Solving The Digital Risk, Resiliency, And Privacy Complexity Problem
Rick Lemieux – DVMS Institute
The following is an excerpt from the DVMS Institute book, A Practitioner’s Guide to Adapting the NIST Cybersecurity Framework published by TSO. You can order the book by visiting https://dvmsinstitute.com/nist-cybersecurity-professional-training-publications/
Complicated is not Complex
To understand complex systems, you must first understand why they aren’t complicated and why they aren’t simple.
Paraphrasing Albert Einstein, there exists a compelling and simple solution for every complex problem that is wrong. It’s not because complex problems are unsolvable; it’s human nature to seek the simplest solution because solving hard problems is hard. Perhaps it’s more of an issue of not understanding the difference between complicated and complex. Let’s start with a simple problem and get that out of the way.
Assume that you don’t know how to cook, but you have someone coming over tonight for dinner, and you want to prepare a great meal. You recall that “there is an app for that.” You install the app and follow the recipe without confusing baking powder with baking soda or tomato paste with tomato sauce. Similarly, you don’t overcook or undercook the pasta, etc.
Following a recipe is a way to solve a simple problem. This approach assumes minimal experience and the ability to read and understand the directions. If this assumption isn’t valid, then the problem isn’t simple. Even so, with practice and experience, an aspiring cook can be generally assured that the resultant meal is not only edible but enjoyable. This approach applies to any process comprised of documented activities.
It gets a bit trickier when things get complicated. Complicated problems differ from simple ones because they require more coordination or specialized knowledge. In addition, some problems are complicated because of their scale.
Consider the example above about cooking pasta. It becomes complicated when we must prepare and serve a pasta dinner for a large catered affair on the condition that it be served hot and al dente. Part of the goal is to ensure everyone gets their food within a short period so that the first person served doesn’t finish their meal before the last person gets theirs – a complicated problem.
Here is another example that addresses a complicated challenge. Post-WWII, Werner von Braun led the Saturn V rocket development, forming the basis for the NASA moon missions. The effort required solving different and related problems by coordinating multidisciplinary specialists to bring together a complicated system of components that sent astronauts to the moon and brought them back alive.
In his article, “Complicated or complex – knowing the difference is important[1],” the author, Will Allen, points out that it’s essential for management teams to understand the difference between complex and complicated. He described the following aspects of how to manage in a complicated environment.
How do you manage in a complicated environment?
- Role defining – setting job and task descriptions
- Decision-making – find the ‘best’ choice.
- Tight structuring – use the chain of command and prioritize or limit simple actions
- Knowing – decide and tell others what to do
- Staying the course – align and maintain focus
The Apollo Program’s Saturn 5 rocket had over 3,000,000 components.
Okay, so what makes complex problems, well, complex?
Complex systems are a bit more “squishy.” Solving a complex problem requires understanding the components and their relationships, how they interact with each other (and other systems), their properties for self-organization, and how they adapt and evolve within the environment in which they exist. It’s this adaptive nature of the system that contributes to its complexity.
“Research into complex systems demonstrates that they cannot be understood solely by simple or complicated approaches to evidence, policy, planning, and management.”[2] Decomposing a complex system and acting on its parts doesn’t work because once isolated from the whole, complex system components behave differently than when connected. Everything we learned in “systems analysis class” works well for understanding complicated systems but doesn’t translate to understanding complex systems. Predicting the weather is complicated; understanding the climate is complex.
Complex systems are adaptive – complex adaptive systems (CAS) exhibit a dynamic network of interactions[3]. This pesky aspect of CAS allows them to defy engineering efforts. Another is that ALL CAS components adapt all of the time. However, if we study the “whole” system and its operation, we might influence its behaviors by implementing well-thought-out and constructive interventions.
The bottom line is that a CAS requires organizational leadership and management to take a different approach. Specifically, the Learning for Sustainability article previously referenced suggests:
- Relationship building – working with patterns of interaction
- Sensemaking – collective interpretation
- Loose coupling – support communities of practice and add more degrees of freedom
- Learning – act/learn/plan at the same time
- Notice emergent directions – building on what works
The difference between a technician and an engineer is that a technician may bend something to make it work, while the engineer will reform it. Perhaps an analogy for complex systems is that a leader won’t try to fix it but will seek to understand it and provide an excellent reason to change its behaviors (and or structure).
In his sequel to his popular TV series Connections, James Burke, a British science historian, introduced The Day the Universe Changed. The TV series revolved around the philosophical idea that the universe only exists as one perceives it through what one knows; therefore, if/when perception changes, this new insight means that the universe has changed (new perception means new reality). We are talking about this because changing the behavior of a complex system is easy; getting the desired behaviors and outcomes is exponentially more difficult.
The “ah-ha” moment in understanding complex systems comes when you know it’s trying to adapt to its environment based on the system’s established rules and goals. Like Hal’s behavior in the book and the movie 2001, a Space Odyssey, rules and goals must align, or you accept the ensuing chaos.
You don’t fix complex adaptive systems, but you coax them into changing their behaviors through a well-thought-out application of leverage. The term “coax” is deliberate; it applies to the context of the organization as a complex adaptive system, not as a method or approach. Getting the necessary buy-in to apply the leverage stick may require organizational change management.
Summary
Solving an organization’s digital risk, resiliency, and privacy complexity problem requires a clear understanding of organizational structures, relationships, dependencies, and culture. Once understood, organizations of any size, scale, and complexity can now focus on building a converged overlay model that facilitates the digital risk, resiliency, and privacy outcomes government regulators expect.
Introducing the DVMS Institute®
Solving The Digital Risk, Resiliency, And Privacy Management Complexity Problem
The landscape of digital outcomes has rapidly evolved, as have the accompanying threats and challenges. The DVMS Institute recognizes these challenges and is committed to reshaping how organizations perceive and manage digital risk, resiliency, and privacy.
The institute’s vision is to serve as that guiding light by teaching organizations of any size, scale, or complexity how to create a digital value overlay system capable of meeting the stringent expectations of both government regulators and operational stakeholders.
As Cloud Services revolutionized the creation and management of digital infrastructure, the DVMS Overlay Model, underpinned by well-known frameworks from NIST and standards from ISO, will revolutionize how organizations manage their digital risk, resiliency, and privacy.
In this rapidly evolving digital world, the DVMS Institute stands at the forefront, ready to guide, educate, and equip. Let’s journey together towards secure, resilient, and auditable digital outcomes
Understanding the DVMS Overlay Model and its Relationship to NIST, ISO, and other Cybersecurity Frameworks
The DVMS Overlay Model enables organizations of any size, scale, and complexity to leverage existing business capabilities and universally recognized frameworks and standards (NIST, ISO, ITSM, GRC) to facilitate the delivery of secure, resilient, and auditable digital outcomes. The following explainer videos will guide you through the specific facets of our comprehensive digital value management system (DVMS™) approach.
This video encapsulates the Institute’s core philosophy. It’s not just about technology; it’s about culture. We advocate for a culture where digital business value creation, protection, and delivery are paramount.
This video is a deep dive into how the institute uses an overlay approach to operationalize and converge universally recognized frameworks like NIST and ISO to deliver the digital outcomes government regulators expect. We believe that a one-size-fits-all solution is often not the answer. Tailoring frameworks to specific needs ensures both security and auditability.
This video describes why digital enterprises are a complex web of operations. The CPD Model breaks down this complexity, ensuring each layer remains secure, resilient, and audit-ready.
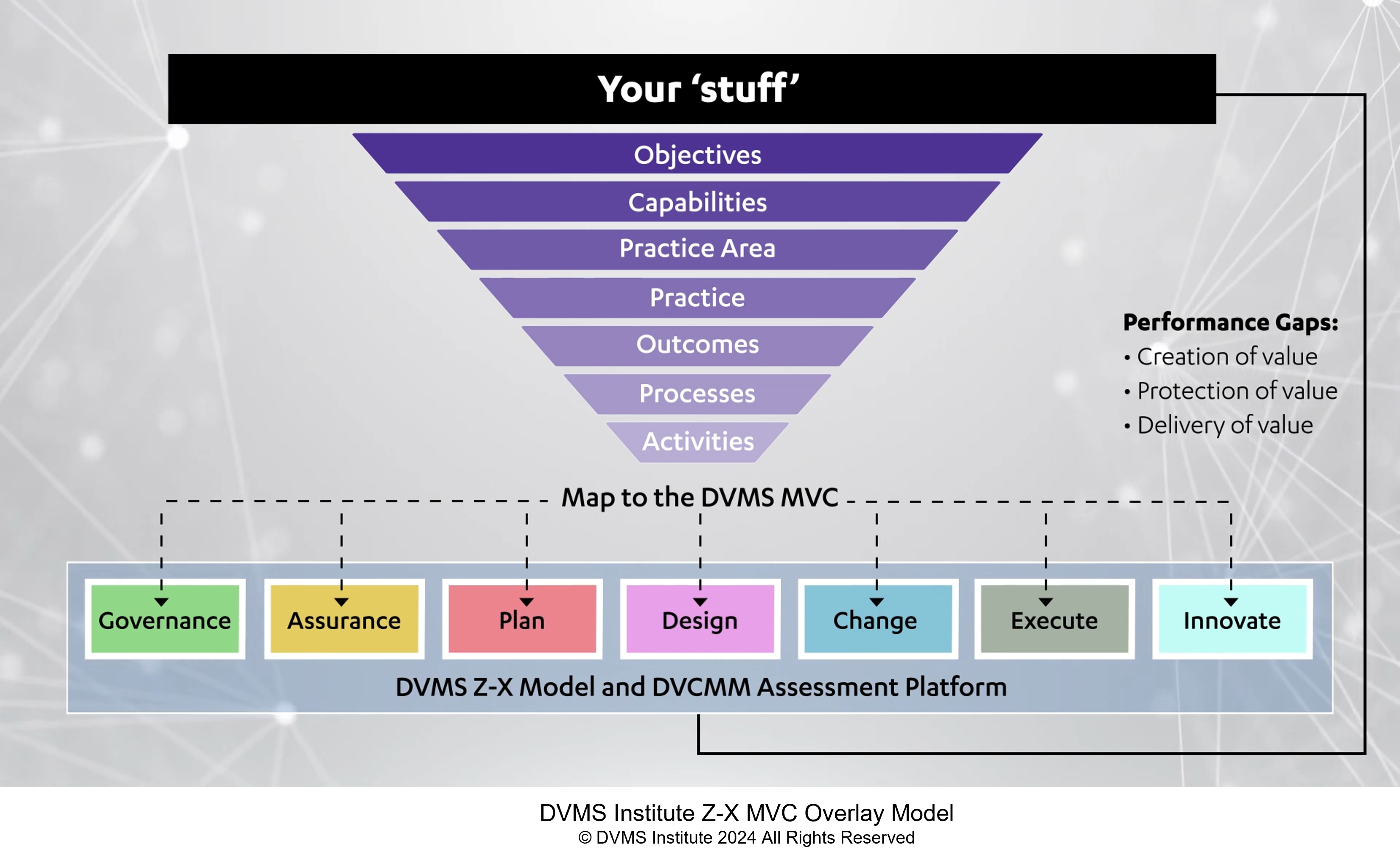
This video describes how the institute’s ZX Model embodies comprehensive planning. From inception to execution, every stage is designed to innovate and support the delivery of secure digital outcomes. It’s a roadmap for organizations to follow.
This video describes why digital outcomes aren’t achieved in isolation. The 3D Knowledge Model fosters communication and collaboration, ensuring that every cog in the organizational machinery works harmoniously by understanding everyone’s role and dependencies in delivering secure digital outcomes.
This video if for those keen on a phased, systematic adoption of these frameworks. The DVMS Fast-Track Model serves as a guide. It emphasizes pace, ensuring digital security and resilience without overwhelming adaptation.
The DVMS Institute Certified Training Programs
All training programs are accredited by APMG International, certified by the National Cybersecurity Council (NCSC) in the UK, and recognized by the U.S. Department of Homeland Security CISA organization as qualified NIST Cybersecurity Framework training in alignment with the cybersecurity roles defined in the NICE Cybersecurity Workforce Framework. A breakdown of the DVMS-accredited training programs:
Digital Business Risk Awareness Training
This course teaches senior leadership, boards, and all employees the fundamentals of digital business, its risks, and WHY organizations of any size, scale, and complexity need to build an overlay model capable of operationalizing any framework (NIST, ISO, COSO, ITSM, GRC, etc.) or standard (ISO) to facilitate secure, resilient, and auditable digital business outcomes.
Foundation Certification Training
This course teaches business leaders and operational stakeholders how to communicate with Leadership and Board Members on WHAT investments must be made to build an overlay model capable of operationalizing any framework (NIST, ISO, COSO, ITSM, GRC, etc.) or standard (ISO) to facilitate secure, resilient, and auditable digital outcomes.
800-53 Practitioner Certification Training
This course teaches digital risk, audit, IT, and cybersecurity practitioners HOW to build an overlay model
capable of operationalizing the NIST Cybersecurity Framework and its NIST 800-53 controls to facilitate
the secure, resilient, and auditable digital outcomes expected by government regulators & operational
stakeholders.
800-171 Specialist Certification Training
This course is an extension to the 800-53 Practitioner Certification Course and is designed to teach 800-53 certified practitioners how to adapt the NIST 800-171 control families in the context of a NIST Cybersecurity Framework program.
ISO 27001 Specialist Certification Training
This course is an extension to the 800-53 Practitioner Certification Course and is designed to teach 800-53 certified practitioners how to adapt the ISO 27001 control families in the context of a NIST Cybersecurity Framework program.
For more information about DVMS Institute® programs please visit www.dvmsinstitute.com or contact support@dvmsinstitute.com
[1] https://learningforsustainability.net/post/complicated-complex/
[2] Ibid.