Bridging the Silos – How DVMS Connects the Languages of Governance, Cyber, and Business – Assurance Mandate Series – Part 3
David Nichols – Co-Founder and Executive Director of the DVMS Institute
Lost in Translation
Your CISO discusses vulnerabilities, controls, and threat actors. Your board emphasizes trust, accountability, and value. Risk officers focus on registers and frameworks. Business operators prioritize uptime, revenue, and customer confidence.
Each of them is telling the truth from their perspective. Yet when those truths are not connected, they don’t add up to reassurance — they create noise. And when the signal gets lost in that noise, resilience slips away.
This is the core issue: in today’s enterprises, governance, cybersecurity, and business operations each use different languages. Without a system to bridge these gaps, leaders are left making decisions in the spaces between these perspectives. It is in those gaps that crises develop.
The Silo Problem
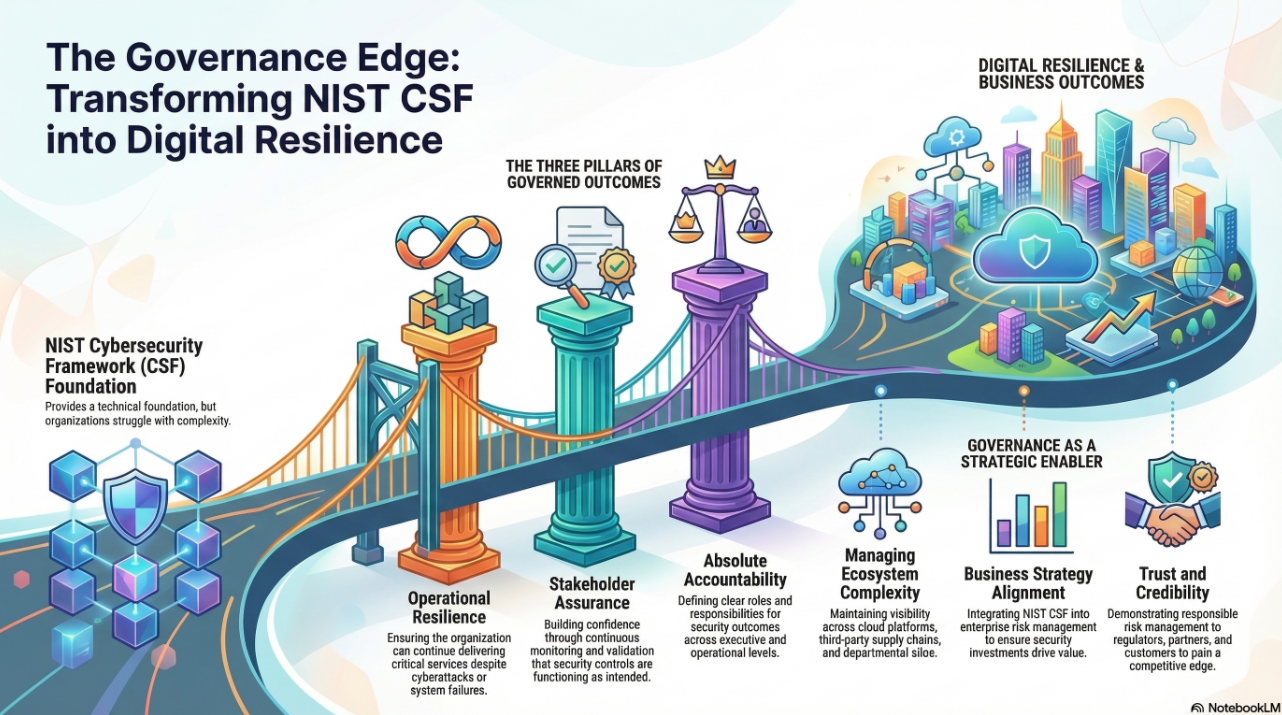
Digital trust doesn’t reside in a single department; it exists at the crossroads of governance, cybersecurity, risk, and operations. However, most organizations fail to recognize this. Instead, each domain reports independently, leading to confusion. Boards seek confidence in ongoing operations but often receive meaningless dashboards filled with out-of-context risk heatmaps and compliance scores. Security teams focus on fixing vulnerabilities, strengthening systems, and incident response, but the jargon of patches and controls often fails to resonate in the boardroom. Risk and compliance officers diligently track controls against ISO standards or NIST CSF categories, creating neat logs that seem authoritative but quickly become outdated. Business leaders, who are most responsible for customer satisfaction, view digital trust primarily through system uptime, transaction success, and customer satisfaction.
All of these perspectives are important. None of them is incorrect. However, when taken alone, they are incomplete. Even worse, they often clash, with each group vying for attention. A board that hears “we’re compliant” might assume the company is resilient, while the CISO knows that a single unpatched system could undermine that confidence overnight. A risk officer might show a heatmap of potential threats, but the operations lead is dealing with a real outage that the heatmap never identified. Each voice is speaking, but without translation, no one is truly understood.
To butcher a line from the Buffalo Springfield, “Nobody’s wrong if everybody’s right.”
Consequences of Misalignment
When these silos remain disconnected, leaders make decisions with incomplete information. History provides many examples of how risky this can be.
Take Equifax in 2017. On paper, the company appeared well-governed. Compliance programs were implemented, audits were conducted, and regulators felt reassured. However, in reality, a critical patch was missed, and the vulnerability was exploited by attackers. The board heard “we are compliant,” but compliance does not equal resilience. The breach ultimately cost over $1.4 billion in settlements and remediation, along with immense damage to public trust.
Consider Colonial Pipeline in 2021 as an example. When ransomware paralyzed operations, each silo responded differently. Security teams worked to contain the attack. Business leaders hurried to manage supply disruptions. Governance faced regulators, lawmakers, and the public, trying to explain why the nation’s largest fuel pipeline had shut down. Each group held part of the truth, but without coordination, the response was slow, costs increased, and the company’s name became a symbol of vulnerability.
The point isn’t that compliance, security, or business operations failed on their own. The real issue is that without integration, their truths never formed a clear, unified picture. When leaders make decisions based on fragmented information, resilience is always at risk.
DVMS: The Rosetta Stone
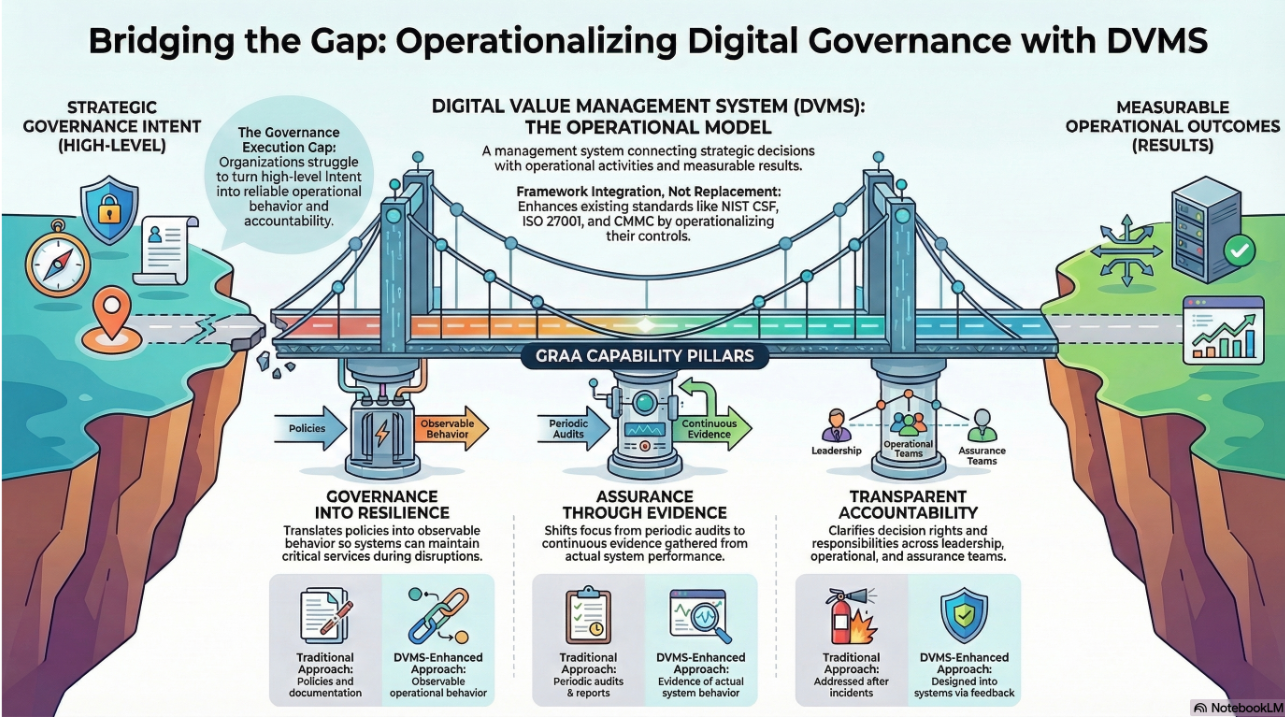
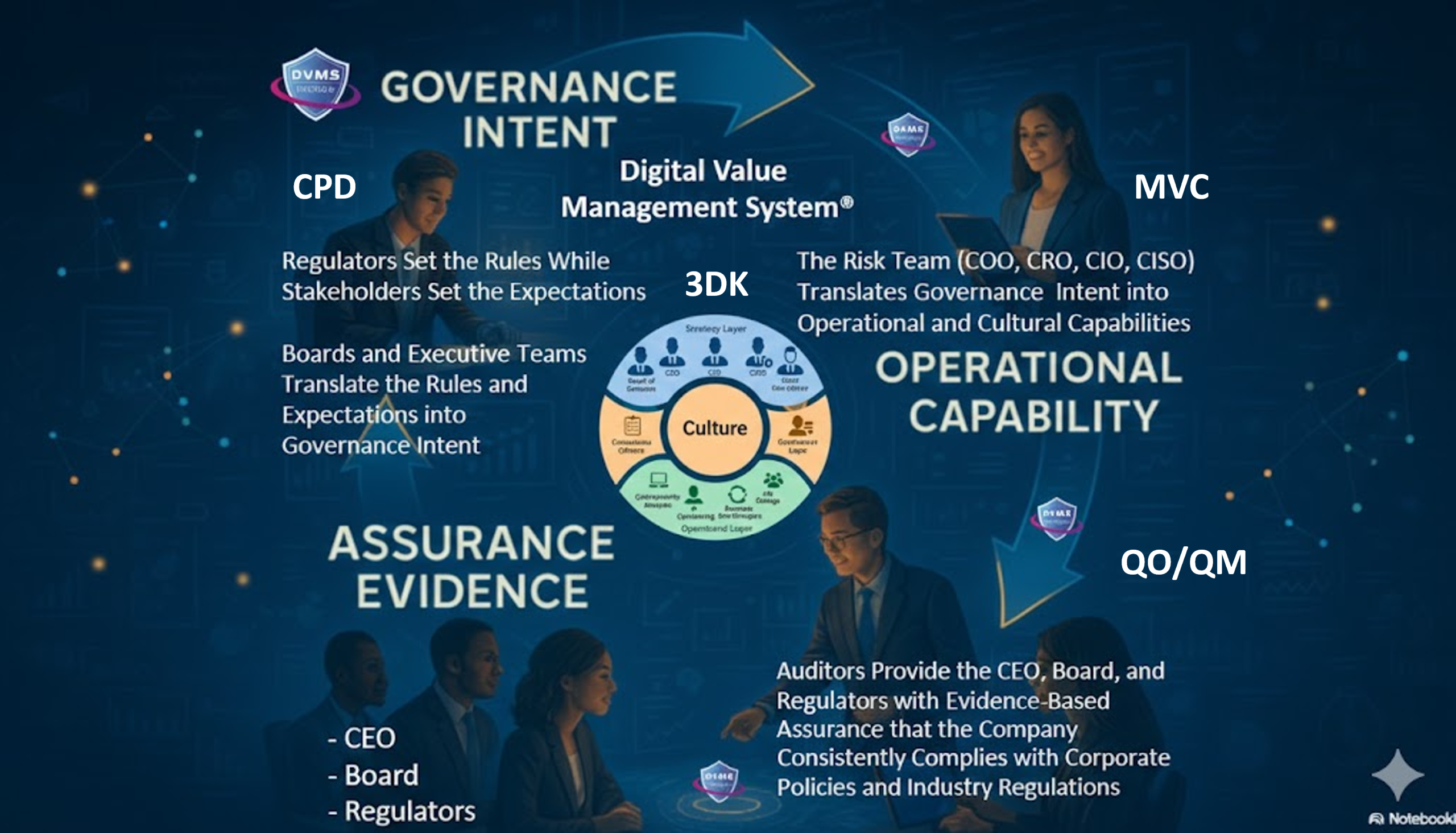
This is the problem the Digital Value Management System® (DVMS) was built to solve. DVMS serves as the Rosetta Stone for governance, translating between the languages of cyber, risk, and business to ensure that intent, performance, and assurance align.
Think of it as the operating system of digital governance. Frameworks and tools, ISO, NIST, ITIL, and COBIT, are like apps. Each holds value, but only within its own domain. Alone, they don’t coordinate. DVMS operates at the top, ensuring that frameworks are not only adopted but also aligned, not only documented but also practiced, and not only isolated but integrated into a continuous system of assurance.
With DVMS in place, governance intent can be clearly expressed and effectively translated into cyber controls that genuinely matter. These controls can then be measured in terms of resilience, not just configuration. Additionally, these resilience metrics can be fed back to the board as assurance evidence, closing the loop between strategy and operations.
What Bridging Looks Like in Practice
Imagine a board clearly states its goal: “Our customers must have uninterrupted access to digital services, even during disruption.” Under the old model, that goal might be interpreted into a compliance framework or a set of technical controls, each isolated from the others. The board would eventually review the certification report and assume that the mission had been achieved.
Under DVMS, the process is different. Managers transform that intent into structures, including policies, workflows, and metrics, designed for adaptability and flexibility. Cybersecurity leaders implement controls that are directly linked to these structures, including zero-trust access, automated monitoring, and incident playbooks, to ensure continuity. DVMS then gathers evidence, not just to determine whether a control exists, but also to assess whether it performs effectively under pressure. The board gets assurance not from checklists, but from resilience dashboards that show recovery time, continuity, and adaptability in action.
The difference is significant. Instead of four separate parallel conversations, leaders now deliver a cohesive story. Assurance is no longer taken for granted; it is proven.
The Executive Question
This raises a set of uncomfortable but necessary questions for executives and boards. Do you receive fragmented reports, each in a different language, with no system to connect them? Do you understand how a single control failure in cybersecurity translates into operational disruption and governance accountability? And most critically, can you prove, with evidence, that your resilience story is coherent across governance, cyber, and business operations?
If the answer is no, then you are not governing by assurance. You are governing by appearances. And appearances never survive disruption.
Closing the Gap
Silos are where resilience goes to die. Integration is where trust is built.
Frameworks always matter, but they aren’t enough. Tools and certifications offer comfort. Only systems instill confidence. The Digital Value Management System is that system, the operating system that aligns governance intent, cyber activity, and business outcomes.
That is how partial truths become a unified narrative of assurance. That is how leaders move beyond complexity and noise to confidence. And that is how resilience becomes real.
👉 Next in the Assurance Mandate Series: Culture Eats Controls for Breakfast — why true resilience depends on behavior as much as technology.
About the Author

Dave is the Executive Director of the DVMS Institute.
Dave spent his “formative years” on US Navy submarines. There, he learned complex systems, functioning in high-performance teams, and what it takes to be an exceptional leader. He took those skills into civilian life and built a successful career leading high-performance teams in software development and information service delivery.
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2026 All Rights Reserved