When One CISO Isn’t Enough: How the DVMS Unifies Microsoft’s 14-Role Security Model
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Introduction
In recent years, the role of the Chief Information Security Officer (CISO) has grown dramatically in scope and complexity. As cyber threats escalate, regulatory demands intensify, and digital business models evolve, many organizations are finding that a single CISO can no longer keep pace.
Microsoft’s decision to appoint multiple Deputy CISOs—14 in total—each aligned to specific domains of the business, product, and engineering, serves as one high-profile case in point. This transformation signals a more profound shift in how security, risk, governance, and assurance must be embedded across enterprise operations.
A Digital Value Management System (DVMS) is uniquely positioned to respond to and anchor this evolution—by providing an integrated intelligence system that spans governance intent, operational capability, and assurance evidence.
In this essay, we examine how the DVMS framework addresses the challenges posed by a distributed CISO model, including clarifying roles and accountability, unifying domain-specific efforts, enabling measurable resilience and trust, and transforming fragmented programs into cohesive systems.
The Changing CISO Landscape at Microsoft
Historically, the CISO role has been a broad-spectrum leadership position, encompassing the definition of cybersecurity strategy, oversight of controls, management of incident response, ensuring compliance, and reporting to the board.
Yet, organizations like Microsoft have recognized that this breadth is unsustainable at large scale. In 2024 and 2025, Microsoft introduced a Deputy CISO (dCISO) strategy, appointing 14 specialists responsible for discrete domains—for example, identity and access, engineering systems, AI risk, product security, customer outreach—with each reporting to the corporate CISO and, in many cases, to a relevant business or product leader.
The rationale is compelling: one individual cannot be a domain expert, strategy leader, board advisor, compliance overseer, product partner, and operational commander all at once. As one Microsoft dCISO put it: “It’s just not humanly possible.” Splitting the role enables domain-specific accountability, more profound expertise, closer alignment with business units, and faster operational feedback loops.
However, it also raises significant governance challenges, including ensuring coherence across domains, maintaining a unified risk posture, aligning with business strategy, and generating assurance consistent with board and regulatory requirements.
How a DVMS Anchors Governance in a Distributed CISO Model
Governance Intent: Creating the Shared North Star
With multiple dCISOs, each domain leader may interpret priorities differently—identity security may focus on access controls, product security on secure development, and AI risk on model governance. Without a unifying framework, silos emerge. A DVMS ensures that governance intent—the organization’s strategic objectives around trust, resilience, and performance—is clearly articulated and cascaded across all domains.
In this model:
- A central governance layer defines enterprise-wide objectives (e.g., “resilience by design”, “trusted digital operations”, “compliance with DORA/ISO”).
- Domain-specific dCISOs map their domain’s responsibilities into that overarching intent—e.g., product security maps to “secure-by-design for digital outcome trust”.
- The DVMS provides visibility into how each domain’s initiatives align with the strategic north star, avoiding fragmentation and drift.
Operational Capability: Turning Domain Roles into Integrated Action
Once intent is set, the operational challenge remains multiple domains, multiple leaders, multiple processes. The DVMS serves as the system of operational capability—standardizing how domains enact controls, manage risk, measure performance, and interoperate. For Microsoft’s 14 dCISOs, the DVMS helps ensure that, for example, identity risk doesn’t operate in isolation from cloud infrastructure risk, engineering systems security doesn’t ignore supply chain dependencies, and AI risk aligns with product security and governance.
Key features include:
- A unified control library mapped to domains but aligned to the enterprise risk taxonomy.
- Cross-domain workflows: when identity domain flags an issue, cloud domain is notified; product domain adapts; assurance evidence is captured.
- Shared dashboards: each dCISO retains domain focus, but the corporate CISO and board see an integrated view of digital risk, trust, and performance.
Assurance Evidence: Making the Invisible Visible
With more roles and domains, generating coherent assurance becomes harder: how do you demonstrate to the board or regulator that you have a unified security posture rather than 14 isolated programs? DVMS addresses this by establishing the assurance evidence layer, which captures metrics, controls execution, incidents, recovery, and improvement across domains, and aggregates them into unified reporting.
- Domain dCISOs log their metrics, test results, and control execution into the DVMS platform.
- The platform normalizes and aggregates these into enterprise-level assurance reports—showing resilience, trust, and regulatory alignment.
- The CISO can use the assurance layer to show the board a “single pane of glass” rather than a series of disconnected domain reports.
Dealing with Pinch Points in a Distributed CISO Model
Fragmentation and Misalignment
When security responsibilities are spread across many leaders, fragmentation is a key risk. Domain teams may pursue local optimization (e.g., product security focuses on speed to market, identity security focuses on strict controls), leading to conflicts or gaps. DVMS alleviates this by ensuring that all domains operate on the exact governance-capability-assurance lifecycle and that alignment to enterprise intent is continuously tracked.
Accountability Diffusion
14 deputy CISOs means 14 distinct accountability threads—who is ultimately responsible when a cross-domain incident occurs? The DVMS clarifies accountability by linking domains to enterprise risk categories and ownership. In doing so, the corporate CISO retains oversight, while domain leads carry operational accountability, and the governance layer ensures that escalation paths and decision rights are defined.
Reporting Overload & Board Visibility
Each domain may report separately to the corporate CISO, who must then translate 14 streams into a board-level narrative and assurance. DVMS provides the infrastructure for consolidated reporting, enabling the CISO to present meaningful, concise metrics: aggregated risk posture, resilience indices, regulatory alignment scores, and stakeholder trust indicators.
Regulatory Complexity & Demonstrable Assurance
Regulators are increasingly expecting continuous, quantifiable assurance across operations, rather than periodic audits. A distributed model complicates this. DVMS enables consistent evidence to capture across domains, aligning control execution, test results, incident response, and improvement loops into an auditable system. For firms facing regulations such as the Digital Operational Resilience Act (DORA) or AI governance standards, this is crucial.
Competitive Advantage of DVMS in This Context
In a world where companies like Microsoft are moving toward multiple domain-specific security leaders, the DVMS not only addresses the risks but also becomes a competitive differentiator. It enables organizations to:
- Scale security governance: By decentralizing domain accountability while retaining central coherence.
- Accelerate decision-making: Domain leads can act rapidly within their remit, while DVMS ensures integration and governance controls are not bypassed.
- Prove resilience and trust: For customers, regulators, and partners, the assurance that a unified system governs the entire digital value chain is robust.
- Adapt dynamically: As new domains emerge (such as AI risk, supply-chain security, digital twins), DVMS accommodates them rather than requiring disparate patches.
Conclusion
The transformation of Microsoft’s CISO role—splitting responsibility into 14 deputy CISOs aligned to domain-specific functions—is emblematic of the broader shift in enterprise security governance. As threats, digital architectures, regulatory demand, and stakeholder expectations all multiply, the one-person CISO model simply cannot keep pace. A DVMS offers a robust answer: it aligns governance intent across the enterprise, systematizes operational capability across domains, and provides unified assurance evidence for boards, regulators, and stakeholders.
In doing so, DVMS transforms what could be a risky, fragmented model of domain-centric deputies into a cohesive, strategic system that enables organizations not only to manage but also to thrive in today’s complex digital risk landscape. By consolidating multiple domain-specific security leads into a single intelligence system, the enterprise ensures coherence, accountability, and trust—transforming security governance from a reactive program to a strategic asset.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
DVMS Cyber Resilience Professional Accredited Certification Training
Teaching Enterprises How to Govern, Assure, and Account for Operational Resilience in Living Digital Ecosystems
Moving From Paper to Practice-Based Operational Resilience
Explainer Video – Governing By Assurance
Despite an abundance of frameworks, metrics, and dashboards, many leaders still lack a clear line of sight into how their digital value streams perform when conditions deteriorate.
Strategic intent, organizational structures, and day-to-day behaviors are evaluated separately, producing static snapshots that fail to reveal how decisions, dependencies, and human actions interact within a dynamic digital system.
The result is governance that appears comprehensive in documentation yet proves fragile under pressure, leaving leaders to reconcile disconnected controls rather than systematically strengthen operational resilience.
What is needed is a framework-agnostic operating overlay that enables operational resilience to be governed, assured, and accounted for coherently across complex, living digital ecosystems.
DVMS Institute White Papers – The Assurance Mandate Series
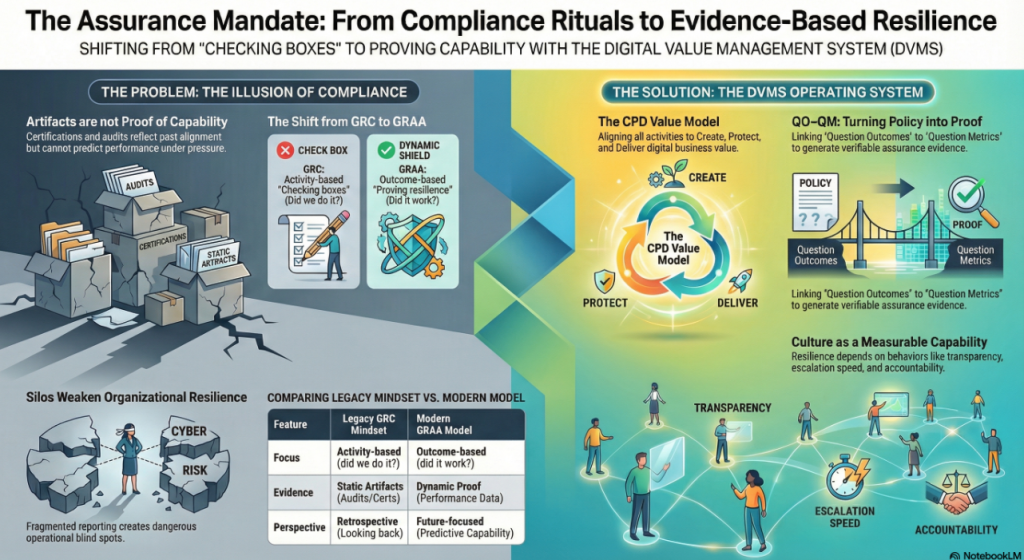
Explainer Video – From Compliance Rituals to Evidence-Based Resilience
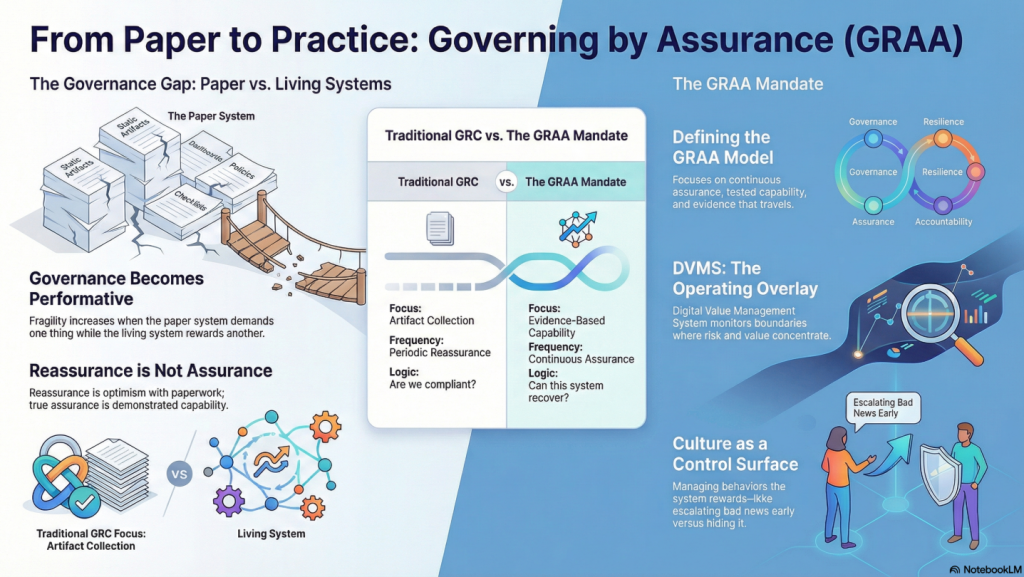
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
The Assurance Mandate Paper explains why traditional compliance artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
The Digital Value Management System® (DVMS)
Explainer Video – What is a Digital Value Management System (DVMS)
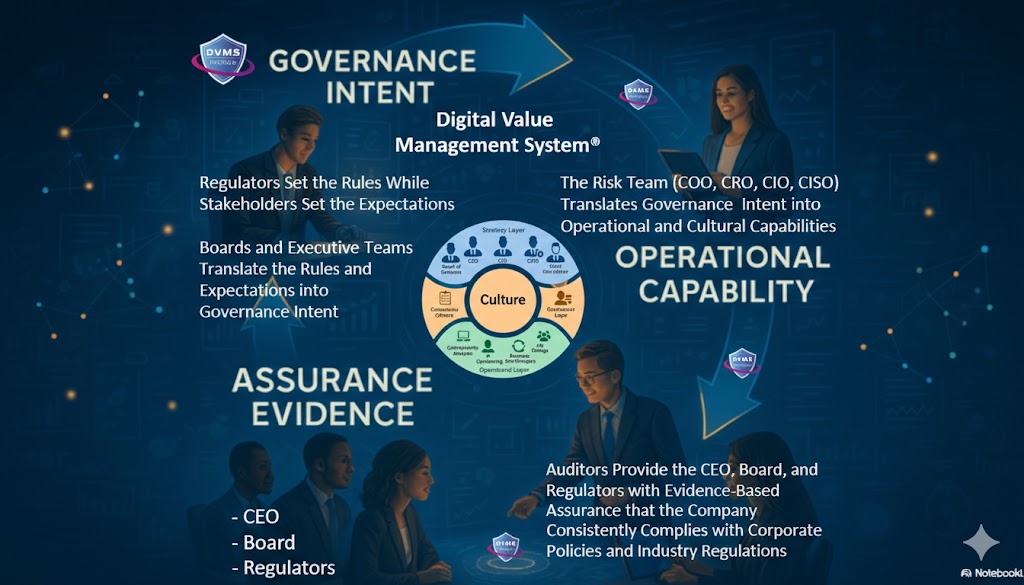
The DVMS is an overlay management system that governs, assures, and accounts for operational resilience in complex, living digital ecosystems. It does so by ensuring living-system outcomes account for paper-system intent.
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business performs
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Learning – for governance intent and operational capability fine-tuning
Underpinning this integration are three distinctive DVMS models
Create, Protect, and Deliver (CPD) – The CPD Model™ is a systems-based model within the DVMS that links strategy-risk and governance to execution to create, protect, and deliver digital business value as an integrated, continuously adaptive capability.
3D Knowledge (3DK) – The 3D Knowledge Model is a systems-thinking framework that maps team knowledge over time (past, present, future), cross-team collaboration, and alignment to strategic intent to ensure that organizational behavior, learning, and execution remain integrated and adaptive in delivering digital business value.
Minimum Viable Capabilities (MVC) – The Minimum Viable Capabilities (MVCs) model supports the seven essential, system-level organizational capabilities—Govern, Assure, Plan, Design, Change, Execute, and Innovate—required to reliably create, protect, and deliver digital business value in alignment with strategy-risk intent.
The models work together to enable the following organizational capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Benefits – Organizational and Leadership
Explainer Video – DVMS Organization and Leadership Benefits
Instead of replacing existing operational frameworks and platforms, the DVMS elevates them, connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
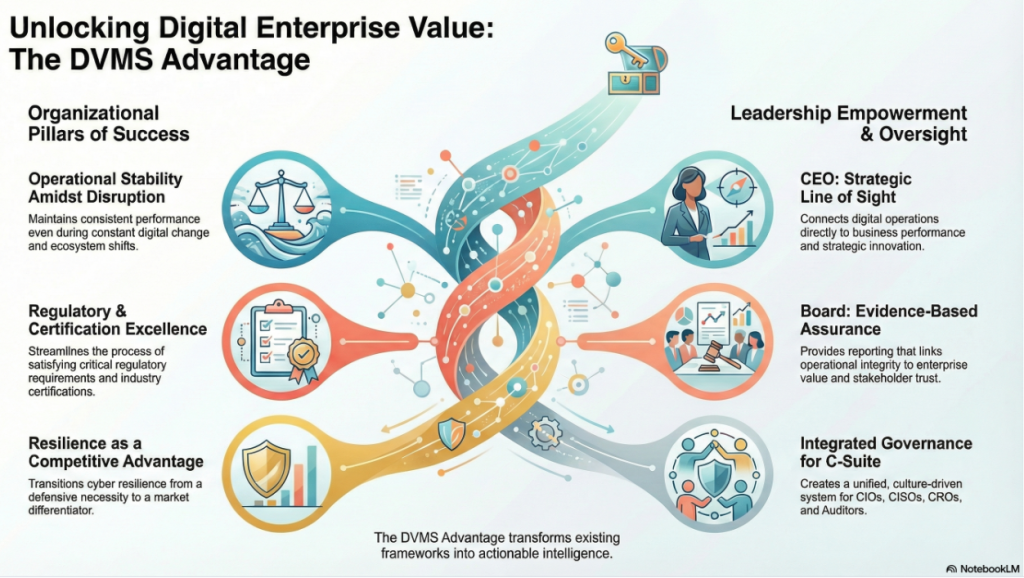
By adopting a DVMS, enterprises are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors, an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability.
DVMS – Accredited Certification Training Program
Explainer Video – The DVMS Training Pathway to Cyber Resilience
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to integrate fragmented systems into a unified, culture-driven governance and assurance system that accounts for the resilience of digital value within a living digital ecosystem.
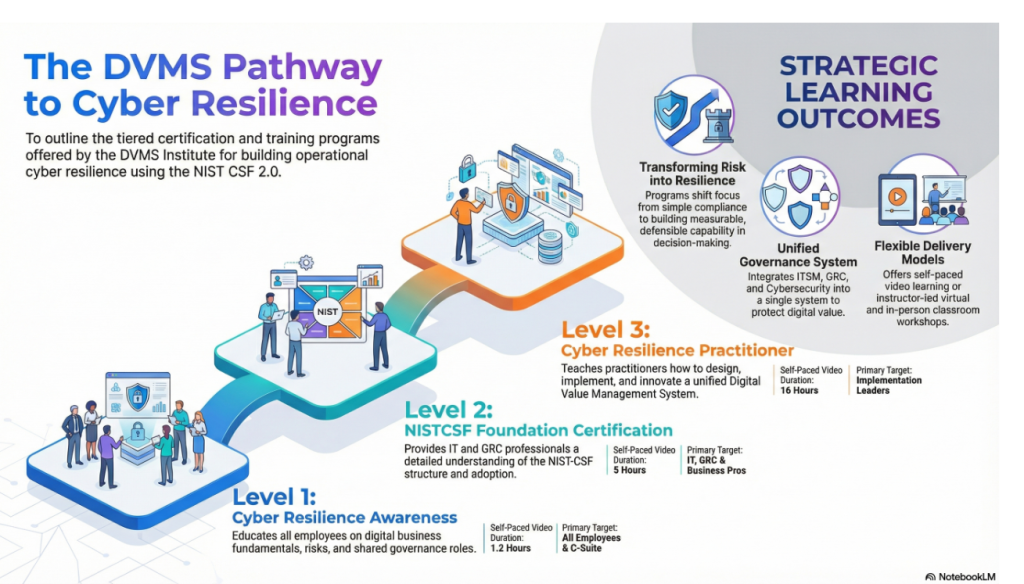
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS NISTCSF Cyber Resilience Foundation Certification Training
The DVMS NISTCSF Cyber Resilience Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
A FastTrack Approach to Launching Your DVMS Program
Explainer Video – Scaling a DVMS Program
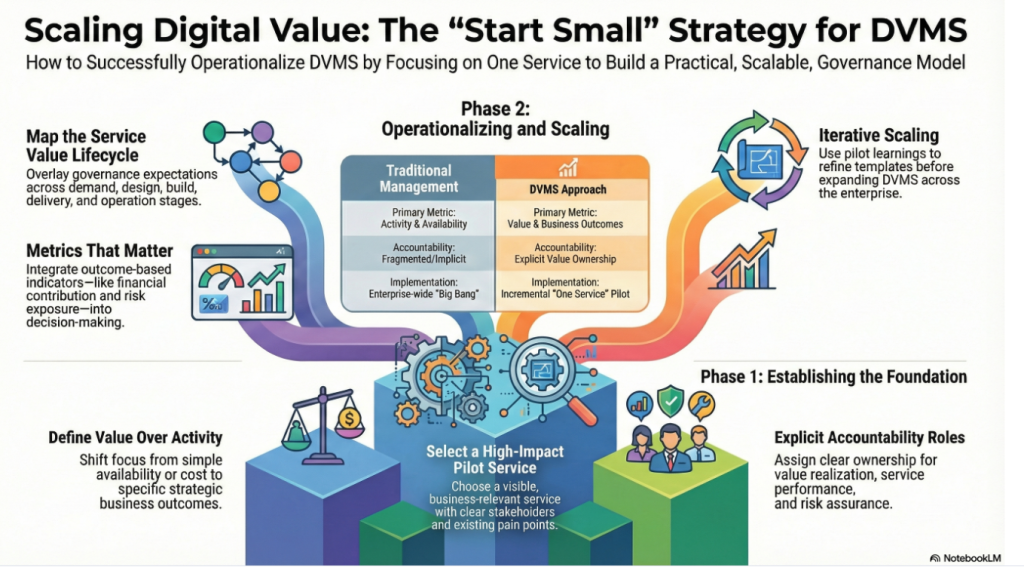
The DVMS FastTrack approach is a phased, iterative approach that helps organizations mature their DVMS over time, rather than trying to do everything simultaneously.
This approach breaks the DVMS journey into manageable phases of success. It all starts with selecting the first digital service you want to make cyber resilient. Once that service becomes resilient, it becomes the blueprint for operationalizing cyber resilience across the enterprise and its supply chain.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved