Closing the Loop – From Controls to Assurance Evidence – The Assurance in Action Series – Part 3
David Nichols – Co-Founder and Executive Director of the DVMS Institute
The Problem with Controls
Controls are necessary, but they are not enough. Every manager knows the routine: configure the firewall, update the patching cycle, enforce access restrictions, rehearse an incident response plan. Each measure matters, but none of them, standing alone, demonstrates organizational resilience.
This is the core issue. Controls offer a sense of security. We have something in place. We look good on dashboards, produce reassuring reports, and keep auditors satisfied. But as the last decade has demonstrated, organizations with extensive control catalogs still fail under stress. Controls are fragile. They can be misconfigured, bypassed, ignored, or undermined by siloed practices. Unless the entire system shows evidence of performance under pressure, boards and executives are left guessing: are we resilient, can we withstand an attack, and maintain our essential operational capabilities?
Boards do not want to be reassured that controls are in place. They want to know whether the organization can continue to create, protect, and deliver value when disruption strikes.
Why Evidence Matters
Here is where the conversation shifts from controls to evidence.
Evidence differs from the reports, lists, and dashboards managers usually provide. These artifacts, such as patch compliance reports, maturity scores, and audit checklists, demonstrate that activity has occurred; however, they do not indicate whether the organization can perform effectively under stress. They offer reassurance, but they don’t provide proof of operational resilience.
Assurance evidence, by contrast, is forward-looking. It demonstrates capability in action, showing whether systems, people, and culture hold up when conditions change. Evidence enables boards to govern with confidence, rather than relying on assumptions.
DVMS and the Evidence Cycle
In Thriving on the Edge of Chaos and the Practitioner’s Guide to Building Cyber-Resilience (Second Edition), the Digital Value Management System® (DVMS) is described as the overlay that connects governance intent, operational workflows, and assurance evidence.
Strategic intent starts as a policy that clearly states goals in outcome-focused terms. A board might declare: “Customer trust must be preserved during disruption.” That statement of intent isn’t a control or a checklist item, but a strategic direction. Management’s role is to transform that intent into capabilities that bring the outcome to life. For instance, incident response isn’t just a plan on paper, but a capability comprised of people, processes, and practiced actions. Within this capability, multiple outcomes can be set, including the speed of detection, accuracy of escalation, recovery within a specific threshold, and maintaining stakeholder communication. Each outcome is measurable, both in terms of “fit for purpose” (does it meet governance goals?) and “fit for use” (does it work effectively during rehearsals and real events?).
When managers organize capabilities this way, they create a feedback loop. Metrics such as recovery times, escalation effectiveness, and vendor resilience are reported back to the board, showing not only whether the goal has been met but also where gaps still exist. This data reassures directors that resilience is being put into practice and helps management identify where incremental innovation is needed. Policy explains the “why,” capabilities define the “how,” and assurance evidence confirms the “what.”
Policy explains the “why,” capabilities show the “how,” and assurance evidence demonstrates the “what.” While frameworks like the NIST Cybersecurity Framework provide a map, the Digital Value Management System ensures the journey actually takes place.
From Reports to Evidence
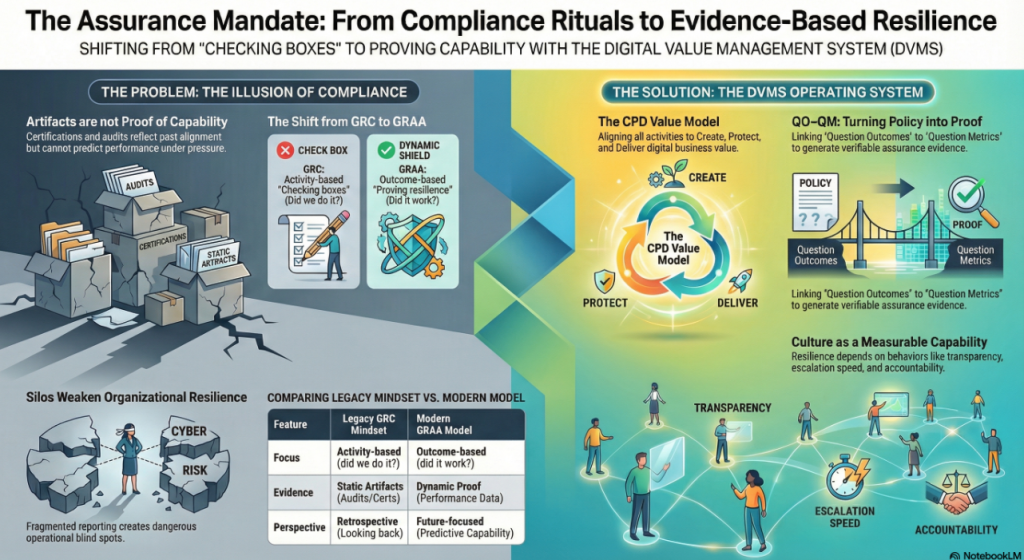
To clarify this distinction with familiar terms, consider the documents managers typically present today, such as reports, dashboards, maturity scores, and compliance checklists. In this series, we have referred to these as “artifacts,” meaning they document the existence of a control or capability. Artifacts are important because they make governance defensible and establish a baseline for measuring the effectiveness of efforts. However, they are static and retrospective in nature. They cannot predict whether the organization will succeed tomorrow in the face of disruption.
Assurance evidence is dynamic and forward-looking. It shows whether documented controls actually function under pressure. An artifact might say, “We applied patches.” Evidence says, “In our last three incidents, services were restored within governance thresholds, and customer trust was maintained.” The first provides comfort, the second builds confidence.
A Practical Illustration
Take the common directive: “Ensure operational resilience against a ransomware attack.”
In the traditional approach, managers focus on controls: contracts, patching policies, and backup procedures. Dashboards display completed backup jobs, tests performed, and audits that have been passed. To the board, this appears to be progress, but when ransomware strikes, recovery takes days instead of hours, customers lose access, regulators demand answers, and trust is lost.
In contrast, the DVMS approach has managers align the six NIST CSF functions, Govern, Identify, Protect, Detect, Respond, and Recover, with the CPD outcomes of creating, protecting, and delivering value. They rehearse ransomware scenarios, measure recovery times, and assess the effectiveness of escalation. The evidence is clear: in the last three ransomware exercises, services were restored in under three hours, meeting the four-hour governance threshold, and demonstrating operational resilience. Customer service was maintained, and stakeholders maintained confidence.
The difference is that the first approach shows activity, while the second proves capability.
CPD as the Organizing Principle
The Create, Protect, and Deliver (CPD) Model redefines how managers approach the NIST CSF. Instead of viewing its six functions as separate functions, CPD integrates them around business value. Create ensures services are designed with resilience in mind. Protect guarantees they are safeguarded through monitoring, security practices, and rehearsals. Deliver ensures continuity and recovery, demonstrating that trust is maintained.
When managers view the NIST CSF through the CPD lens, the functions are no longer seen as separate checkboxes. Instead, they become interconnected building blocks that support resilient capabilities. A “Respond” function, for instance, isn’t just a plan stored away. It’s a rehearsed workflow that shows recovery times and measures the effectiveness of escalation. “Recover” isn’t merely a checklist for restoring data. It serves as proof that services can be brought back within governance-defined thresholds, thus safeguarding customer trust.
QO–QM: Closing the Loop
The Practitioner’s Guide to Building Cyber-Resilience (Second Edition) introduces the QO–QM (Question Outcome–Question Metric) model as a practical way to connect governance intent with operational performance. Strategic intent is expressed as an outcome: the board might set a policy goal such as, “Services must be restored within four hours of disruption.” Managers then translate this into capabilities, such as rehearsed recovery processes, and measure the results against the stated outcome. They might report, “In our last three recovery drills, services were restored in an average of 2.5 hours.”
The difference between outcome and metric becomes the driver of continuous improvement. If the measured results fall short, managers adapt and strengthen capabilities until fit-for-purpose outcomes and metrics that are fit for use converge.
As emphasized in Thriving on the Edge of Chaos: Managing at the Intersection of Value and Risk in the Digital Era, leadership is the art of turning complexity into clarity. When the principles from the book are combined with the practical tools of the Practitioner’s Guide, managers gain both the perspective and the method to transform compliance into assurance. This loop turns intent into evidence, proof of resilience that boards and executives can trust.
The Role of AI and Automation
Historically, managers saw assurance as a burden. Gathering, testing, and reporting evidence of resilience was time-consuming, resource-intensive, and often overlooked. Demonstrating that systems could handle disruptions required drills, manual reports, and extensive documentation. As a result, boards usually relied on static reports and retrospective audits, while managers quietly accepted that showing assurance in real time was too costly to maintain.
That reality is evolving. Progress in automation and artificial intelligence is making assurance possible on a large scale. Automated monitoring now offers continuous visibility over infrastructure, applications, and supply chains. AI-driven simulations can dynamically evaluate resilience scenarios, testing for vulnerabilities in ways that mimic real-world disruptions. Agentic systems automatically log performance results into governance dashboards, narrowing the gap between operations and oversight.
For managers, this does not replace responsibility or human judgment; it enhances their ability to make informed decisions. Instead of chasing reports after the fact, managers can focus on interpreting assurance evidence, improving workflows, and building capabilities. The “burden of assurance” is no longer an excuse; it is becoming part of the routine discipline of digital management.
This shift redefines assurance itself. It is no longer endless paperwork that clutters compliance binders. It is real-time confidence, produced by systems that continually test, measure, and report on resilience. Boards no longer have to ask whether policy intent is being fulfilled; they can see the evidence. Managers no longer struggle to provide proof; they can focus on building stronger capabilities.
The Manager’s Paradigm Shift
For most managers, the traditional approach to governance and resilience has been transactional in nature. The task involved implementing controls, producing reports, and preparing for audits. Activity was equated with progress. A patch applied, a system scanned, or a compliance checklist completed all served as proof of diligence. This worked in a world where disruption was occasional and regulators were satisfied with artifacts of compliance.
But disruption today is constant, and boards no longer accept artifacts as evidence. They require assurance, proof that capabilities can perform under stress and that resilience is embedded into daily operations. This is the core of the manager’s paradigm shift: moving from delivering documentation to building capabilities that inspire confidence.
That shift cannot occur gradually. It requires managers to think in terms of systems. The Create, Protect, Deliver (CPD) Model shifts focus from silos to value. Every capability must help create digital business value, protect it from disruptions, and deliver it reliably.
The Minimum Viable Capabilities (MVC) overlay is how managers implement this approach. By comparing policies and current practices to MVC, managers identify the gaps that weaken resilience. These gaps aren’t fixed with a single project. Still, they are closed through ongoing capability improvements, step by step, function by function, until the organization can confidently demonstrate that it meets CPD requirements.
The QO–QM (Question Outcome–Question Metric) model, introduced in The Practitioner’s Guide, connects intent to evidence. The board may ask, “Can we restore services within four hours of disruption?” Managers then develop and practice capabilities, measure actual performance, and report, “In our last three recovery drills, services were restored in an average of 2.5 hours.” This cycle turns policies into measurable outcomes and outcomes into assurance.
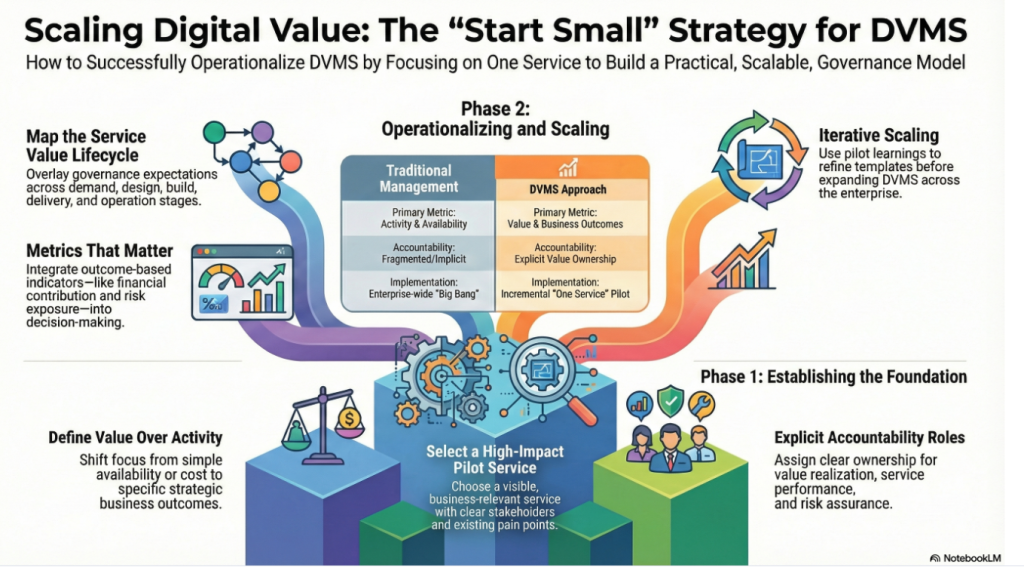
Of course, the scale of this change can seem daunting. That’s why the DVMS FastTrack® approach is so essential. Instead of asking managers to overhaul every process all at once, FastTrack offers a phased plan. Managers start with the most critical MVCs, develop integrated capabilities around them, and show early signs of resilience. Each stage builds confidence, simplifies complexity, and facilitates the transition from an abstract idea to a tangible journey.
This is what distinguishes old thinking from new—the old approach centered on managing fragments: controls, metrics, and reports. The new strategy emphasizes managing the system, focusing on governance intent, integrated capabilities, and assurance evidence. Managers who adopt this shift not only satisfy executive demands but also become drivers of cultural change, embedding resilience into the core of their organizations.
From Comfort to Confidence
Boards are no longer satisfied with knowing which controls exist. They want proof that those controls perform under stress. For managers, the essential question is this: are you presenting artifacts that document activity, or assurance evidence that demonstrates capability? The first provides comfort. The second builds confidence.
The Assurance Mandate series made the case for moving from Governance, Risk, and Compliance (GRC) to Governance, Resilience, and Assurance (GRA). Parts 1 and 2 of this series showed how intent must be translated into capabilities and how frameworks like the NIST Cybersecurity Framework can be operationalized through the Digital Value Management System (DVMS). Part 3 closes the loop: managers must ensure every control generates evidence, and every piece of evidence informs governance. Only then does the system move beyond reassurance to deliver absolute confidence.
Looking Ahead
In the following article in the Assurance in Action Series, we will explore culture. Even the best frameworks, systems, and evidence fall short when organizational culture hampers escalation, discourages transparency, or punishes accountability. We will examine how managers can cultivate a culture that fosters resilience rather than eroding it.
About the Author

Dave is the Executive Director of the DVMS Institute.
Dave spent his “formative years” on US Navy submarines. There, he learned complex systems, functioning in high-performance teams, and what it takes to be an exceptional leader. He took those skills into civilian life and built a successful career leading high-performance teams in software development and information service delivery.
Digital Value Management System® (DVMS) Cyber Resilience Professional Training
Building a DVMS to Govern, Assure, and Account for Strategic Outcomes and Sustained Operational Resilience in Complex Digital Ecosystems
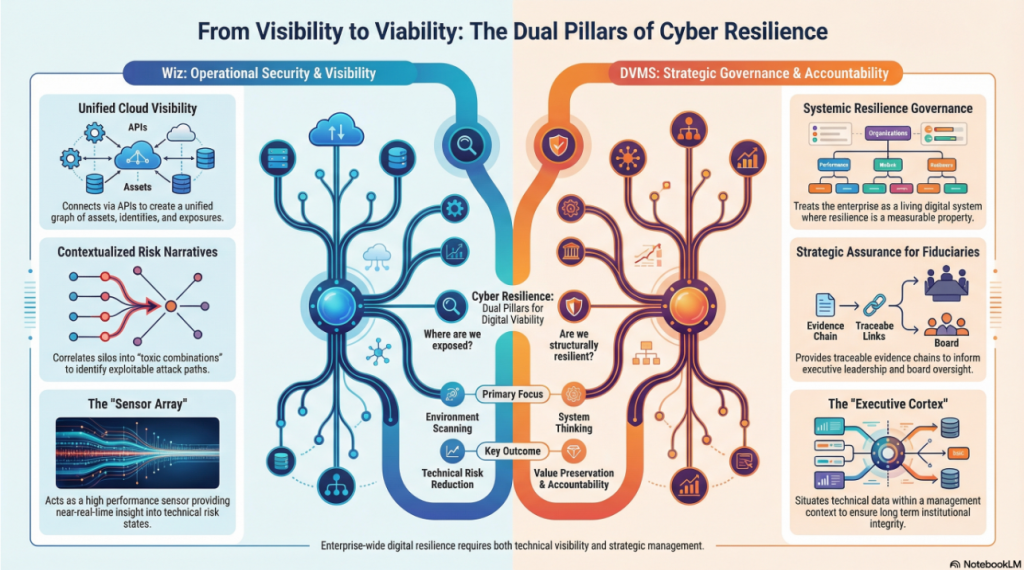
From Visibility to Viability – The Dual Pillars of Cyber Resilience
Explainer Video – The Dual Pillars of Cyber Resilience
As enterprises accelerated their adoption of complex, cloud-native architectures, they encountered a new order of complexity. Infrastructure dissolved into services, workloads became ephemeral, and security boundaries blurred.
In that environment, Wiz emerged as a transformational force in cloud security, offering radical visibility and risk prioritization across multi-cloud ecosystems. At the same time, a broader and more systemic challenge has been unfolding, one that extends beyond misconfigurations and vulnerabilities.
Modern organizations function as dynamic, interconnected digital ecosystems composed of technologies, processes, data flows, and human actors working in constant interaction.
Within this complexity, achieving strategic objectives and sustaining operational resilience, particularly in meeting regulatory obligations, cannot depend on siloed controls or after-the-fact detection mechanisms.
Instead, the fluid and interdependent nature of digital operations requires a cohesive, system-level approach to governance—one that integrates oversight, execution, and accountability into the fabric of how the organization actually operates.
This is the domain in which the Digital Value Management System® (DVMS) operates.
While Wiz redefined how organizations see and secure cloud environments, DVMS is redefining how enterprises govern, assure, and account for strategic outcomes and operational resilience as an integrated dimension of digital business performance.
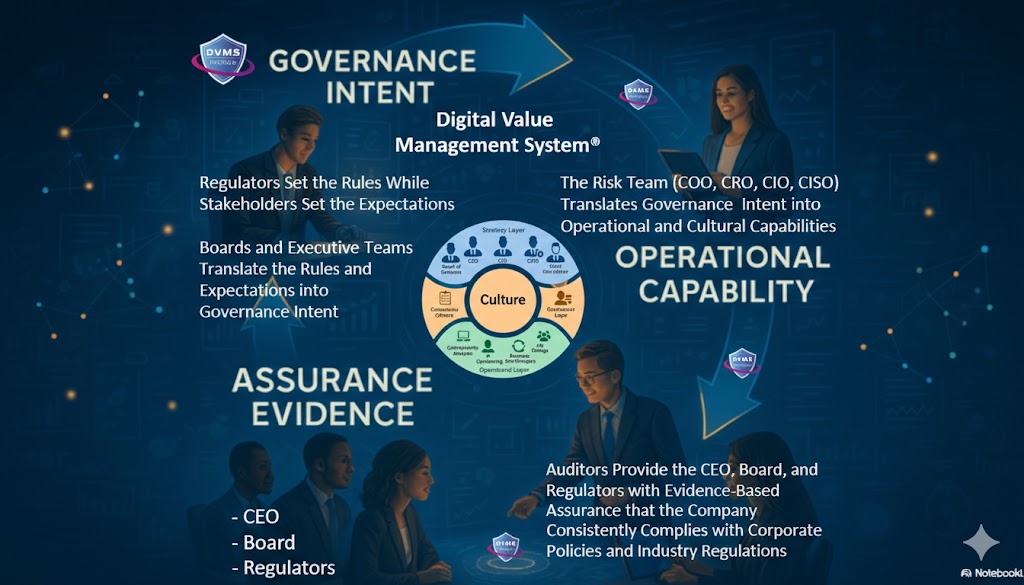
The Digital Value Management System® (DVMS)
Explainer Video – What is a Digital Value Management System (DVMS)
The DVMS is an overlay system that governs, assures, and accounts for strategic outcomes and sustained operational resilience in complex digital ecosystems.
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business performs
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Learning – for governance intent and operational capability fine-tuning
Underpinning this integration are the following DVMS models and approaches:
Create, Protect, and Deliver (CPD) – The CPD Model™ is a systems-based model within the DVMS that links strategy-risk and governance to execution to create, protect, and deliver digital business value as an integrated, continuously adaptive capability.
3D Knowledge (3DK) – The 3D Knowledge Model is a systems-thinking framework that maps team knowledge over time (past, present, future), cross-team collaboration, and alignment to strategic intent to ensure that organizational behavior, learning, and execution remain integrated and adaptive in delivering digital business value.
Minimum Viable Capabilities (MVC) – The Minimum Viable Capabilities (MVCs) model supports the seven essential, system-level organizational capabilities—Govern, Assure, Plan, Design, Change, Execute, and Innovate—required to reliably create, protect, and deliver digital business value in alignment with strategy-risk intent.
Question Outcome / Question Metric (QO/QM) – This approach supports governance as testable intent by defining a clear Question Outcome (QO), the specific value or resilience condition that must be true at a given boundary, and pairing it with one or more Question Metrics (QM) that provide observable, decision-relevant evidence that the system can actually create, protect, and deliver that outcome under complex, living system operating conditions
These models and approaches work together to enable three organizational capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Benefits – Organizational and Leadership
Explainer Video – DVMS Organization and Leadership Benefits
Instead of replacing existing operational frameworks and platforms, the DVMS elevates them, connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
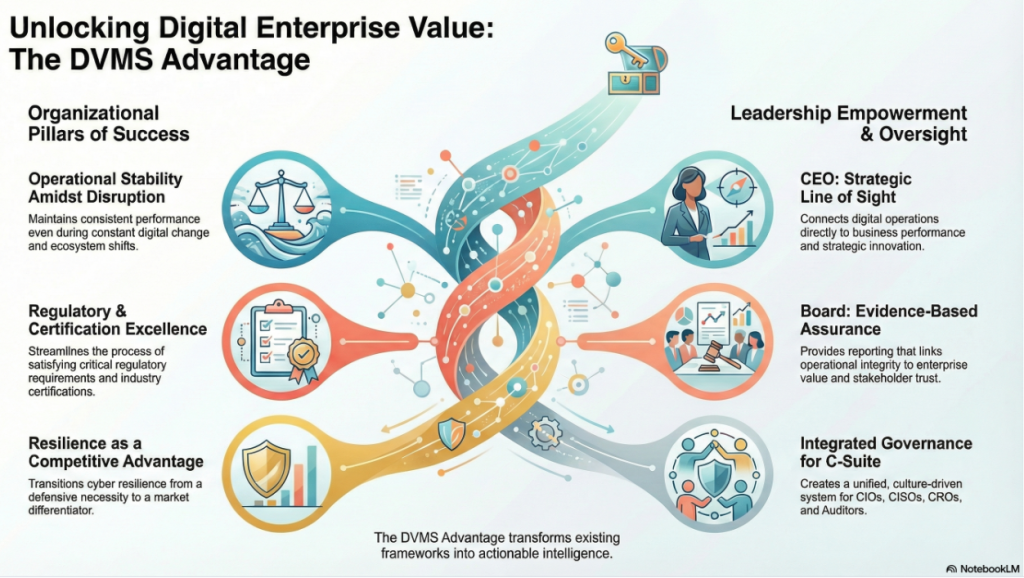
By adopting a DVMS, enterprises are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors, an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability.
DVMS – Accredited Certification Training Program
Explainer Video – The DVMS Training Pathway to Cyber Resilience
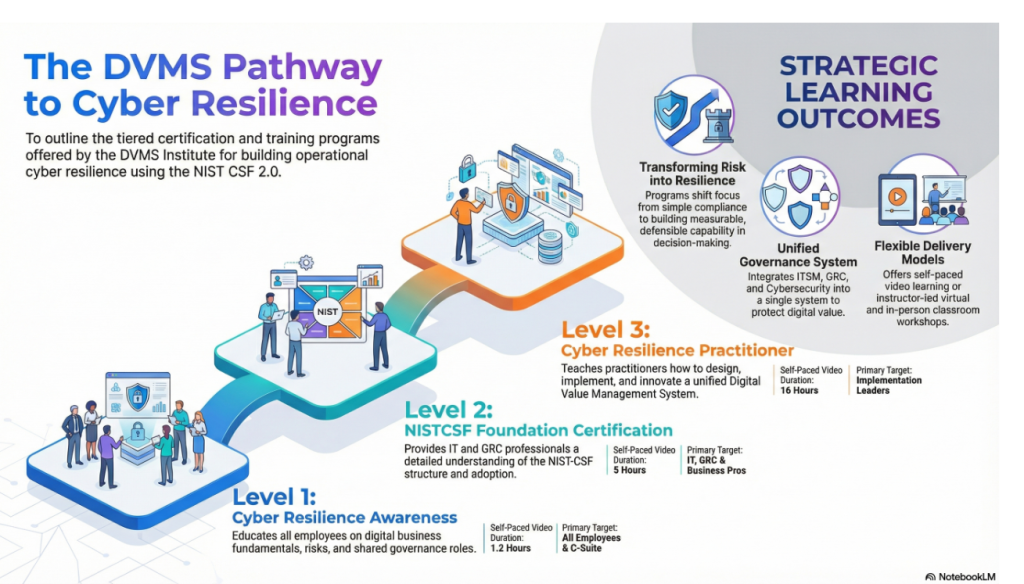
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to integrate fragmented systems into a unified, culture-driven governance and assurance system that accounts for the resilience of digital value within a living digital ecosystem.
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS NISTCSF Cyber Resilience Foundation Certification Training
The DVMS NISTCSF Cyber Resilience Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
A FastTrack Approach to Launching Your DVMS Program
Explainer Video – Scaling a DVMS Program
The DVMS FastTrack approach is a phased, iterative approach that helps organizations mature their DVMS over time, rather than trying to do everything simultaneously.
This approach breaks the DVMS journey into manageable phases of success. It all starts with selecting the first digital service you want to make cyber resilient. Once that service becomes resilient, it becomes the blueprint for operationalizing cyber resilience across the enterprise and its supply chain.
DVMS Institute White Papers – The Assurance Mandate Series
Explainer Video – From Compliance Rituals to Evidence-Based Resilience
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
The Assurance Mandate Paper explains why traditional compliance artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved