Why Current Approaches to Cyber Risk Management Fail
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Cybersecurity, once a peripheral concern, is now a paramount business imperative. Yet, despite the escalating threats and mounting losses, conventional cybersecurity risk management (CSRM) approaches need to be revised. This paper will delve into the fundamental shortcomings of these methods, highlighting their inability to mitigate risk effectively in the ever-evolving cyber threat landscape.
One of the most critical flaws in CSRM is its reactive nature. Traditional approaches often focus on responding to threats after they have materialized rather than proactively preventing them. This reactive stance is primarily due to the reliance on outdated risk assessment methodologies that need to be revised to keep pace with the rapidly changing threat landscape. Risk assessments are often static, conducted annually or biannually, rendering them obsolete before implementation. When a risk is identified and mitigated, the threat landscape has shifted, leaving organizations vulnerable to new and emerging attacks.
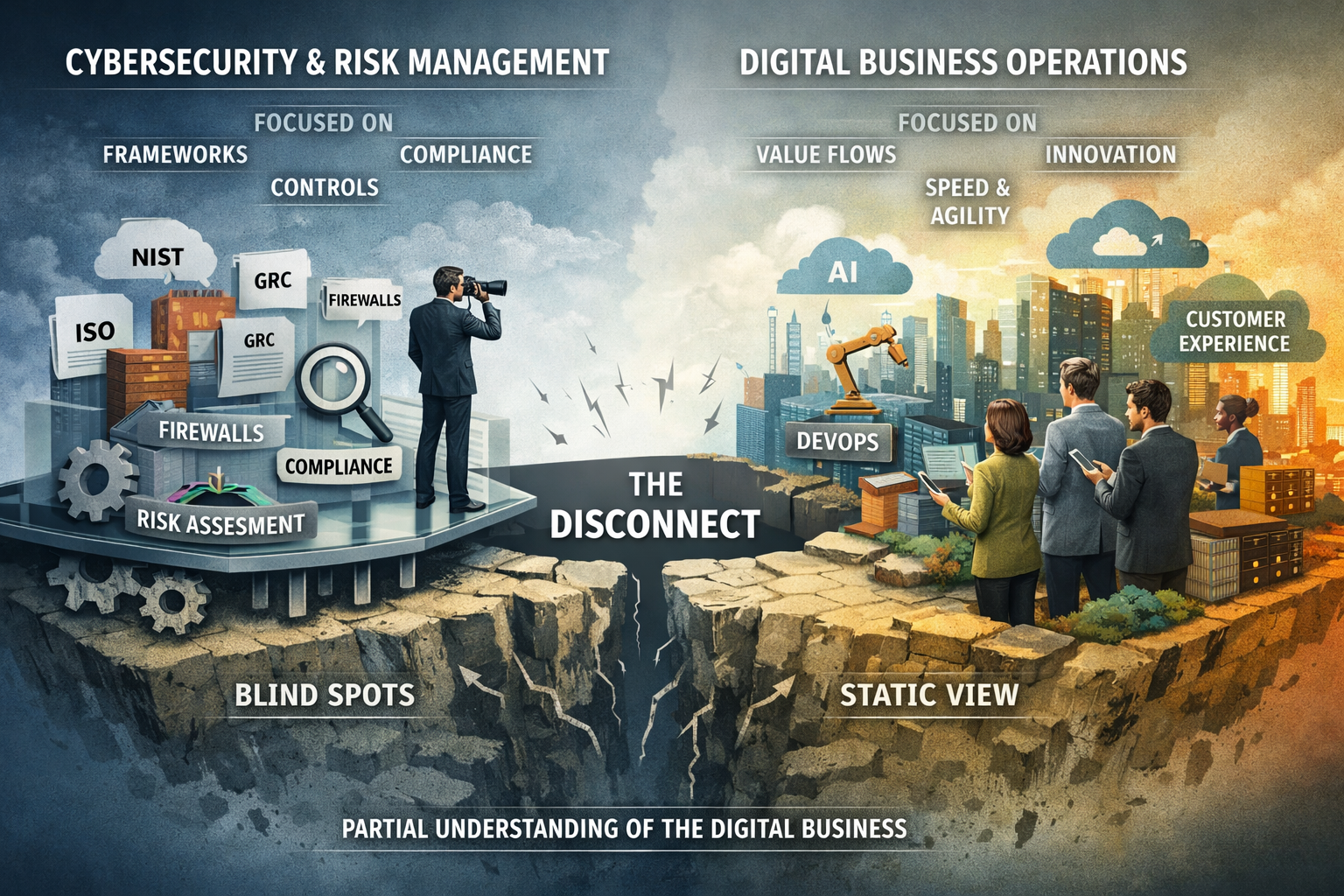
Moreover, CSRM frequently adopts a siloed approach to security, treating it as an isolated function rather than an integral part of the business. This compartmentalization hinders effective risk management by preventing a holistic view of the overall security posture of the organization. Security teams often operate in isolation, needing more visibility into the broader business context and the potential impact of cyber incidents on critical operations. This siloed perspective can lead to suboptimal decision-making and missed opportunities to identify and address emerging risks.
Another significant challenge is the overreliance on technology as a panacea for cybersecurity problems. While technology is undoubtedly a crucial component of any robust security strategy, it is not a silver bullet. Many organizations invest heavily in the latest security tools and technologies without considering the human element. Phishing attacks, social engineering, and insider threats are significant contributors to breaches, highlighting the importance of employee training on the fundamentals of digital business, its risks, and the role everyone plays in mitigating cyber risks. Even the most sophisticated technological defenses can be circumvented without a strong human component.
Furthermore, CSRM often struggles to quantify and communicate risk effectively to senior management. Security risks are complex and multifaceted, making them difficult to translate into financial terms that resonate with business leaders. As a result, cybersecurity initiatives are frequently underfunded and prioritized lower than other business objectives. Without a clear understanding of the potential financial impact of cyber incidents, organizations are less likely to invest the necessary resources to protect their assets.
Finally, the regulatory landscape surrounding cybersecurity is constantly evolving, adding complexity to risk management efforts. Organizations must comply with a patchwork of overlapping regulations, each with its requirements and standards. This regulatory burden can divert resources from core security activities and create employee compliance fatigue. Additionally, the rapid pace of regulatory change can make it challenging for organizations to stay up-to-date and ensure ongoing compliance.
Current approaches to cybersecurity risk management are failing in the face of increasingly sophisticated and persistent threats. The reactive nature of these methods, coupled with a siloed approach, overreliance on technology, ineffective risk communication, and the complexities of the regulatory environment, creates a perfect storm for cyberattacks.
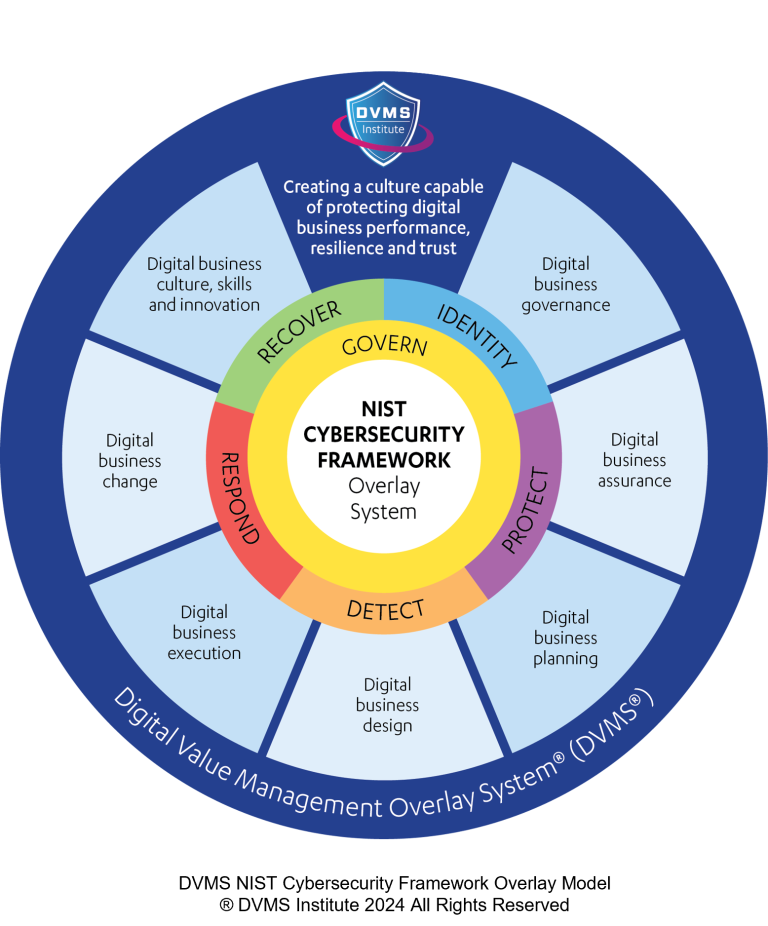
To effectively mitigate cyber risks, organizations must adopt a more proactive, holistic, and adaptive overlay approach that integrates cyber risk management into an organization’s core business strategy. This new approach must result in a culture capable of mitigating cyber risks to protect digital business performance, resilience, and client trust.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
The DVMS Institute teaches organizations of any size, scale, or complexity an affordable approach to mitigating cyber risk to protect digital business performance, resilience, and trust.
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
® DVMS Institute 2024 All Rights Reserved