Using a DVMS to “Ethically Hack” An Enterprise NIST, ITSM, GRC, ISO, and ERM Governance and Assurance Programs
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Introduction: The Problem with Framework Fatigue
In an era where organizations are increasingly dependent on digital systems, frameworks such as NIST, ISO, ITSM, GRC, and ERM have become essential components of modern business governance. Yet many companies still struggle to translate these frameworks into real operational value. They are often deployed in silos—compliance in one corner, IT service management in another, risk management somewhere else—resulting in fragmented processes, inconsistent controls, and blind spots that undermine digital value protection and operational resilience.
The DVMS as a Transformative Overlay for Ethical Governance Hacking
The Digital Value Management System (DVMS) offers a transformative alternative. Rather than treating these frameworks as static rulebooks, the DVMS enables organizations to “ethically hack” their internal processes, culture, and systems to uncover gaps that traditional assessments overlook. By applying systems thinking, adaptive leadership, and cultural interrogation, organizations can turn DVMS into a strategic overlay that enhances—and in many ways revolutionizes—their use of NIST, ISO, GRC, ITSM, and ERM to protect organizational digital value and operational resilience.
DVMS as a Dynamic and Adaptive Governance Lens
At its core, the DVMS reframes governance and cybersecurity as dynamic, living systems. It functions as an adaptive lens rather than a prescriptive toolkit, enabling organizations to see how their existing frameworks behave in the real world—not just on paper. The DVMS incorporates seven minimum viable capabilities (Govern, Assure, Plan, Design, Change, Execute, and Innovate) that map onto existing business processes to reveal performance gaps. Instead of adding yet another framework to the mix, it exposes where current frameworks conflict, overlap, or fail to produce intended outcomes. In this way, the DVMS helps organizations “hack” their governance systems the same way ethical hackers probe software—by testing assumptions, stress-testing controls, and exposing systemic weaknesses before adversaries do.
Hacking NIST and ISO: Beyond Documentation to Real-World Behavior
When applied to frameworks like NIST CSF or ISO 27001, the DVMS provides deeper insight into whether the controls organizations believe they have in place are functioning as designed. Many organizations hold a false sense of security based on documented policies or successful audits. The DVMS challenges these assumptions by asking whether controls truly influence behavior, integrate into decision-making, and support resilience. For example, the DVMS “Govern” capability prompts organizations to question whether cybersecurity policies shape daily actions—or simply exist as procedural artifacts. This form of introspection forces leaders to confront the practical effectiveness, not just the formal presence, of their NIST or ISO controls.
Hacking ITSM and GRC: Fixing Misalignments and Invisible Dependencies
In ITSM and GRC environments, the DVMS helps organizations identify and correct structural misalignments and hidden dependencies that undermine risk management. ITSM processes—incident, change, and problem management—often operate independently of GRC risk assessments or ISO control monitoring. The DVMS overlay connects these traditionally siloed systems, revealing how activity in one domain affects risk exposure in another. Using DVMS-driven inquiry, organizations can ask: Are our service workflows reinforcing resilience or inadvertently creating new risks? Are our GRC processes grounded in operational reality or merely in compliance checklists? This systems-level view uncovers failures and strengthens the connective tissue between frameworks.
Strategy-Risk Thinking: Hacking the Organization’s Strategic Blind Spots
The DVMS introduces a powerful paradigm known as strategy-risk thinking. Unlike traditional models that separate strategy and risk, the DVMS insists that the two are inseparable. Ethical hackers identify disconnects between intended function and actual behavior; DVMS teaches organizations to do the same with their strategies. Tools like the DVMS CPD (Create, Protect, Deliver) and 3D Knowledge Models enable organizations to assess whether risk considerations are effectively embedded in their objectives, KPIs, and investments. This mindset converts strategic misalignments into opportunities for improvement rather than latent threats.
Becoming “The Menace Within”: Red Teaming Governance Itself
One of the DVMS’s most innovative contributions is its framing of the organization as “the menace within.” Instead of relying solely on external penetration tests, organizations learn to adopt a threat actor mindset internally. With tools such as Goal-Question-Metric (GQM) and Question-Outcome-Question Metric (QO-QM), teams conduct internal red teaming of their governance structures by asking: What are we trying to achieve? How do we know controls are adequate? What evidence proves that our risk posture matches our intentions? This transforms NIST, ISO, GRC, ERM, and ITSM programs into dynamic systems that continuously adapt and improve.
Cultural Hacking: Transforming the Organizational Mindset
The DVMS emphasizes that actual governance improvement requires cultural transformation. Frameworks such as ISO or NIST often fail not because of poor documentation but because the organizational culture does not support disciplined behavior or shared risk awareness. The DVMS encourages organizations to “hack” their cultural web—analyzing rituals, stories, power structures, and underlying assumptions. This psychological hacking reveals hidden loyalties, conflicts, and outdated beliefs that hinder the effectiveness of NIST, GRC, or ERM initiatives. By promoting psychological safety and cross-functional collaboration, leaders cultivate a culture where employees feel empowered to challenge existing practices and contribute to governance improvement.
Iterative Improvement Through DVMS FastTrack™
In operational practice, organizations adopt the DVMS through iterative cycles such as the DVMS FastTrack™ method. This approach mirrors the iterative nature of ethical hacking—test, learn, adjust. Instead of waiting for annual audits or periodic assessments, organizations continuously refine their governance processes. The DVMS integrates threat intelligence, regulatory updates, and internal performance data into a living system of adaptive governance. As a result, NIST controls become more actionable, GRC efforts become more meaningful, ITSM processes become more resilient, and ERM programs become more accurate in reflecting real-world risks.
Conclusion: From Compliance to Cyber-Consciousness
Ultimately, the DVMS empowers organizations to move beyond compliance toward a state of cyber-consciousness. It transforms NIST, ISO, ITSM, GRC, and ERM programs into cohesive, adaptive systems that can evolve with the organization and the evolving threat landscape. By ethically hacking themselves—intelligently and continuously—organizations shift governance from a static obligation to a strategic advantage. They discover vulnerabilities before adversaries do, strengthen controls through cultural alignment, and build a continuous feedback loop that elevates digital trust and operational reliability.
By becoming the ethical hackers of their own governance systems, organizations unlock the full potential of their existing frameworks and cultivate a resilient culture that can thrive in an age of digital chaos.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
Digital Value Management System® (DVMS)
Training Leaders to Govern Digital Value Outcomes Through Operational Resilience, Performance Assurance, and Transparent Accountability
Despite abundant frameworks and dashboards, leadership still struggles to see how their complex digital system actually behaves at its boundaries under stress.
Leadership intent, structure, and day-to-day behavior are viewed separately, creating fragmented, flat perspectives that hide how real decisions and human responses interact within digital value streams.
As a result, organizations can look well-governed on paper while still experiencing catastrophic events in practice. Without an integrated view, leaders end up managing isolated components and controls rather than governing the system as a whole.
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to integrate fragmented frameworks and systems such as NISTCSF, GRC, ITSM, DevOps, and AI into a unified, living overlay system that:
- Enables Adaptive Governance through risk-informed decision-making
- Sustains Operational Resilience through a proactive and adaptive culture
- Measures Performance Assurance through evidence-based outcomes
- Ensures Transparent Accountability by making intent, execution, and evidence inseparable
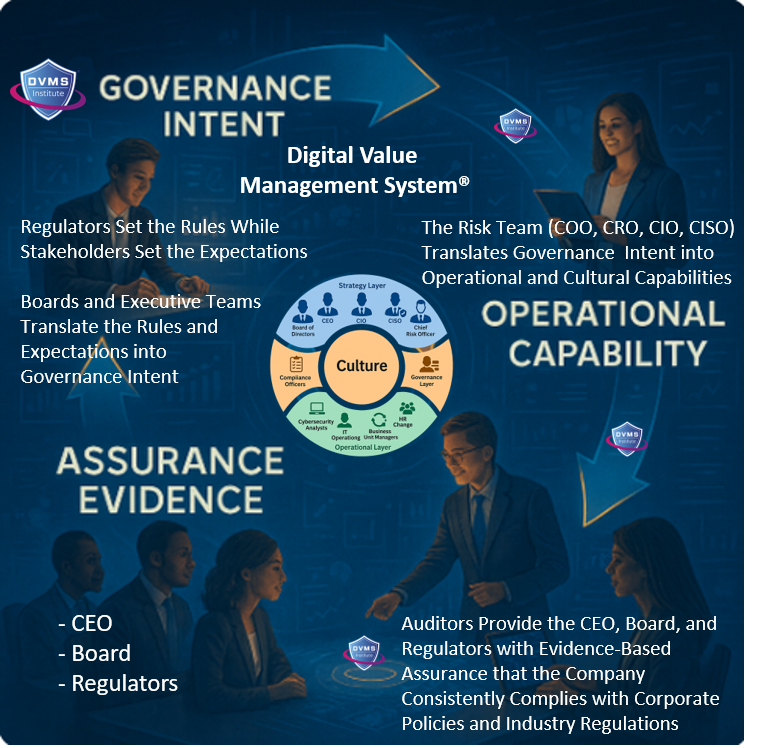
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business actually performs
- Assured Evidence – proof that outcomes are achieved and accountable
Through its MVC, CPD, 3D Knowledge, and FastTrack Models, a DVMS turns this integration into three distinctive capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance—across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Organizational Benefits
Instead of replacing existing operational frameworks, the DVMS elevates them—connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
By adopting a DVMS, organizations are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Leadership Benefits
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors: an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability
DVMS White Papers
The whitepapers below present a coherent progression that shifts organizations from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Collectively, the three papers define a comprehensive system for building and governing resilient digital enterprises, grounded in evidence rather than assumptions.
The Assurance Mandate Paper sets the stage by showing why traditional GRC artifacts provide only reassurance—not evidence—and calls boards to demand forward-looking proof that their organizations can continue to create, protect, and deliver value under stress.
The Assurance in Action Paper elevates the conversation from leadership intent to managerial execution, demonstrating how the DVMS operationalizes resilience by translating outcomes into Minimum Viable Capabilities, connecting frameworks through the Create–Protect–Deliver model, and generating measurable assurance evidence that managers can use to demonstrate real performance rather than activity.
The Governing by Assurance Paper elevates the approach to the policy and regulatory level, showing how DVMS functions as a learning overlay system that links governance intent, operational capability, and verifiable evidence into a continuous loop—enabling regulators, agencies, and enterprises to govern by outcomes rather than checklists and to prove capability with measurable, auditable performance data.
DVMS Cyber Resilience Certified Training Programs
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters a culture that is prepared to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS NISTCSF Foundation Certification Training
The DVMS NISTCSF Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
This investment fosters IT, GRC, Cybersecurity, and Business professionals with the skills to operate within a system capable of transforming systemic cyber risks into operational resilience.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
This investment fosters IT, GRC, Cybersecurity, and Business practitioners with the skills to assess, design, implement, operationalize, and continually innovate a Digital Value Management System® program that operationalizes a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved