How The NIST-CSF-DVMS and Secure Controls Framework (SCF) Work Together To Enable Regulatory and Maturity Model Outcomes
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
The DVMS Institute’s NIST Cybersecurity Framework Digital Value Management System® (DVMS) and the Secure Controls Framework (SCF) represent comprehensive approaches to cybersecurity, risk management, and digital value assurance. However, while they share common goals—such as enabling organizations to build secure, compliant, and resilient digital environments—they diverge significantly in philosophy, structure, scope, and practical application.
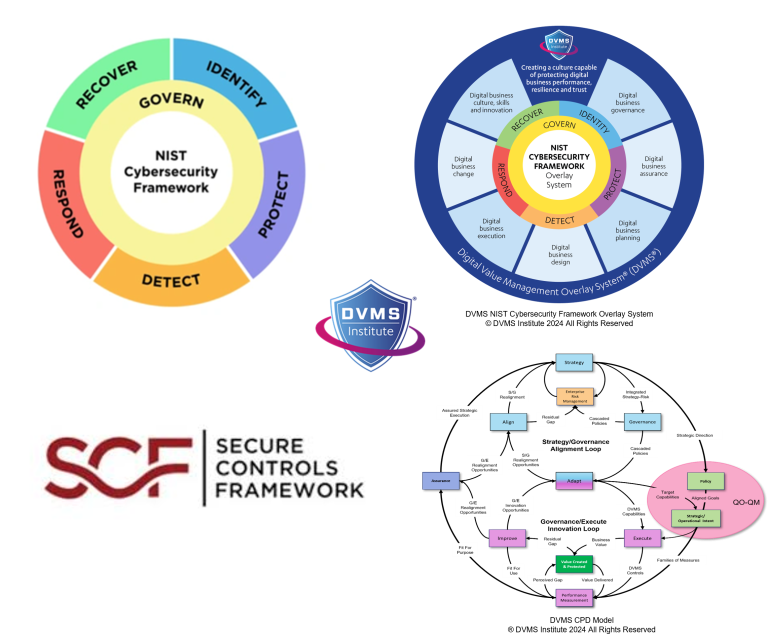
The DVMS, rooted in the NIST Cybersecurity Framework (CSF) and enhanced through systems thinking and cultural adaptation, is designed as a control mechanism and a strategic governance overlay. In contrast, the SCF is a control-centric, requirements-driven framework that maps across numerous compliance regimes to provide prescriptive controls for building secure systems. Understanding how these frameworks compare reveals their complementary potential and highlights why organizations seeking cyber-resilient operations rather than just static compliance might add DVMS to their program.
At a foundational level, the SCF is a catalog of cybersecurity and privacy controls mapped against over 100 statutory, regulatory, and contractual frameworks. It provides detailed, prescriptive language for how organizations should implement controls across 32 domains—from access control and cryptographic protections to business continuity and data classification. These controls are designed to be measurable, mappable, and aligned with industry-standard frameworks such as ISO 27001, NIST SP 800-53, GDPR, and HIPAA. In this sense, SCF is a comprehensive control repository—a “Rosetta Stone” of cybersecurity compliance. It benefits organizations operating in regulated industries or those required to demonstrate conformance across multiple jurisdictions.
By contrast, the DVMS is not a control library but a systems-based management overlay designed to help organizations create, protect, and deliver digital business value within complex and dynamic ecosystems. Rather than prescribing technical controls, the DVMS focuses on embedding cybersecurity as a governance, culture, and operational capability. It integrates the six Functions of the NIST CSF (Govern, Identify, Protect, Detect, Respond, Recover) with the DVMS Institute’s original models—the CPD Model and the Z-X Model. These models provide a strategic and operational map that aligns digital value creation with cybersecurity and resilience outcomes.
One of the key differences lies in the philosophical approach. The SCF is fundamentally compliance-oriented. Its value proposition is to help organizations “check every box” across disparate compliance requirements harmoniously and unify. Organizations implementing the SCF typically begin with a gap analysis: determining which controls apply, which are missing, and how to remediate the gaps. The outcome is usually a highly detailed compliance posture, suitable for audits, attestations, and third-party assessments. While this is effective for demonstrating conformance, it can lead to a checklist mentality, where controls are implemented without broader consideration of how they interact with strategy, culture, and evolving business goals.
The DVMS takes a systems thinking approach. Rather than starting with compliance requirements, it begins by asking: What digital value are we trying to create, protect, and deliver? From there, the organization maps its existing capabilities to the seven DVMS minimum viable capabilities: Govern, Assure, Plan, Design, Change, Execute, and Innovate. This layered approach acknowledges that organizations operate as complex adaptive systems and that linear control models often fail to account for emergent behaviors, cultural inertia, and unforeseen vulnerabilities. The DVMS provides a lens through which these systemic realities can be seen, understood, and addressed.
Culturally, the SCF is technocratic. It is designed for cybersecurity professionals, auditors, and compliance officers who need clarity, specificity, and traceability in control implementation. Its structure assumes that roles and responsibilities are already established, and that the enterprise is ready to align controls with them. This can work well in mature security programs but poses challenges for organizations that lack centralized governance or cross-functional collaboration.
The DVMS, in contrast, emphasizes organizational learning, cross-functional coordination, and cultural evolution. It explicitly addresses that most cybersecurity failures are not technical, but organizational. For example, the “Thriving on the Edge of Chaos” publication underscores the need for leaders to understand mental models, feedback loops, and human behavior as part of any security transformation. The DVMS doesn’t assume maturity—it enables it by helping organizations build cultural and structural capacity through phased adoption using the DVMS FastTrack approach (Initiate, Basic Hygiene, Expand, Innovate). This phased approach makes the DVMS accessible to organizations undergoing transformation, digital modernization, or restructuring.
Another key distinction is how the two frameworks handle metrics and outcomes. The SCF focuses on control-level implementation and audit readiness, meaning its measurement systems are inherently binary or maturity-based (e.g., control implemented: yes/no, or control maturity: 1–5). It provides clear evidence paths for compliance but does not inherently connect these measurements to business value, resilience, or adaptability.
In contrast, the DVMS applies GQM (Goal-Question-Metric) and QO–QM (Question Outcome–Question Metric) models that force organizations to tie metrics to strategic outcomes. For example, rather than asking whether a logging control is in place, DVMS would prompt the question: “How does our incident response capability protect the digital value created by our ERP system?” From there, metrics are developed to validate implementation and effectiveness. This approach results in more meaningful measurement, especially in board-level conversations where business leaders need to understand the ROI and impact of cybersecurity investments.
Both solutions provide value in supply chain and third-party risk, but in different ways. The SCF includes dedicated controls for vendor risk management, making it easy to operationalize due diligence and third-party oversight across compliance regimes.
The DVMS, meanwhile, contextualizes third-party relationships as interdependencies within a larger system. Rather than focusing solely on vendor controls, it encourages organizations to understand how third-party failures impact digital value chains and develop resilience strategies accordingly. This includes creating Community Profiles, which serve as shared baselines of security expectations across a digital ecosystem—something that could be highly valuable in sectors such as healthcare, finance, or government.
The scalability and flexibility of each framework also differ. The SCF is designed to be modular and highly granular. Organizations can pick and choose controls based on scope and applicability. However, it can become unwieldy without strategic integration, particularly for smaller organizations or those without mature GRC tooling. The DVMS is intentionally an overlay, meaning it can be applied on top of existing standards, including the SCF, to identify performance gaps, streamline governance, and guide transformation. Its strength lies in its ability to harmonize diverse practices through a strategic, outcome-oriented lens, rather than adding another layer of detailed requirements.
In practice, these frameworks are not mutually exclusive. They can be highly complementary. Organizations may use the SCF as a foundation for control implementation and audit preparation, leveraging the DVMS to ensure those controls are contextually appropriate, strategically aligned, and operationally effective. For instance, a global manufacturer might use the SCF to implement uniform controls across its IT, OT, and supply chain environments while using DVMS to monitor whether those controls protect critical digital value and enable resilience in geopolitical instability.
The DVMS and the SCF represent two distinct, but overlapping approaches to cybersecurity and risk management. The SCF offers breadth and precision in control implementation, while the DVMS provides depth in governance, culture, and strategic alignment. Where the SCF excels at doing things right, the DVMS ensures the organization is doing the right things—and doing them in a way that enables resilience, adaptability, and sustained digital business value. Combining both frameworks may offer the most robust path forward for organizations navigating complex digital ecosystems, regulatory landscapes, and rapidly changing threats.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
DVMS Institute is a renowned provider of accredited (APMG International), Assured (NCSC-GCHQ-UK), and Recognized (DHS-CISA-NICCS-USA) NIST Cybersecurity Framework, Digital Value Management System® body of knowledge publications, certification trainings, assessment platforms and real-life desktop simulation trainings.
The Institute’s NIST Cybersecurity Framework Digital Value Management System® certified training programs teach businesses of any size, scale, or complexity the skills to build a Holistic, Adaptive, and Culture-Powered Overlay System capable of anticipating and mitigating the systemic risk that will impact organizational cyber resilience.
By embedding systemic risk management into strategic decision-making and aligning it with employee cultural values, organizations can build resilience—a dynamic capability to withstand digital business disruption and comply with any cybersecurity regulation (SEC, UK, DORA, NIS2, SAMA, SOCI, IMO, etc.) or maturity model mandates (HITRUST, CMMC, C2M2 etc.).
® DVMS Institute 2024 All Rights Reserved