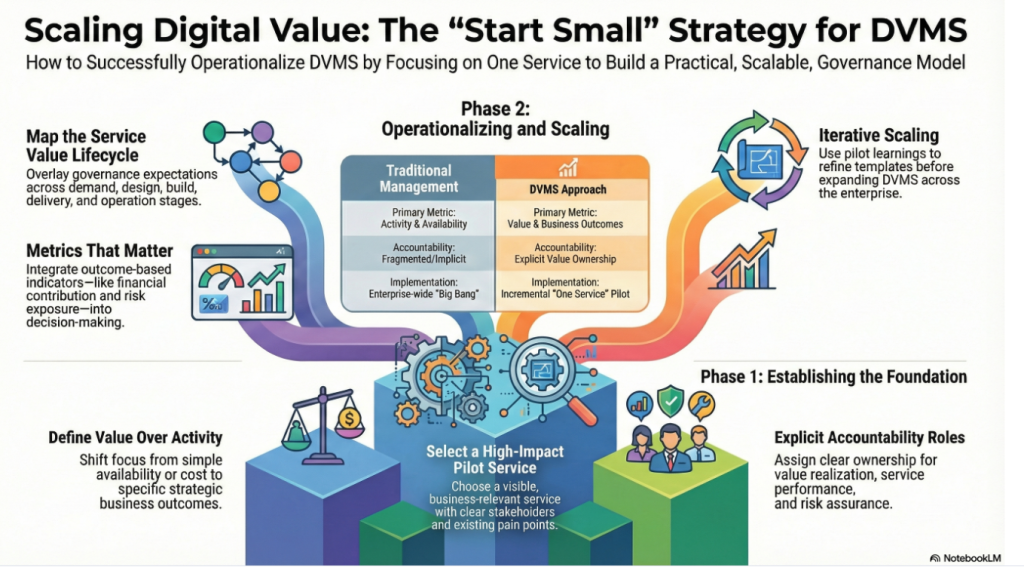
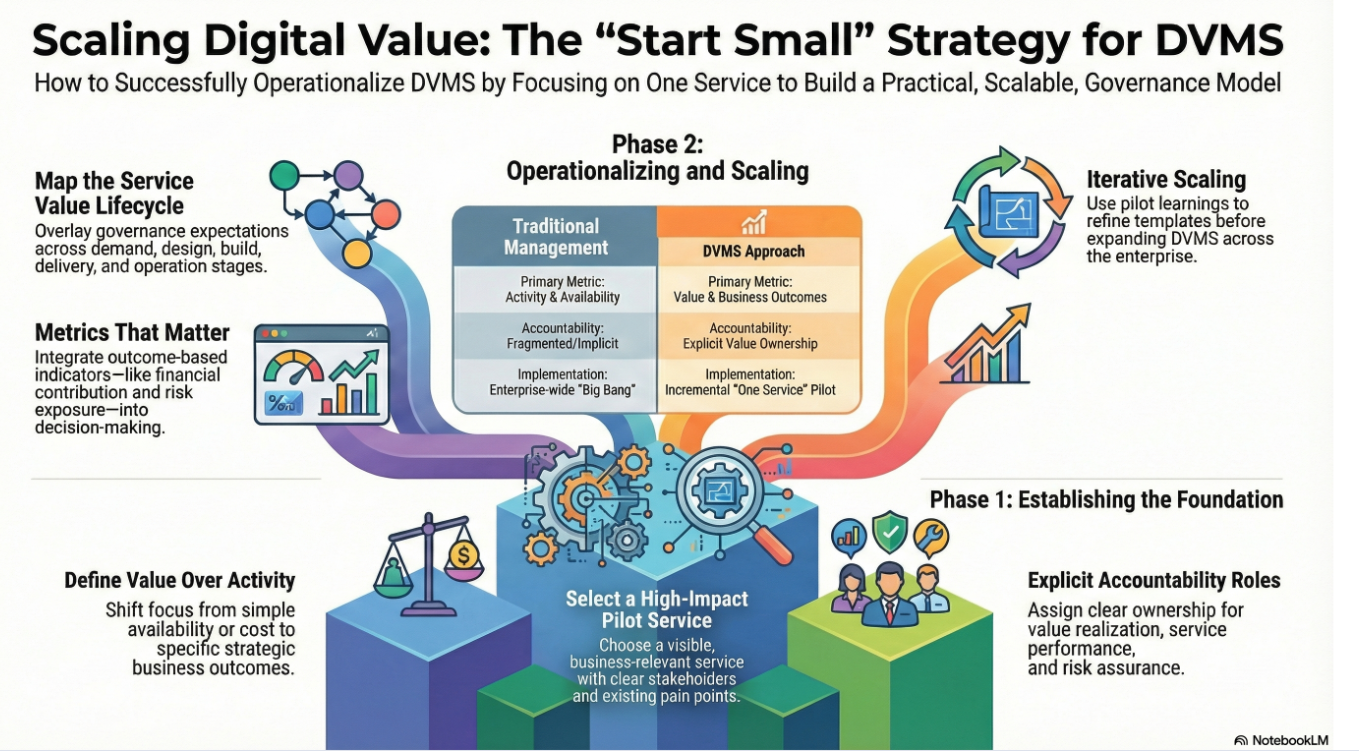
Governance is Boundary Setting, Not Policy Writing – The GRAA Management Series Part 1
David Nichols – Co-Founder and Executive Director of the DVMS Institute
Most managers I know do not dislike governance. What they dislike is governance that only exists on paper, governance that shows up late, and governance that becomes visible only after something goes wrong.
If you have ever sat in a post-incident review and heard, “But the policy says…”, you already know the gap. Policies are important. They clarify intent, obligations, and standards. They also do not run your operation.
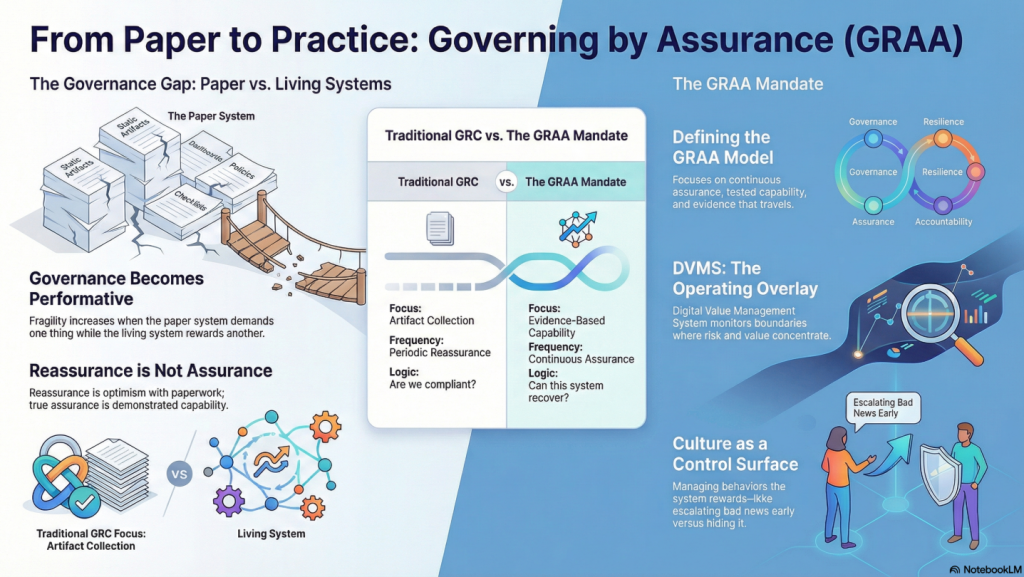
Managers run operations. We do it with imperfect information, shifting priorities, and real constraints, and we do it in an environment where yesterday’s “normal” is rarely today’s. That is why, in the GRAA Leadership Series – Part One, “Why Our GRC Investments Aren’t Delivering Resilience… and Everyone Feels It,” the key point is not that GRC is wrong. It is that we all feel the difference between artifacts that look mature and a system that behaves resiliently. That difference is what creates the frustration.
This management series is about closing that gap, without throwing anything away. You still need controls. You still need audits. You still need risk registers, exception processes, and evidence to satisfy regulators, customers, and boards. The shift is not “GRC vs operations.” The shift is from treating governance as a set of documents to treating it as boundary-setting, allowing managers to execute it in real time and produce evidence from actual work.
In the GRAA Leadership Series – Part Two, “Your Organization Doesn’t Have a Framework Problem: It Has an Overlay Problem,” the message is that most enterprises are stacking frameworks rather than integrating with the operating reality. You can retain the frameworks and maintain the audit discipline. What you cannot keep is the assumption that documentation alone will drive behavior at the edge of chaos, where decisions actually happen.
This is where the DVMS approach becomes essential for managers. It takes the abstract idea of “governance” and anchors it to how the work flows through Create, Protect, and Deliver. It turns governance into something you can run, not just reference.
The manager’s definition of governance
If you ask ten managers to define governance, you will get ten versions of the same thing: “How we decide, what we are allowed to do, who decides when it gets hard, and what happens when we are wrong.” That is the most practical definition I have found, because it is operational.
Governance, in management terms, is the set of boundaries that keep the organization aligned while still moving forward. It is about creating speed without losing control. When governance is healthy, it serves three key purposes for managers.
First, it reduces ambiguity. It makes decision rights clear, especially in the moments that matter. Second, it sets tolerances, so teams know the difference between normal variance and a condition that must trigger escalation. Third, it creates coherence across functions, so delivery teams, security teams, risk teams, and audit teams are operating inside the same model of “what good looks like.”
When governance is weak, managers see the opposite. Decision rights are vague. Escalation is political. Tolerances are implied, or they exist only in continuity documents that nobody rehearses. Evidence becomes a scramble because no one is sure what “proof” looks like until a stakeholder asks for it at the worst possible time.
From my perspective, the goal of governance is not to produce more artifacts; rather, it is to ensure that existing artifacts are practical and effective. The goal is to create bounded autonomy, allowing work to proceed at speed while adhering to constraints, making traceable decisions, and providing evidence that can withstand scrutiny. That is the shift this article is about.
Boundaries beat policies, because boundaries are executable
Policies matter. They set expectations. They provide legitimacy, especially when you need to say “no.” They also tend to be general. Managers need something more concrete. Boundaries are the operational form of governance. They translate intent into execution. Here are the boundary types that consistently show up in resilient operations.
One is outcome tolerances. This is where the conversation moves from “Are we compliant?” to “What outcome are we protecting, and how much variance can we accept before we must change behavior?” Outcome tolerances can include time (the duration during which the service can be degraded), integrity (the amount of data loss or corruption that is unacceptable), safety (the events that must never occur), financial exposure, customer harm, and legal or contractual thresholds. The exact categories vary by industry, but the idea stays the same. Tolerances define the edge of acceptable performance.
Another boundary type is decision rights. Most outages do not become crises because something failed. They become crises because no one is sure who can authorize the next move, or because the person who can approve it is not informed quickly enough.
The third boundary type is escalation triggers. Escalation should not depend on personality, confidence, or politics. Conditions should trigger it. If a tolerance is threatened, escalation is not optional; it is the designed behavior of the system.
A fourth boundary type is pre-authorized actions. If you wait to negotiate authority during a disruption, you are burning time and trust. Pre-authorized actions define what teams are allowed to do within a specified tolerance envelope, eliminating the need for a meeting.
The final boundary type, and one that managers often overlook until late, is evidence expectations. Not “What report do we file?” but “What proof do we maintain as we operate?” Evidence is what makes governance real. Evidence is what allows leaders to delegate with confidence. Evidence is what makes audits less of a paper chase, because it links artifacts to actual behavior.
This is a good point to say what this is not. This is not anti-GRC. It is the operationalization of GRC. It is how you take governance intent and make it executable at the boundary, where managers live.
DVMS makes boundary setting practical because it runs on Create, Protect, Deliver
One reason governance becomes abstract is that it is often discussed “above” the work. DVMS fixes that by tying governance to the flow of work. In DVMS terms, Create, Protect, and Deliver are not departments; instead, they are key functions. They are operating modes that every value stream moves through. That matters for managers because it prevents the classic pattern where governance is written by one group, another interprets risk, and delivery is left to translate both, under time pressure.
If you apply boundary thinking across Create, Protect, and Deliver, governance becomes concrete.
In Create, boundaries clarify what outcomes matter, what trade-offs are acceptable, and what “success” means in observable terms. This is where managers can push for clarity: what are we optimizing, and what are we refusing to sacrifice?
In Protect, boundaries clarify unacceptable harm, constraints, and risk thresholds, including when to stop the line. Protect is not “the security team’s job.” Protect is the set of conditions that should change behavior across the whole value stream.
In Deliver, boundaries clarify operating behaviors. How will we degrade? How will we recover? What gets restored first? What do we verify before we declare “back to normal?” This is where governance becomes real, because delivery is where the consequences show up.
If you have read Thriving on the Edge of Chaos: Managing at the Intersection of Value and Risk in the Digital Era, you will recognize the theme. The Thriving book argues, in practical terms, that value and risk are inseparable in the digital era. Managers feel that every day. DVMS gives you a way to run it.
The Boundary Card, a tool managers can actually use
Most teams do not need another framework presentation. They need a shared object that enables governance to be portable.
A simple technique I have used, and seen work well across different types of organizations, is what I call a Boundary Card. It is one page. It can be a page in a platform, a living document, or a template. The medium matters less than the discipline.
A Boundary Card answers five questions:
- What is the outcome? Name it in business language, not system language.
- What are the tolerances? Define what “acceptable variance” looks like, and define the thresholds that trigger a behavior change.
- Who has decision-making rights, and for what purposes? Be explicit about who can pause, degrade, recover, and accept exceptions, within what conditions.
- What are the escalation triggers? Define the conditions that require escalation and outline the corresponding path.
- What evidence do we maintain? Define what proof exists that we are inside boundaries, or that we recovered in a disciplined way.
If you do this well, you gain something significant. You reduce the number of decisions that require executive involvement because you have created bounded autonomy. You also increase the quality of the escalations that do happen, as they are grounded in tolerances and evidence, rather than emotion and guesswork.
A manager scenario: the difference between “policy compliance” and “boundary execution.”
Imagine a business service with strong documentation. It has policies, procedures, a disaster recovery plan, and a control mapping. It passes audits.
Then a dependency fails. It could be a supplier, a shared platform, or a central service, such as an identity management system. Your teams have workarounds, but they are not sure they are allowed to use them. The risk team is not sure whether the workaround violates a policy. The delivery team is not sure whether leadership will support the decision. Everyone slows down, and the outage lasts longer than it needs to.
Nothing in that story is unusual. It is a normal outcome of governance designed as documentation, not as executable boundaries. Now imagine the same service with a Boundary Card and a rehearsal discipline. The tolerances are precise. The decision rights are clear. The escalation triggers are clear. The evidence expectations are clear.
The team degrades in a controlled manner within tolerance. They execute a pre-authorized workaround. They escalate when a tolerance threshold is approached, not when someone panics. They record the rationale for their decision and capture evidence as they go. When leaders ask, “Why did you choose this path?” the answer is immediate because it is already linked to boundaries.
That is what operational governance looks like. It does not eliminate incidents. It reduces chaos. It shortens the time to a decision. It improves recovery predictability. It provides evidence that withstands scrutiny.
Here is the part managers should appreciate. This discipline makes audits easier, not harder. Instead of hunting for artifacts that “prove” you are in control, you point to operational evidence that shows how control behaved when reality showed up. Evidence trumps artifacts, not because artifacts are useless, but because artifacts without evidence do not establish trust.
How does this help managers without creating more overhead
It is fair to ask, “Isn’t this just more work?” It can be, if you make it bureaucratic. The point is to simplify. If a Boundary Card takes two months, it is the wrong tool. If it takes a manager and a cross-functional group a couple of sessions to get to a usable first version, it is doing its job.
The Boundary Card is not about perfection. It is about clarity. Start with one service or one value stream that matters and avoid trying to model the entire enterprise. Define tolerances that reflect reality, not wishful thinking. If your service cannot survive four hours of disruption, do not pretend it can. If the business cannot tolerate two hours, that is not a documentation problem; it is a capability gap, and that gap is now visible.
Clarify decision rights and escalation triggers. Be honest about where decisions currently get stuck and fix those chokepoints. Then define the minimum evidence set. Make it small and operational. Evidence should come from regular work, not from a quarterly scramble.
If you do those things, you will immediately benefit as a manager. You receive faster decisions, fewer unexpected escalations, and more transparent conversations with risk and audit partners. You also get a cleaner story upward, because leadership can see how governance is being executed at the edge.
The leadership-manager handshake
This is where the two series become complementary. The leadership series is establishing a paradigm shift, from static, artifact-centered governance to evidence-centered operational governance, from stacking frameworks to overlaying them with a system model, and from dashboards to understanding how the system behaves.
The management series is helping to establish that paradigm in the places where managers live. Leaders can set intent, tolerances, and expectations. Managers can operationalize that intent through clear boundaries, defined decision rights, established escalation triggers, and established evidence routines. When both are aligned, governance stops being something that “gets in the way” and becomes something that enables delivery.
This is the handshake worth aiming for. It respects the purpose of GRC and audit, while addressing the gap that both managers and leaders feel between paper maturity and operational resilience.
What to do before the following incident
If you are a manager reading this, here is a reasonable next step that does not require a program. Pick one critical outcome your team supports. Write a first Boundary Card draft. Keep it simple. Bring in the right cross-functional partners, including the risk or security lead who will support your decisions, and the operations lead who will execute them. Agree on tolerances, decision rights, escalation triggers, and the minimum evidence set.
Then run one short rehearsal, even if it is a tabletop. Focus on the boundaries. Ask, “When do we degrade? Who authorizes it? What triggers escalation? What evidence do we capture while we operate?” You will learn more in that hour than you will learn in a month of document review.
In Part Two – Resilience Is Designed into Daily Delivery, we will discuss why resilience is built into daily delivery, rather than being added after the fact, and how managers can develop and recover behaviors that are both operationally realistic and auditable through evidence.
About the Author

Dave is the Executive Director of the DVMS Institute.
Dave spent his “formative years” on US Navy submarines. There, he learned complex systems, functioning in high-performance teams, and what it takes to be an exceptional leader. He took those skills into civilian life and built a successful career leading high-performance teams in software development and information service delivery.
DVMS Institute Cyber Resilience Certified Training
Learn to Build a DVMS Governance System for Resilient, Assured and Accountable Digital Value Outcomes
Watch a Quick Paper to Practice Explainer Video
Despite abundant frameworks and dashboards, leaders still struggle to see how digital value streams actually perform under real-world stress.
Intent, structure, and day-to-day behavior are examined in isolation, creating flat views that hide how decisions and human responses interact in a living digital system.
The result is governance that appears robust on paper but breaks down in execution, forcing leaders to manage fragmented controls rather than assure and account for resilient, system-level performance
The Assurance Mandate White Paper Series
Watch a Quick Assurance Mandate Explainer Video
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
The Assurance Mandate Paper explains why traditional GRC artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
The Digital Value Management System® (DVMS)
Watch a Quick DVMS Explainer Video
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to easily integrate fragmented frameworks and systems such as NISTCSF, GRC, ITSM, and AI into a unified, culture-driven governance and assurance system that enables organizations to manage the resilience of their living digital system by :
- Enabling Adaptive Governance through risk-informed decision-making
- Sustaining Operational Resilience through a proactive and adaptive culture
- Measuring Performance Assurance through evidence-based outcomes
- Ensuring Visible Accountability by making intent, execution, and evidence inseparable
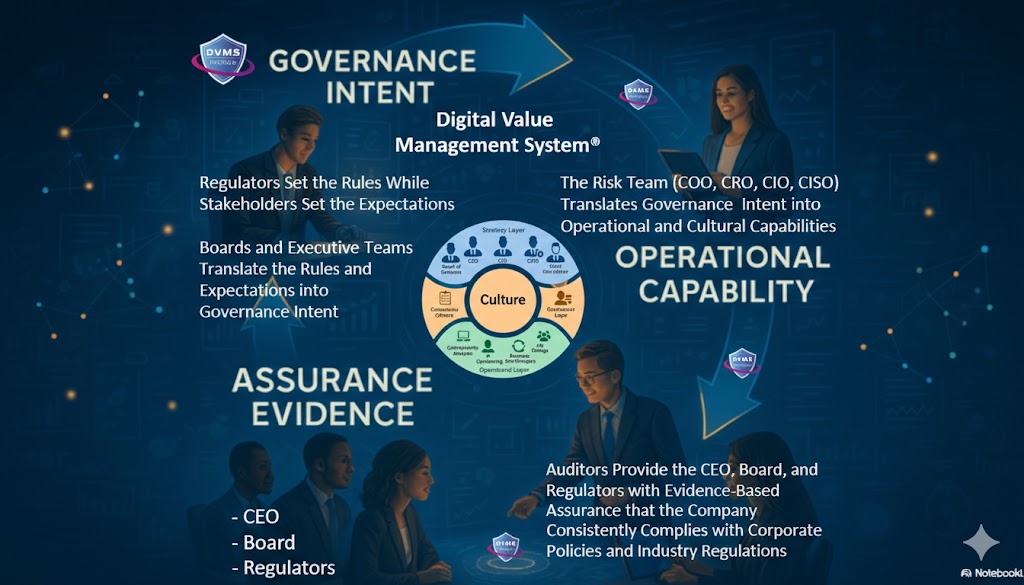
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business actually performs
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Outcomes – that align people, decisions, and behaviors
Through its MVC, CPD, 3D Knowledge, and FastTrack Models, a DVMS turns this integration into three distinctive capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance—across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
The DVMS Team
Watch a Quick DVMS Explainer Video
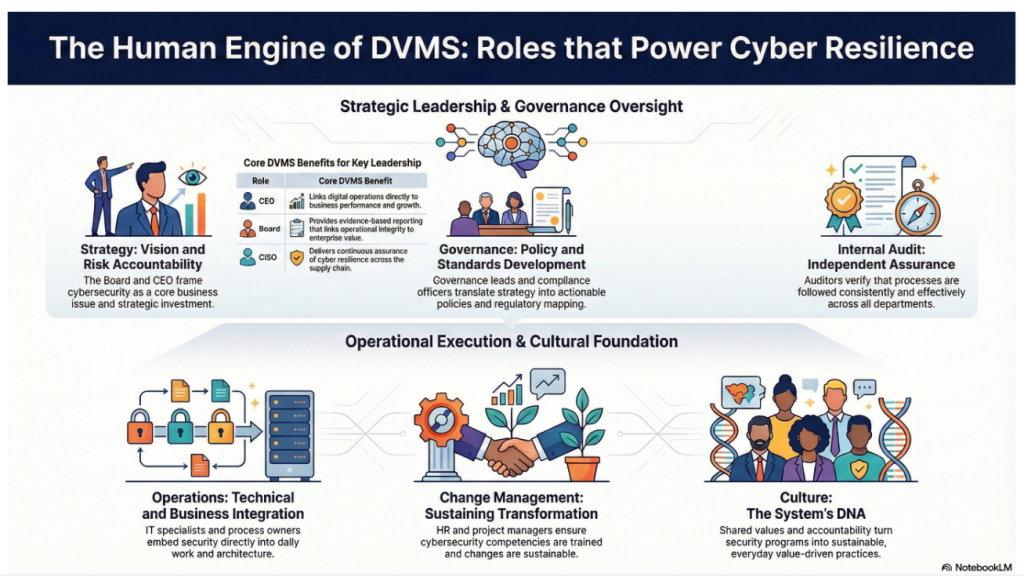
Delivering the outcomes of the DVMS integrated with the NIST CSF, ITSM, GRC, and AI systems requires coordinated action across an enterprise’s strategy, governance, and operational layers.
Each of these business layers contains unique roles that, when aligned and functioning cohesively, enable the organization to protect digital assets and adaptively manage digital business risks while delivering sustained digital value and resilience.
Together, these roles create an adaptive, risk-informed, and resilient organization capable of thriving in a complex, volatile digital environment.
The DVMS Training Pathway to Operational Resilience
Watch a Quick DVMS Training Explainer Video
The DVMS Institute’s certification training programs and publications equip leaders, practitioners, and organizations to govern operational cyber-resilience through an evidence-based system that assures and accounts for digital value outcomes.
Grounded in real-world governance challenges and aligned to NIST CSF 2.0, DVMS Institute offerings go beyond frameworks and compliance checklists to build measurable capability, clear accountability, and defensible confidence in decision-making.
Through structured learning, applied certification, and authoritative publications, the Institute advances a disciplined, outcome-driven approach to managing digital risk, performance, and resilience as an integrated system.
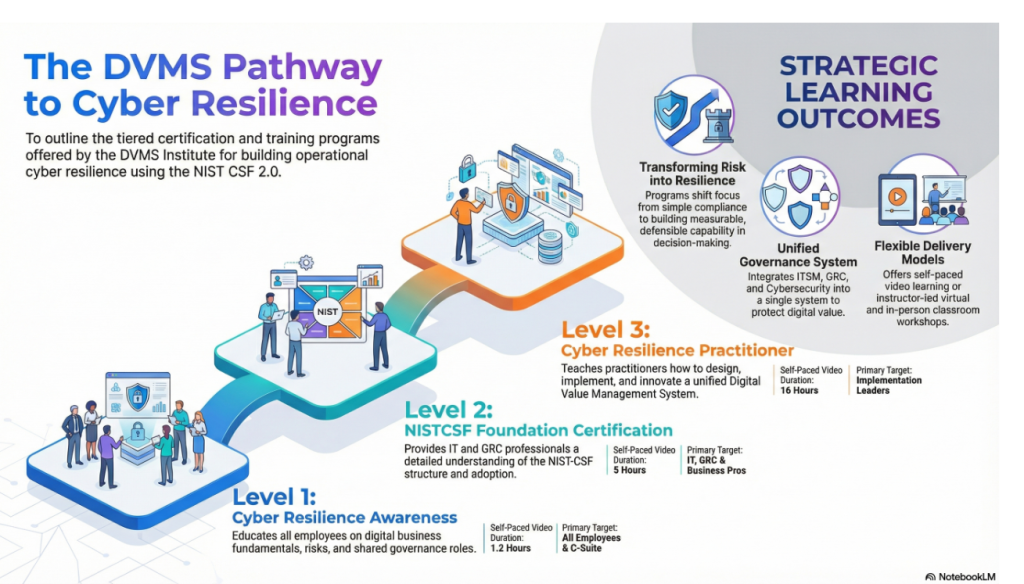
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters a culture that is prepared to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS NISTCSF Foundation Certification Training
The DVMS NISTCSF Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters IT, GRC, Cybersecurity, and Business professionals with the skills to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
This investment fosters IT, GRC, Cybersecurity, and Business practitioners with the skills to assess, design, implement, operationalize, and continually innovate a Digital Value Management System® program that operationalizes a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
A FastTrack Approach to Launching A DVMS Program
Watch a Quick DVMS FastTrack Explainer Video
The DVMS FastTrack Model is a phased, iterative approach that helps organizations adopt and mature their Digital Value Management System over time, rather than trying to do everything simultaneously. This approach breaks the DVMS journey into manageable phases of success.
DVMS Organizational Benefits
Instead of replacing existing operational frameworks, the DVMS elevates them—connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
By adopting a DVMS, organizations are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Leadership Benefits
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors: an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved