The DVMS-CPD and the HITRUST Threat Adaptive Model – A Synergistic Approach to HITRUST Common Security Framework (CSF) Maturity Certification
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
The Digital Value Management System (DVMS) Create, Protect, and Deliver (CPD) model aligns powerfully with the HITRUST Threat Adaptive Model, providing a synergistic approach to digital governance, resilience, and assurance in a constantly evolving threat landscape. Both solutions are grounded in continuous improvement, adaptability, and proactive risk management. Together, they create a unified structure that enables organizations to dynamically manage digital risk, optimize controls, and ensure compliance, all while protecting digital value and client trust.
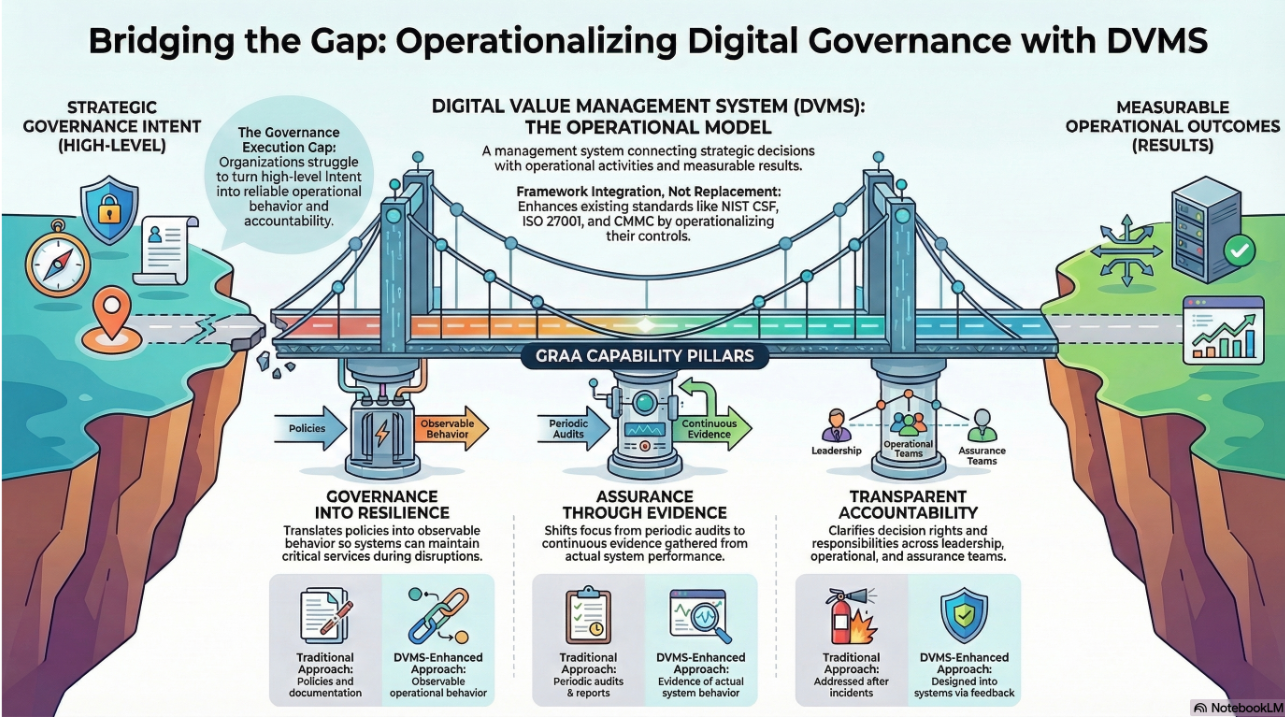
In essence, the DVMS CPD Model provides the operational engine that enables organizations of any size, scale, or complexity to execute the principles and requirements of the HITRUST Threat Adaptive Model. It turns high-level guidance into a repeatable, evidence-based cycle of governance, risk management, control validation, and assurance.
Where HITRUST sets the strategic imperative for adaptive, risk-informed cybersecurity and compliance, CPD delivers the structured execution overlay system that ensures those principles are profoundly and dynamically embedded into everyday business practices. Together, these two models empower organizations not just to comply or respond but to lead proactively in securing their digital futures.
Below is a breakdown of how the DVMS-CPD Model enables the digital business outcomes necessary to achieve HITRUST CSF Certification
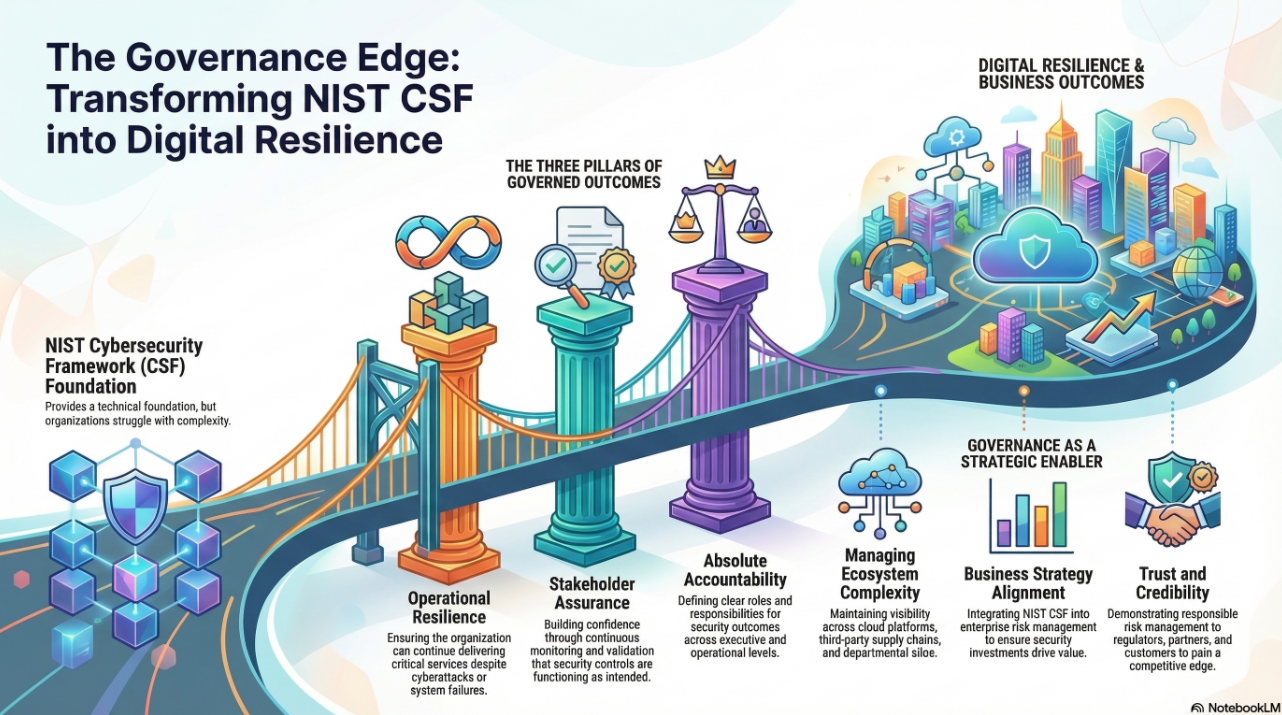
The HITRUST Threat Adaptive Model is designed to evolve security and compliance programs beyond static checklists and periodic audits. It emphasizes real-time risk intelligence, control effectiveness monitoring, and dynamic assurance based on threat activity and risk posture.
The DVMS CPD Model complements this by offering a continuous, iterative governance overlay system that integrates risk classification, asset and service mapping, control design, testing, and performance feedback loops directly into operational planning and delivery cycles. Essentially, where the HITRUST model defines the “what” and “why” of threat-adaptive governance, the DVMS CPD defines the “how.”
The HITRUST Threat Adaptive Model objective is based on ongoing, evidence-based assurance.
The DVMS CPD Model’s focus on continuous planning and delivery ensures that threat intelligence, control validation, and business alignment are not one-time efforts but embedded into the organization’s daily rhythm. With CPD, organizations can plan, monitor, test, and adapt their controls based on current threat data and business needs rather than waiting for annual reviews or audit cycles. This creates a living risk posture that adjusts as threats emerge, technologies evolve, and business priorities shift.
The HITRUST Threat Adaptive Model is based on the goal of adaptive governance through critical service mapping and digital value prioritization.
The DVMS CPD Model strengthens HITRUST’s goal of adaptive governance through critical service mapping and digital value prioritization. In CPD, critical digital services and assets are continuously identified, classified, and linked to the organizational value they support. This mapping allows for risk-prioritizing threat adaptive responses—a principle HITRUST promotes as foundational to maintaining meaningful security postures in high-velocity digital environments. When integrated with HITRUST’s threat intelligence, CPD enables organizations to make smarter decisions about where to apply or scale security controls based on business-critical dependencies.
The HITRUST Threat Adaptive Model expects organizations to reevaluate their controls as threat evolve which also includes, emerging vulnerabilities, and environmental changes
The DVMS CPD operationalizes the HITRUST concept of dynamic control selection and validation. . The DVMS CPD Model supports this through real-time control performance monitoring, test-driven assurance loops, and risk-performance feedback into planning cycles. This turns control management into a dynamic, learning-driven process, ensuring the proper controls are applied at the right time and context.
The HITRUST Threat Adaptive Model promotes risk-based, continuous assurance that reduces reliance on traditional audit methods
The DVMS CPD Model aligns with this by embedding assurance into delivery practices. Rather than performing assurance as an afterthought, CPD ensures that control testing, risk assessment, and evidence collection are part of day-to-day operations. This makes assurance faster, more accurate, and more reflective of current realities, supporting HITRUST’s vision of adaptive trustworthiness that can be demonstrated continuously to stakeholders and regulators.
The HITRUST Threat Adaptive Model views that adaptive security cannot be siloed but must be a shared enterprise capability
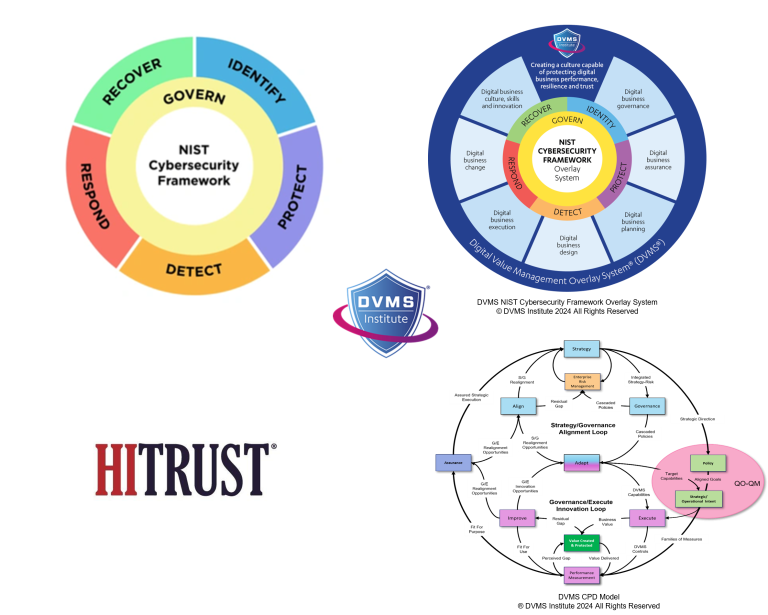
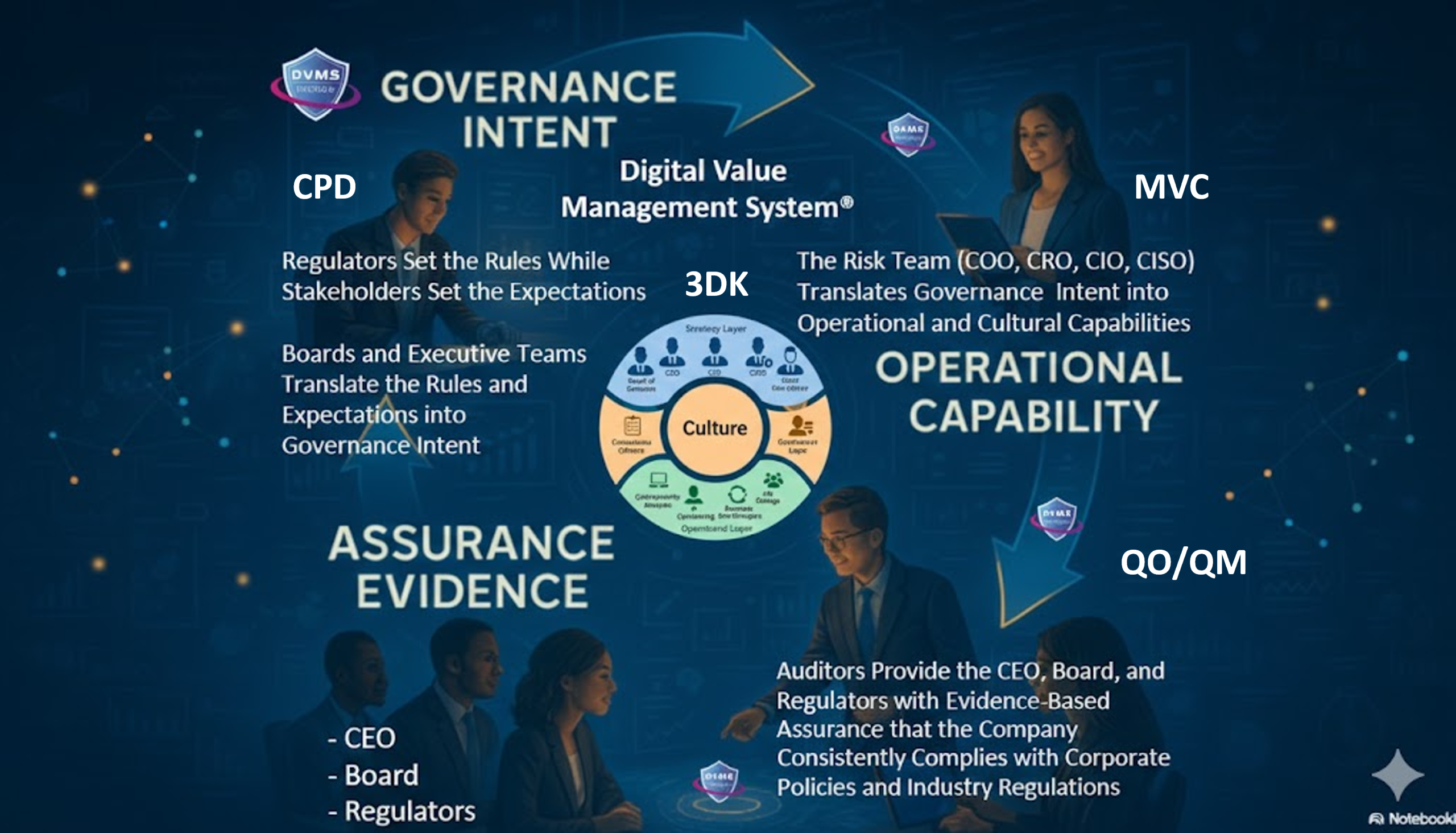
The DVMS CPD model builds structures for collaborative governance across IT, risk, compliance, operations, and business teams.. The DVMS CPD 3D governance operating model underpinned by a 3D Knowledge Model, formalizes this communication and collaboration, enabling the integration of HITRUST’s threat-adaptive practices into strategic planning, service delivery, and value protection processes enterprise-wide.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
DVMS Institute is a renowned provider of accredited (APMG International), Assured (NCSC-GCHQ-UK), and Recognized (DHS-CISA-NICCS-USA) NIST Cybersecurity Framework, Digital Value Management System® body of knowledge publications, certification trainings, assessment platforms and real-life desktop simulation trainings.
The Institute’s NIST Cybersecurity Framework Digital Value Management System® certified training programs teach businesses of any size, scale, or complexity the skills to build a Performance Driven Overlay System for Cyber Resilience capable of anticipating and mitigating the systemic risk digital businesses face today.
By embedding systemic risk management into strategic decision-making and aligning it with employee cultural values, organizations can build resilience—a dynamic capability to withstand digital business disruption and comply with any cybersecurity regulation (SEC, UK, DORA, NIS2, SAMA, SOCI, IMO, etc.) or maturity model mandates (HITRUST, CMMC, C2M2 etc.).
® DVMS Institute 2024 All Rights Reserved