From Intent to Action – Turning Strategy into Daily Decisions – The Assurance in Action Series – Part 1
David Nichols – Co-Founder and Executive Director of the DVMS Institute
The Mandate for Managers
Resilience is no longer optional. For boards today, it is a clear expectation and, increasingly, a fiduciary obligation. Directors put it plainly: “We must ensure operational resilience to protect stakeholder trust.” That intent becomes the guiding principle for governance.
Executives turn this intent into policies. They create continuity plans, establish statements of cyber risk tolerance, publish vendor dependency guidelines, and set escalation procedures. On paper, it appears to be leadership in action. However, policies, no matter how well written, are not the same as capabilities.
This is where managers step in. They serve as the critical translation layer. Their role is to convert executive intent into integrated, non-siloed capabilities that can endure disruption. More importantly, those capabilities must produce assurance evidence that proves resilience in practice.
The Assurance Mandate Series argued that executives need to go beyond appearances and require evidence to support their decisions. Now, the emphasis shifts. If boards and executives are to govern through assurance, then managers must provide it.
I saw this translation problem firsthand when a CEO once told me, ‘Go implement client-server.’ It was a directive without clarity of intent. Only by reframing the conversation around strategic outcomes could we design the right capabilities.
The Disconnect in Practice
In most organizations, managers inherit siloed directives by function. Cybersecurity leaders respond by tightening controls and strengthening defenses. IT managers focus on uptime, SLAs, and efficiency. Compliance teams prepare for the next audit and update the risk register. Each group believes it is fulfilling the policy’s intent.
Yet, what they are building are fragments, not full capabilities. And when disruption occurs, the cracks become clear.
The 2017 Equifax breach illustrates a clear example. The board prioritized protecting consumer trust. The company had established frameworks, passed its audits, and obtained industry certifications. However, siloed practices resulted in a crucial patch remaining unimplemented. When attackers exploited this vulnerability, over 140 million consumer records were compromised. Policies were in place, frameworks adopted, but essential capabilities were missing.
The 2021 Colonial Pipeline ransomware attack followed a similar pattern. Leadership emphasized continuity of operations, but cyber was still treated as “IT’s problem.” When ransomware struck, technical controls were in place, but there was no integrated ability to keep services running. A regional outage turned into a national crisis.
In 2024, Snowflake’s breach revealed another aspect of this gap. Customers believed their resilience was assured because the platform held certifications and followed industry frameworks. However, when attackers exploited misconfigurations in more than 160 customer environments, the organization was unable to prevent a widespread loss of trust. Compliance had been met. Resilience had not.
In each case, boards had set a clear intent. Executives had written policies. But the translation into non-siloed capabilities never happened.
That conversation with our CEO forced us to confront the difference between slogans and strategy. Once we clarified intent, we were able to build a capability that delivered value to both distributors and customers.
The CPD Model as Scaffolding
This is where the Create, Protect, Deliver (CPD) Model provides managers with an essential scaffolding from which they operationalize the MVC.
As described in our books, Thriving on the Edge of Chaos and the Practitioner’s Guide to Building Cyber-Resilience (Second Edition), CPD redefines resilience as the ability to simultaneously generate digital business value, protect that value from threats and disruptions, and deliver it reliably to stakeholders. It is not a strict checklist. It does not prescribe controls or maturity levels. Instead, it provides a conceptual scaffolding that aligns every activity with the ultimate goal: stakeholder trust.
For managers, CPD is not just an abstract concept; it is a vital component of professional development. It serves as the perspective through which executive policies are understood and translated into operational terms. When boards state, “We must protect customer trust during disruption,” CPD offers the framework for managers to ask: What does this mean for how we design services (or create them)? How do we safeguard them (protect)? And how do we ensure continuity of delivery (deliver)?
But scaffolding alone does not create the structure. Managers need a practical way to turn policy into capabilities. This is where the Minimum Viable Capabilities (MVC) overlay comes into play. MVC acts like a diagnostic tool. By comparing current practices to MVC, managers identify the gaps that prevent the organization from reaching true resilience.
This process is not a one-time overhaul; it is an ongoing process. It is a cycle of incremental innovation. Each identified gap—whether in vendor continuity planning, cross-functional escalation, or incident rehearsal—becomes an opportunity to strengthen capabilities. Over time, these small, systemic improvements compound into demonstrable resilience.
From Policy to Capability
Turning executive policy into capability is not a straightforward process. Managers must adopt a discipline that closes the loop between intent and evidence.
It begins with clarifying intent. A board might declare: “We must ensure customer services remain available during cyber disruption.” Managers must reframe that in CPD terms. Continuity of customer service is not a single control. It is the coordinated ability to create services with continuity features, protect them through rehearsed incident response, and deliver them reliably even under attack.
The next step is mapping to capabilities. Using MVC, managers assess what exists and what is missing. The policy may exist, but if there is no rehearsed recovery capability, no evidence of vendor resilience, or no mechanism for escalation, then the intent remains unrealized.
Third, managers must integrate across functions. Siloed ownership undermines resilience. Vendor management is not just a compliance exercise in reviewing contracts. It is also about protecting through security attestations and delivering through performance monitoring and assurance evidence. Every capability must touch all three CPD dimensions.
Finally, managers must generate assurance evidence. Workflows are insufficient unless they provide proof of performance. This is where the QO–QM (Question Outcome–Question Metric) model, introduced in Practitioner, becomes vital. Boards articulate the desired outcome (“fit for purpose”); managers define the metrics that prove operational performance (“fit for use”). The gap between the two is what drives continuous improvement and innovation.
Without this cycle, managers tend to revert to familiar patterns: controls, reports, and audits that offer comfort but not confidence. With it, managers become the bridge that turns policy into resilience.
What we delivered was an enterprise-wide, integrated service information system that transformed strategic intent into an organizational capability to service our distributors and their customers’ equipment seamlessly, adapting to multiple distribution channels and new and retired products and services.
A Manager’s Paradigm Shift
This requires a profound shift in managerial mindset.
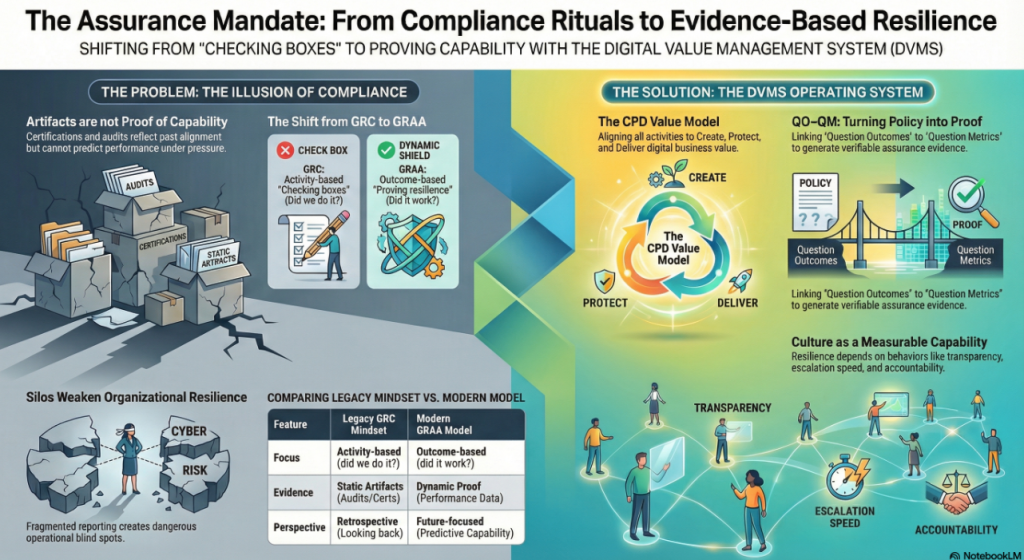
The traditional method focused on controlling processes, generating reports, and passing audits. Managers associated activity with achievement.
The new approach focuses on building capabilities, integrating across functions, and providing assurance evidence. Managers need to stop confusing artifacts with proof. A patch rate is an artifact. A recovery benchmark is assurance. An audit checklist is an artifact. Demonstrating the ability to restore services under stress is an assurance.
As Thriving on the Edge of Chaos reminds us, leadership is the art of turning complexity into clarity. Managers practice leadership every time they translate intent into integrated capabilities that produce evidence of resilience.
My own application of systems thinking, inspired by Peter Senge’s The Fifth Discipline, reinforced this lesson: resilience is not the result of isolated fixes, but of integrated disciplines working in harmony.
A Practical Illustration
Consider again the policy: “Ensure customer services remain available during cyber disruption.”
In the old approach, cybersecurity teams strengthened access controls, IT tracked uptime, and compliance prepared audit reports. Each department reported success in its own way. However, when disruptions occurred, escalation was slow, workflows failed, and continuity was disrupted. The board received reports but not actual results.
In the CPD-driven approach, the same policy appears different. Services are designed with built-in continuity and redundancy to ensure uninterrupted operation. Cross-functional teams safeguard them by conducting rehearsed response and recovery exercises. Evidence of assurance is generated to demonstrate that services are delivered within acceptable thresholds even during disruptions. The board doesn’t just see an artifact; it sees proof.
The difference isn’t in frameworks. Both organizations might align with ISO 27001 or NIST CSF. The real difference lies in whether managers utilize CPD and MVC to transform policies into capabilities that generate assurance evidence.
The Executive Question for Managers
The Assurance Mandate Series ended with a challenge to boards: demand assurance, not artifacts. The Assurance in Action Series begins with a challenge to managers: supply that assurance, not just activity.
The question every manager faces is simple but crucial: Are you focusing on reporting artifacts, patch counts, audit scores, and compliance checklists? Or are you showcasing evidence, recovery times, escalation effectiveness, and continuous delivery under pressure?
Artifacts provide comfort. Evidence builds confidence.
Resilience is no longer optional and cannot be delegated. It is shaped by the daily choices managers make when translating intent into capability. Suppose you develop capabilities that turn strategic intent into action and ensure they are both ready for use and suitable for purpose. In that case, you won’t fear being called into the boardroom — you’ll welcome it.
The path from intent to assurance starts with managers. This is where strategy turns into action, and action turns into proof.
From Maps to Journeys
Frameworks offer maps. Compliance offers snapshots. Culture offers potential. But only systems provide assurance.
The Digital Value Management System (DVMS) ensures that CPD intent is translated into MVC-aligned capabilities and that evidence of resilience is communicated upward to executives and boards. It is not about activity for its own sake. It is about proof that the organization can withstand disruption and keep delivering value.
For managers, this marks a shift in mindset. Stop mixing activity with confidence. Begin developing capabilities that demonstrate resilience.
The journey from intent to assurance begins with managers who turn strategy into daily decisions and then translate those decisions into evidence.
Looking Ahead
In the following article of the Assurance in Action Series, we will explore how managers can implement a widely cited but inconsistently applied framework—the NIST Cybersecurity Framework—using DVMS. We will demonstrate how to transform CSF from a mere compliance checklist into a dynamic assurance system that showcases resilience in practice.
About the Author

Dave is the Executive Director of the DVMS Institute.
Dave spent his “formative years” on US Navy submarines. There, he learned complex systems, functioning in high-performance teams, and what it takes to be an exceptional leader. He took those skills into civilian life and built a successful career leading high-performance teams in software development and information service delivery.
DVMS Cyber Resilience Professional Accredited Certification Training
Teaching Enterprises How to Govern, Assure, and Account for Operational Resilience in Living Digital Ecosystems
Moving From Paper to Practice-Based Operational Resilience
Explainer Video – Governing By Assurance
Despite an abundance of frameworks, metrics, and dashboards, many leaders still lack a clear line of sight into how their digital value streams perform when conditions deteriorate.
Strategic intent, organizational structures, and day-to-day behaviors are evaluated separately, producing static snapshots that fail to reveal how decisions, dependencies, and human actions interact within a dynamic digital system.
The result is governance that appears comprehensive in documentation yet proves fragile under pressure, leaving leaders to reconcile disconnected controls rather than systematically strengthen operational resilience.
What is needed is a framework-agnostic operating overlay that enables operational resilience to be governed, assured, and accounted for coherently across complex, living digital ecosystems.
DVMS Institute White Papers – The Assurance Mandate Series
Explainer Video – From Compliance Rituals to Evidence-Based Resilience
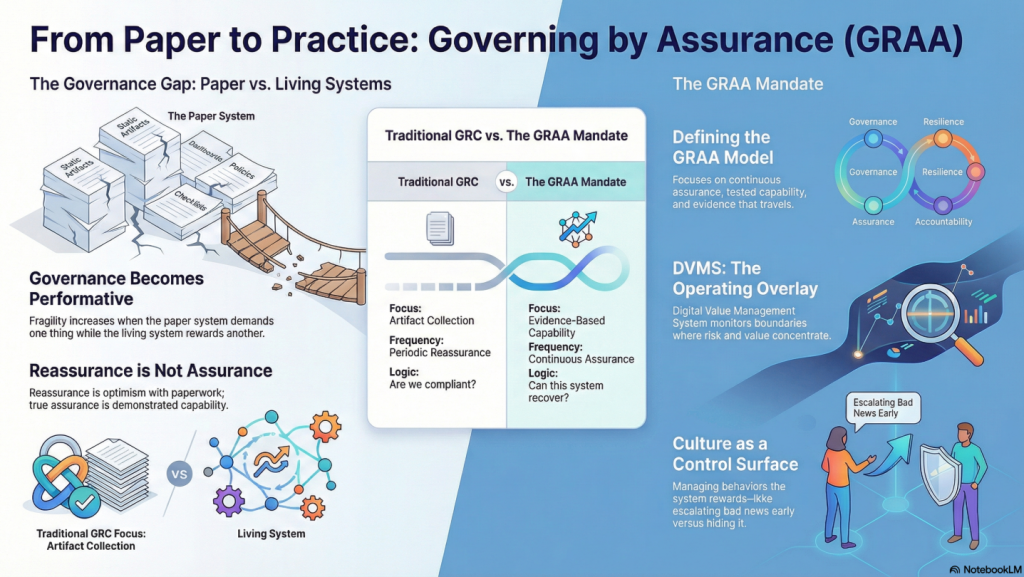
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
The Assurance Mandate Paper explains why traditional compliance artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
The Digital Value Management System® (DVMS)
Explainer Video – What is a Digital Value Management System (DVMS)
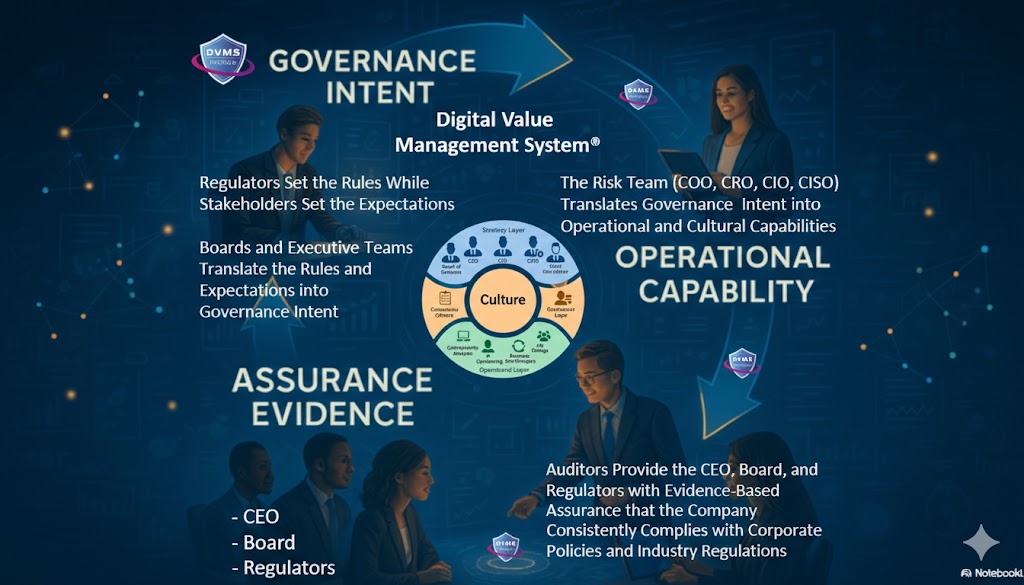
The DVMS is an overlay management system that governs, assures, and accounts for operational resilience in complex, living digital ecosystems. It does so by ensuring living-system outcomes account for paper-system intent.
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business performs
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Learning – for governance intent and operational capability fine-tuning
Underpinning this integration are three distinctive DVMS models
Create, Protect, and Deliver (CPD) – The CPD Model™ is a systems-based model within the DVMS that links strategy-risk and governance to execution to create, protect, and deliver digital business value as an integrated, continuously adaptive capability.
3D Knowledge (3DK) – The 3D Knowledge Model is a systems-thinking framework that maps team knowledge over time (past, present, future), cross-team collaboration, and alignment to strategic intent to ensure that organizational behavior, learning, and execution remain integrated and adaptive in delivering digital business value.
Minimum Viable Capabilities (MVC) – The Minimum Viable Capabilities (MVCs) model supports the seven essential, system-level organizational capabilities—Govern, Assure, Plan, Design, Change, Execute, and Innovate—required to reliably create, protect, and deliver digital business value in alignment with strategy-risk intent.
The models work together to enable the following organizational capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Benefits – Organizational and Leadership
Explainer Video – DVMS Organization and Leadership Benefits
Instead of replacing existing operational frameworks and platforms, the DVMS elevates them, connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
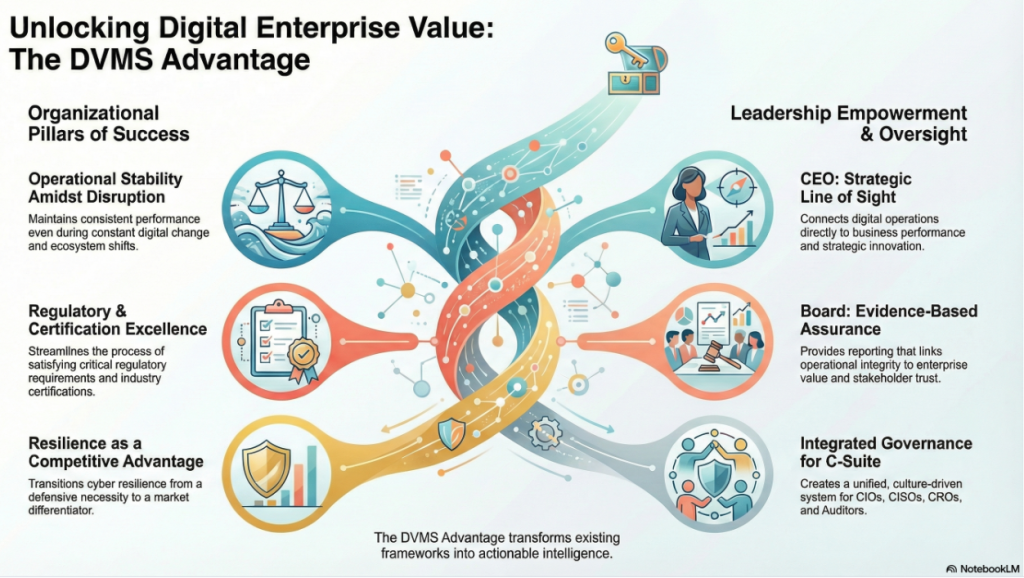
By adopting a DVMS, enterprises are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors, an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability.
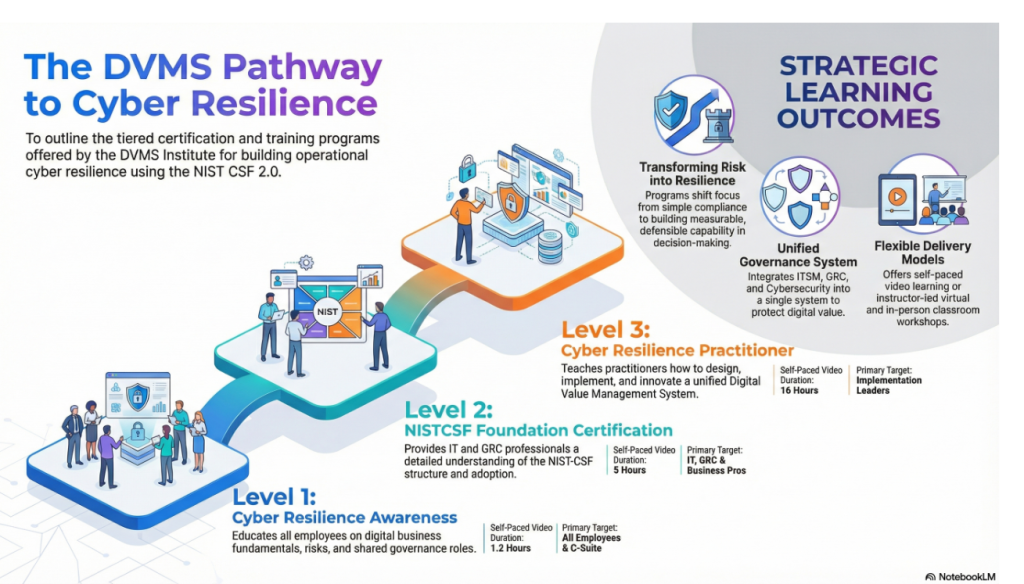
DVMS – Accredited Certification Training Program
Explainer Video – The DVMS Training Pathway to Cyber Resilience
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to integrate fragmented systems into a unified, culture-driven governance and assurance system that accounts for the resilience of digital value within a living digital ecosystem.
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS NISTCSF Cyber Resilience Foundation Certification Training
The DVMS NISTCSF Cyber Resilience Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
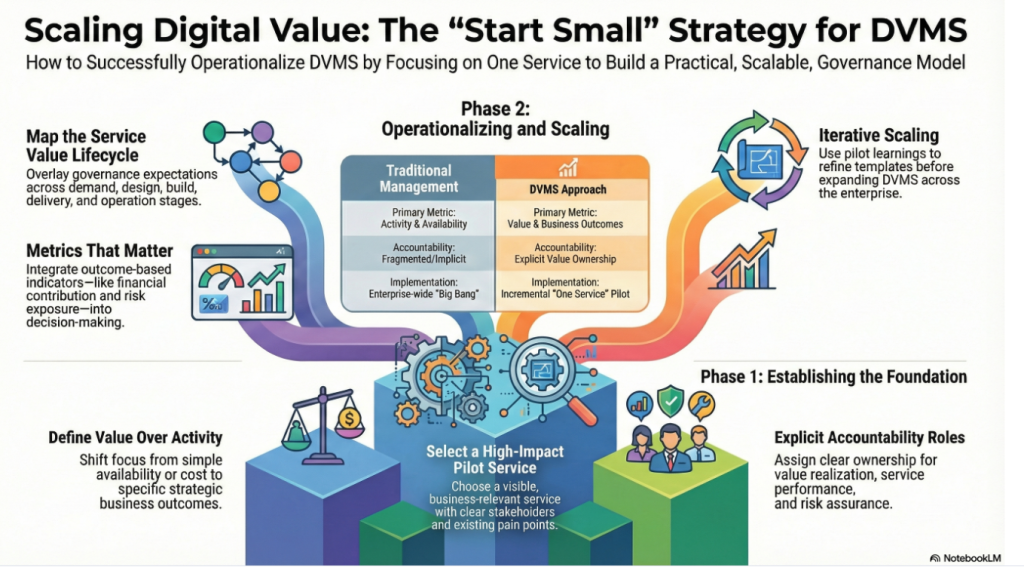
A FastTrack Approach to Launching Your DVMS Program
Explainer Video – Scaling a DVMS Program
The DVMS FastTrack approach is a phased, iterative approach that helps organizations mature their DVMS over time, rather than trying to do everything simultaneously.
This approach breaks the DVMS journey into manageable phases of success. It all starts with selecting the first digital service you want to make cyber resilient. Once that service becomes resilient, it becomes the blueprint for operationalizing cyber resilience across the enterprise and its supply chain.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved