Leadership Mandate – Hack Your Enterprise Culture, Capabilities, and Skills Before It’s Too Late
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Introduction:
In today’s volatile digital economy, organizations cannot rely solely on traditional management practices to ensure resilience, competitiveness, and accountability. Technologies evolve faster than governance structures, employee skill sets shift rapidly, and organizational cultures often operate in ways leadership does not fully understand. As a result, hidden vulnerabilities emerge not just in cybersecurity systems but across policies, workflows, relationships, and decision-making processes. These vulnerabilities become the cracks through which operational failures, compliance breakdowns, and even cyber threats can quietly enter.
To address this reality, leaders must learn to “ethically hack” their enterprise—not in the technical sense alone, but by probing their culture, examining capabilities, interrogating assumptions, and stress-testing the readiness of people and processes. Leadership’s ability to hack its own organization is now essential for building adaptive, learning-driven enterprises that can thrive in a world of continuous disruption.
Hacking Culture: Revealing the Mindsets and Behaviors that Drive Performance
Culture is often described as “the way things get done around here,” yet many leaders misunderstand how deeply culture shapes digital transformation and operational resilience. Traditional culture assessments—surveys, interviews, engagement scores—provide surface-level insights but rarely reveal how people behave when pressures mount, or systems break.
Ethical governance hacking requires leaders to go deeper. This involves examining the hidden, unspoken elements of culture, including the stories employees tell about the organization, the informal power structures that override policies, the workarounds people develop to compensate for broken processes, and the underlying beliefs that shape risk-taking or avoidance.
Leaders who hack their culture actively test the assumptions embedded in everyday behavior. They observe how teams respond when faced with ambiguous instructions, unexpected changes, or conflicting priorities. By adopting a hacker’s mindset—curious, skeptical, and evidence-driven—leaders uncover cultural weaknesses that traditional assessments miss. These include complacency, silos, mistrust, fear of speaking up, and misalignment between stated values and real behavior. Through hacking culture, leadership gains visibility into what truly drives performance, collaboration, and resilience.
Hacking Capabilities: Mapping What the Enterprise Can Really Do
Organizations routinely overestimate their capabilities. Strategies assume resources that do not exist, transformation programs rely on processes that are not actually followed, and leaders trust capabilities that look strong on paper but fail under stress.
Ethical hacking of enterprise capabilities means testing them—continuously and rigorously—much like a penetration tester evaluates system controls. Leaders must question whether the capabilities their teams claim to have correspond to reality. Do risk assessments influence decision-making, or are they created for compliance checkboxes? Do crisis-response plans work in practice, or do they collapse under pressure? Do service management processes strengthen resilience, or do they create bottlenecks?
Leaders who hack capabilities ask targeted, evidence-driven questions: What are we trying to achieve? How do we know this capability works? What proof do we have? Where are the gaps? This shifts the organization away from assumption-based governance toward outcome-based, validated performance.
Hacking capabilities also involve testing cross-functional linkages—how one capability interacts with another. For example, how does change management influence cybersecurity? How does employee skill development affect operational risk? By probing these systemic relationships, leaders identify misalignments and develop stronger, more integrated capabilities that can adapt to shifting strategic demands.
Hacking Technologies: Understanding the Real Behavior of Digital Systems
Most technology failures are not technical—they are organizational. Systems do not perform as expected because teams misunderstand how they work, rely on outdated processes, or integrate them poorly into daily operations.
Ethical leadership hacking applies the same logic used by cybersecurity professionals who test system weaknesses: continuously stress-test technology assumptions. Leaders must understand not just what technology does, but how it behaves in the real world. This includes uncovering inefficient workflows, misconfigurations, shadow IT, system dependencies, and unvalidated automations. Leaders should also examine how employees interact with technology: Do tools empower teams or restrict them? Are controls user-friendly or burdensome? Are data flows transparent or opaque?
Hacking technology means leaders observe how systems respond to variability, how data is generated and consumed, and how technologies align (or fail to align) with business outcomes. When leaders hack their technology landscape, they expose hidden weaknesses—security gaps, operational fragility, and mismatched expectations—before adversaries or crises exploit them.
Hacking Skill Sets: Closing the Gap Between Employee Capability and Organizational Need
People are the most critical variable in organizational resilience. Yet, leaders often assume that employees possess the necessary competencies simply because they occupy a role, have completed training, or have performed well in the past. Skill sets, however, must evolve continuously as threats, technologies, and business models change.
Ethical hacking of employee skills involves assessing real-world readiness—not through quizzes or annual training modules, but through scenario-based evaluation, live-fire exercises, cross-functional problem-solving, and performance evidence.
Leaders must identify skill gaps that are not visible on résumés or performance reviews—such as critical thinking, collaboration under stress, digital literacy, or the ability to adapt to rapidly evolving threats. Hacking skills involve understanding how employees respond to uncertainty, how they exercise judgment, and how well-equipped they are to execute the organization’s strategy under pressure. By enhancing workforce capabilities, leaders identify where targeted development, reskilling, or structural redesign is necessary to strengthen the enterprise.
The Hacker Mindset: Why Leadership Must Think Like Adversaries
Ethical hacking in leadership is not malicious—it is curious, evidence-driven, and proactive. Great leaders share the mindset of great hackers: they explore systems, look for inconsistencies, test limits, and seek to understand how things work rather than how they are supposed to work. In this sense, hacking becomes a leadership discipline. It helps leaders detect vulnerabilities early, enhance operational integrity, and build cultures committed to continuous improvement. It transforms governance from a static, rule-bound construct into a dynamic system of learning and adaptation. Most importantly, leadership hacking fosters psychological safety by encouraging employees to challenge assumptions, speak up about risks, and participate in collaborative problem-solving. Leaders who model ethical hacking empower their teams to do the same, turning the entire organization into a self-healing, self-improving system.
Conclusion: Hacking the Enterprise as a Path to Operational Resilience
As digital transformation accelerates, organizations face new challenges that demand deeper visibility into their culture, capabilities, technologies, and workforce. Leaders cannot afford to manage based on assumptions, outdated models, or surface-level insights.
Ethical hacking provides a robust methodology for uncovering hidden weaknesses and validating strengths across the entire enterprise. By hacking their own culture, leaders reveal the beliefs and behaviors that shape performance. By hacking capabilities, they separate real effectiveness from imagined competence. By hacking technologies, they expose system behavior and integration gaps. By honing their hacking skill sets, they ensure their people can meet the demands of a dynamic environment. When leaders adopt this mindset, they transform their organizations into adaptive, resilient, and learning-driven enterprises that can withstand disruption and sustain change. Ethical hacking thus becomes not just a technical discipline, but a leadership imperative for the modern age.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
Digital Value Management System® (DVMS)
Training Leaders to Govern Digital Value Outcomes Through Operational Resilience, Performance Assurance, and Transparent Accountability
Despite abundant frameworks and dashboards, leadership still struggles to see how their complex digital system actually behaves at its boundaries under stress.
Leadership intent, structure, and day-to-day behavior are viewed separately, creating fragmented, flat perspectives that hide how real decisions and human responses interact within digital value streams.
As a result, organizations can look well-governed on paper while still experiencing catastrophic events in practice. Without an integrated view, leaders end up managing isolated components and controls rather than governing the system as a whole.
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to integrate fragmented frameworks and systems such as NISTCSF, GRC, ITSM, DevOps, and AI into a unified, living overlay system that:
- Enables Adaptive Governance through risk-informed decision-making
- Sustains Operational Resilience through a proactive and adaptive culture
- Measures Performance Assurance through evidence-based outcomes
- Ensures Transparent Accountability by making intent, execution, and evidence inseparable
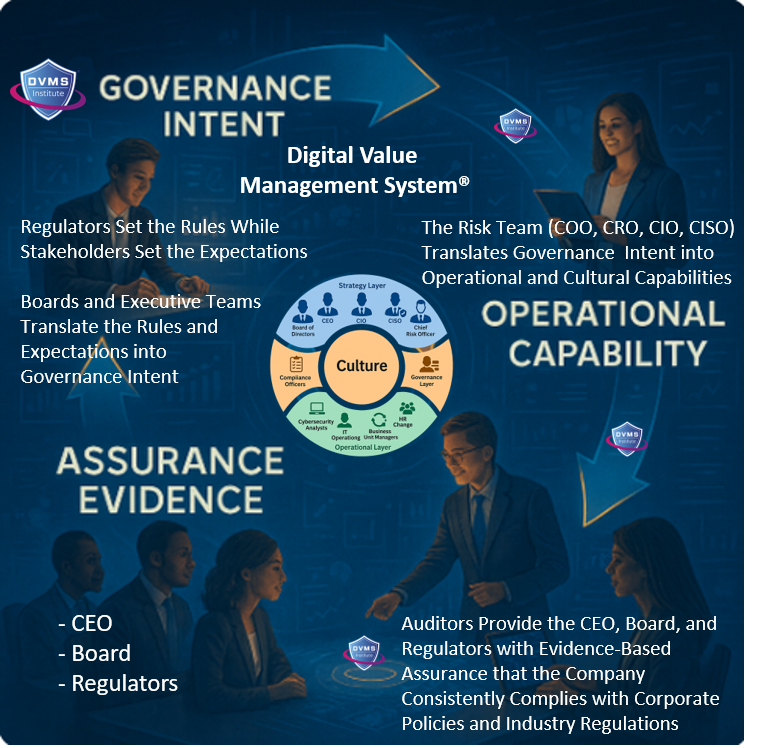
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business actually performs
- Assured Evidence – proof that outcomes are achieved and accountable
Through its MVC, CPD, 3D Knowledge, and FastTrack Models, a DVMS turns this integration into three distinctive capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance—across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Organizational Benefits
Instead of replacing existing operational frameworks, the DVMS elevates them—connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
By adopting a DVMS, organizations are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Leadership Benefits
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors: an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability
DVMS White Papers
The whitepapers below present a coherent progression that shifts organizations from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Collectively, the three papers define a comprehensive system for building and governing resilient digital enterprises, grounded in evidence rather than assumptions.
The Assurance Mandate Paper sets the stage by showing why traditional GRC artifacts provide only reassurance—not evidence—and calls boards to demand forward-looking proof that their organizations can continue to create, protect, and deliver value under stress.
The Assurance in Action Paper elevates the conversation from leadership intent to managerial execution, demonstrating how the DVMS operationalizes resilience by translating outcomes into Minimum Viable Capabilities, connecting frameworks through the Create–Protect–Deliver model, and generating measurable assurance evidence that managers can use to demonstrate real performance rather than activity.
The Governing by Assurance Paper elevates the approach to the policy and regulatory level, showing how DVMS functions as a learning overlay system that links governance intent, operational capability, and verifiable evidence into a continuous loop—enabling regulators, agencies, and enterprises to govern by outcomes rather than checklists and to prove capability with measurable, auditable performance data.
DVMS Cyber Resilience Certified Training Programs
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters a culture that is prepared to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS NISTCSF Foundation Certification Training
The DVMS NISTCSF Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters IT, GRC, Cybersecurity, and Business professionals with the skills to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
This investment fosters IT, GRC, Cybersecurity, and Business practitioners with the skills to assess, design, implement, operationalize, and continually innovate a Digital Value Management System® program that operationalizes a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved