Assurance Is Operational Evidence, Not Compliance Artifacts– The GRAA Management Series Part 3
David Nichols – Co-Founder and Executive Director of the DVMS Institute
Managers do not wake up wanting more dashboards, more templates, or another quarterly evidence scramble. We want two things. We want to run our services with confidence, even when conditions change. And we want to be able to prove, to ourselves and to others, that our decisions were reasonable and that our systems behaved as intended. That is what assurance is supposed to deliver.
Yet in many organizations, assurance has come to mean something else. It has come to mean assembling artifacts that demonstrate our intention to be in control. In the moment, managers can feel how fragile that is because the artifacts do not always translate into operational behavior.
This is not a criticism of GRC or audit. It is a recognition of how the world has changed. Much of traditional assurance practice evolved when systems were less coupled, dependencies were more visible, and controls could be evaluated under relatively static conditions. In modern digital operations, assurance must keep pace with dynamic behavior.
That is the thread you started in the GRAA Leadership Series – Part One, “Why Our GRC Investments Aren’t Delivering Resilience… and Everyone Feels It.” The mismatch is not that GRC is pointless; it is that artifact maturity does not necessarily produce resilient behavior, and everyone can feel it.
This article explores how managers can bridge that gap practically. We do it by treating assurance as operational evidence, rather than a mere formality. We still respect artifacts and support audit. We simply stop pretending that artifacts are proof. Evidence is proof.
The manager’s view of assurance
Assurance is the ability to demonstrate that the system can perform as claimed within defined boundaries, under normal conditions, and under stress. That is a very different statement from “We have a policy” or “We mapped our controls.” Those things matter. They are not assured. They are intent and structure. Assurance requires evidence of behavior.
Managers instinctively understand the difference. If you have ever been asked to “give confidence” during a disruption, you know that nobody really wants a document. They want answers to questions like:
- Are we still inside tolerance?
- If we are not, do we have a controlled degrade mode?
- Do we know what to restore first?
- Can we verify integrity, not just availability?
- Are we coordinated across teams and suppliers?
Those are assurance questions. They are behavior questions.
This is also where your GRAA Leadership Series – Part Seven, “You Do Not Need More Dashboards,” connects directly to management practice. Dashboards can be helpful. They can also create false comfort when they show status without proving behavior or when they summarize data without revealing the system’s real constraints and couplings.
Managers do not need more dashboards. We need evidence we can trust, and we need it in a form that supports decisions.
Artifacts still matter, but they just are not proof.
It is worth being explicit about this because it maintains a constructive tone. Artifacts are important. Policies, procedures, control mappings, risk registers, and continuity plans have real value. They codify expectations, define accountability, and establish repeatable practices. Auditors need them. Regulators often require them. Leaders need them to delegate.
The problem is not artifacts. The problem is treating artifacts as if they were operational evidence. A continuity plan that has never been rehearsed is not evidence. A control mapping that is not tied to observable behavior is not evidence. A policy that nobody can execute under pressure is not evidence. Managers often struggle when asked to certify confidence based solely on intent. The way out is to connect artifacts to evidence, so your assurance story is grounded in reality.
This also aligns with the GRAA Leadership Series – Part Two, “Your Organization Doesn’t Have a Framework Problem: It Has an Overlay Problem.” Artifacts often multiply because frameworks multiply. An overlay approach reduces noise by focusing on how the system actually operates. For managers, that translates into a more straightforward question: “What evidence shows we can sustain outcomes and recover predictably?”
DVMS makes assurance practical because it runs on Create, Protect, Deliver
DVMS helps because it anchors assurance to how work flows through the enterprise rather than keeping it in a separate lane.
In Create, the assurance question is whether the outcome is clear and whether tolerances are explicit. If the organization cannot describe what it is trying to sustain, it cannot provide assurance.
In Protect, the assurance question is whether constraints and unacceptable harm are explicitly stated and whether the system has been designed to avoid or limit that harm.
In Deliver, the assurance question is whether the operation can behave as intended. Can you detect drift, make decisions within boundaries, execute degrade modes, recover in sequence, and verify integrity?
This resonates with Thriving on the Edge of Chaos: Managing at the Intersection of Value and Risk in the Digital Era. The Thriving book makes the inseparability of value and risk very practical. Managers experience it as trade-offs. DVMS provides a structure for those trade-offs and a way to gather evidence that the trade-offs are being managed within boundaries.
The evidence chain: how managers make assurance real
A good assurance story is not a stack of artifacts. It is an evidence chain that links intent to behavior. Here is the simplest chain I have found that managers can maintain without creating a new bureaucracy. Start with intent. What outcome matters, and why is it critical?
- Then define boundaries. What tolerances define acceptable performance and unacceptable harm? This ties directly to Part 1 of this series.
- Then define the expected behaviors. When tolerances are threatened, what do we do? How do we degrade? How do we recover? How do we verify??
- Then capture operational evidence. What data, logs, test results, exercises, incident timelines, and change outcomes demonstrate that the behaviors actually occurred??
- Then close the loop. What did we learn, and how did we update the boundaries or behaviors? Evidence without improvement is just history. Assurance requires learning.
This chain creates something powerful for managers. It makes assurance a byproduct of operating, not a quarterly scavenger hunt.
You can see how this complements the leadership series without repeating it. The GRAA Leadership Series – Part Four, “Seeing the System, A 3D View of Leadership, Structure and Behavior,” focuses on alignment and visibility. The manager’s translation is that evidence must connect those three dimensions. Intent without structure creates frustration. Structure without behavior creates paper confidence. Behavior without intent creates local optimization. Evidence is the glue.
What operational evidence looks like in practice
Managers often ask, “What counts as evidence?” A helpful rule is this: evidence should show what happened, when it happened, who made the decision, what they knew at the time, what action was taken, what outcome followed, and what verification confirmed that the system was safe to continue. That sounds like a lot until you realize much of it already exists in modern operations. The problem is that it is scattered, inconsistent, or not tied to the boundaries you have defined.
Operational evidence can include incident timelines, change records with rollback outcomes, restore test results, integrity check results, alerting and detection metrics, escalation logs, capacity and performance variance trends, and supplier performance evidence. It also includes evidence from rehearsals and tabletop exercises, especially those that validate, degrade, and recover behaviors.
This is where the tone matters. We are not trying to drown managers in data. We are trying to identify a minimum evidence set that supports confidence. If you choose a small number of high-value evidence types, keep them current, and tie them to boundaries, you can answer most executive and audit questions quickly, without drama.
The minimum evidence that managers should maintain for a critical service
Every enterprise is different, but the manager pattern is stable. A minimum evidence portfolio answers five assurance questions.
- Can we detect drift before customers do?
- Can we decide quickly, inside boundaries?
- Can we recover predictably, in a defined sequence?
- Can we verify integrity and safety before declaring normal?
- Can we show learning and improvement over time?
You can operationalize those questions with a handful of evidence-driven measures and artifacts.
Detection evidence can include time-to-detect, alert fidelity, and the rate of near-misses identified early enough to prevent impact. It can also include proof that monitoring covers the proper boundary conditions, not just component health.
Decision evidence can include time-to-decision during incidents, clarity of decision rights, and a brief record of the rationale for significant decisions, especially when trade-offs were made. Managers do not need to write essays. A few sentences that link the decision to tolerance and observed signals are usually sufficient.
Recovery evidence can include time-to-recover within tolerance, restored test success rates, rollback success rates, and proof that recovery sequencing is understood and practiced. A good recovery story is not “we recovered”; it is “we recovered in order, and we verified as we went.”
Integrity and safety evidence can include verification steps and results. These checks confirm the service is trustworthy, not just online. Think of data reconciliation, integrity validation, access validation, and functional verification of the outcome.
Improvement evidence can include the changes made as a result of incidents and drills, along with proof that those changes reduced recurrence or impact. This is the part that builds long-term trust with leadership and audit partners, as it demonstrates that the organization is learning, not just complying.
Managers often already track parts of this. The shift is to tie the evidence portfolio to a Boundary Card and keep it current through everyday work. When you do that, assurance becomes durable.
A manager scenario: the audit request that did not create panic
Let’s consider a scenario many managers recognize. A customer, a regulator, or internal audit requests assurance that a critical service can recover within a defined time and that data integrity will be maintained. This request often arrives after a public incident in your industry, which increases the urgency.
In a traditional artifact-driven environment, the team scrambles. People pull policies, diagrams, and old test results. Everyone argues over which documents are “official.” Answers are slow, which erodes trust, even when the team is capable of providing them.
In an evidence-driven environment, the response differs. The manager pulls the service’s Boundary Card. It clearly states the outcome, tolerances, decision rights, and escalation triggers. It links to the Minimum Evidence Portfolio. The portfolio includes the most recent restore test result with integrity verification, the most recent rehearsal outcome, and the incident timeline from the most recent relevant disruption. It also includes what changed as a result and the next scheduled rehearsal.
The audit partner is not just handed documents. They are shown an evidence chain. The manager can calmly say, “Here is the tolerance, here is our evidence we can recover within it, here is how we verify integrity, and here is how we refresh this evidence.”
Notice what happened. The enterprise did not become resilient as a result of the audit. The audit became less painful because resilience was already being practiced and evidenced. That is the positive relationship we are aiming for. Audit is not the enemy. Audit becomes the forcing function that rewards disciplined operations, and disciplined operations naturally produce evidence.
How to shift from artifact-first to evidence-first without starting a war
Managers are often cautious here because we do not want to step on toes. We rely on GRC, security, and audit teams. The goal is alignment, not conflict. A few good management moves help.
First, frame the shift as making assurance easier and more defensible, not as criticizing current practice. Say, “We want evidence that reduces the scramble and increases confidence.” Most people will agree with that.
Second, invite GRC and audit partners to participate in setting boundaries and defining evidence. They often know what external stakeholders request and can help you design evidence-based expectations that satisfy oversight while remaining operationally realistic.
Third, keep the initial scope small. Pick one critical service or one outcome. Build a Boundary Card and a minimum evidence portfolio. Run one rehearsal. Use what you learn to refine. When you demonstrate success, others will want it.
Fourth, treat evidence as a product of everyday work. If the evidence portfolio requires special effort to maintain, it will decay. The evidence should be gathered from operational routines, including change readiness assessments, incident reviews, restoration testing, supplier evaluations, and periodic drills.
Fifth, close the loop. Evidence becomes assurance when it drives improvement. If a rehearsal reveals a seam, fix it, update the boundary, and record the change. That record becomes part of the evidence chain.
These steps align with what you are already advancing in the leadership series. The GRAA Leadership Series – Part Five, “From Chaos to Capability,” explores the transition from reactive chaos to deliberate capability. Evidence shows that capability exists, not just intent.
Assurance as a management habit
A helpful way to think about assurance is that it is not a report, but a mindset. It is a habit to define tolerances. It is the habit of rehearsing degrade and recover behaviors. It is the habit of recording decisions and linking them to signals. It is the habit of verifying integrity before declaring normal. It is a habit of learning and staying updated. When managers build these habits into delivery, assurance stops being a special event. It becomes the natural output of how the system is run.
This also sets you up for the next article in this management series, where accountability takes center stage. Because once you have boundaries and evidence, accountability becomes fair. It becomes about decision rights and obligations, not blame.
A simple move you can make before your next assurance request.
If you want to apply this immediately, here is a manager-scale starting point. Pick one critical service or outcome. Use the Boundary Card approach from Part One to make tolerances and decision rights explicit. Use the degrade-and-recover play approach from Part Two to define behaviors and verification points. Then define a minimum evidence portfolio that answers the five assurance questions: detect, decide, recover, verify, and improve.
Do not overbuild it. Build the smallest version that lets you respond to a serious assurance request without panic. Then schedule one short rehearsal. Validate the playbook and the evidence capture. Update what needs updating.
If you can do that for one outcome and keep the evidence current, you will feel the difference. You will run with more confidence. You will communicate more clearly upward. And when the audit arrives, you will be ready because the evidence will already exist.
In Part 4 – Accountability That Works Under Pressure, we will take the next step and discuss how accountability that works under pressure enables speed and learning rather than blame, and how DVMS helps managers align decision rights and evidence ownership across Create, Protect, and Deliver.
About the Author

Dave is the Executive Director of the DVMS Institute.
Dave spent his “formative years” on US Navy submarines. There, he learned complex systems, functioning in high-performance teams, and what it takes to be an exceptional leader. He took those skills into civilian life and built a successful career leading high-performance teams in software development and information service delivery.
Digital Value Management System® (DVMS)
Organizations don’t experience catastrophic digital breaches because they lack the frameworks and systems to create, protect, and deliver the value stakeholders and regulators expect.
They suffer breaches because those frameworks and systems operate in silos and fail at their boundaries when placed under real-world stress.
The Digital Value Management System® (DVMS) integrates fragmented frameworks and systems such as NISTCSF, GRC, ITSM, DevOps, and AI into a unified living overlay system that:
- Enables Adaptive Governance through risk-informed decision-making
- Sustains Operational Resilience through a proactive and adaptive culture
- Measures Performance Assurance through evidence-based outcomes
- Ensures Transparent Accountability by making intent, execution, and evidence inseparable
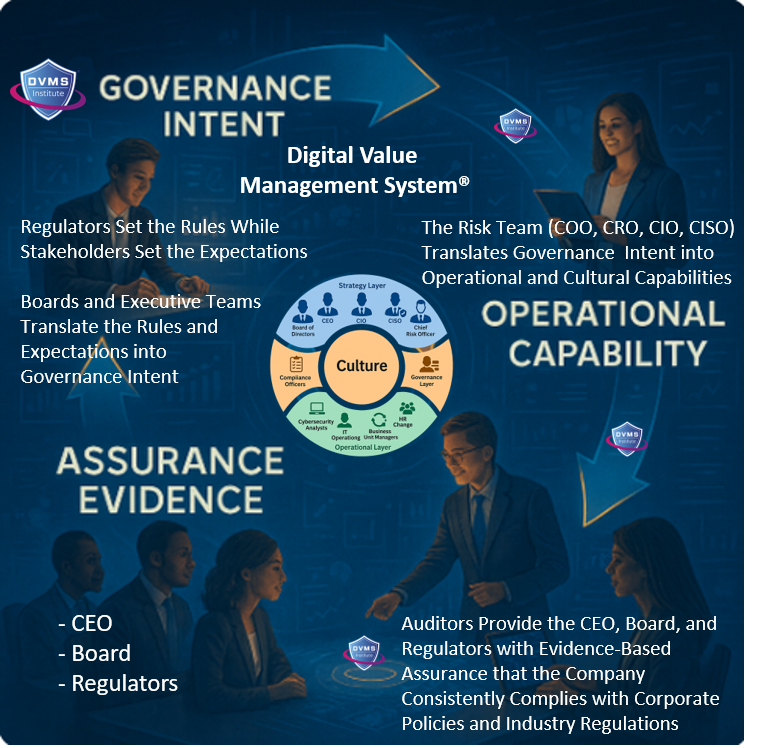
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business actually performs
- Assured Evidence – proof that outcomes are achieved and accountable
Through its MVC, CPD, 3D Knowledge, and FastTrack Models, a DVMS turns this integration into three distinctive capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance—across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Organizational Benefits
Instead of replacing existing operational frameworks, the DVMS elevates them—connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
By adopting a DVMS, organizations are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Leadership Benefits
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors: an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability
DVMS White Papers
The whitepapers below present a coherent progression that shifts organizations from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Collectively, the three papers define a comprehensive system for building and governing resilient digital enterprises, grounded in evidence rather than assumptions.
The Assurance Mandate Paper sets the stage by showing why traditional GRC artifacts provide only reassurance—not evidence—and calls boards to demand forward-looking proof that their organizations can continue to create, protect, and deliver value under stress.
The Assurance in Action Paper elevates the conversation from leadership intent to managerial execution, demonstrating how the DVMS operationalizes resilience by translating outcomes into Minimum Viable Capabilities, connecting frameworks through the Create–Protect–Deliver model, and generating measurable assurance evidence that managers can use to demonstrate real performance rather than activity.
The Governing by Assurance Paper elevates the approach to the policy and regulatory level, showing how DVMS functions as a learning overlay system that links governance intent, operational capability, and verifiable evidence into a continuous loop—enabling regulators, agencies, and enterprises to govern by outcomes rather than checklists and to prove capability with measurable, auditable performance data.
DVMS Cyber Resilience Certified Training Programs
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters a culture that is prepared to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS NISTCSF Foundation Certification Training
The DVMS NISTCSF Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters IT, GRC, Cybersecurity, and Business professionals with the skills to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
This investment fosters IT, GRC, Cybersecurity, and Business practitioners with the skills to assess, design, implement, operationalize, and continually innovate a Digital Value Management System® program that operationalizes a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved