Outcomes Over Compliance – Using NIST-CSF 2.0, and a DVMS® to Enable Cyber Operational Resilience Outcomes
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
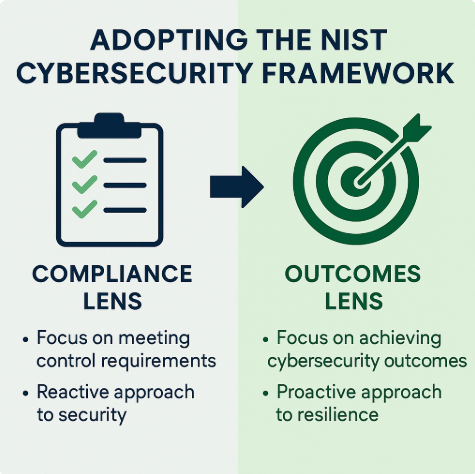
The Problem with the Compliance Mindset
For years, many organizations have defaulted to treating cybersecurity as a compliance exercise — a series of controls to implement, audits to pass, and checkboxes to tick. This mindset has created a false sense of security: merely aligning with a control catalog or meeting regulatory minimums will ensure resilience. However, real-world data breaches and operational failures repeatedly reveal the limitations of compliance-driven approaches. The root causes are often not technical but strategic: leadership gaps, cultural inertia, unclear risk ownership, or fragmented governance.
The compliance mindset tends to narrow the focus to what is mandated, overlooking what is mission critical. It can foster a culture where cybersecurity is seen as the responsibility of the IT department rather than a shared enterprise imperative. This outlook inhibits innovation, stifles responsiveness to threats, and perpetuates fragmented, siloed approaches to risk management.
The Evolution of the NIST Cybersecurity Framework (NIST-CSF) and the Digital Value Management System® (DVMS)
The NIST CSF 2.0 and the DVMS release mark a pivotal shift. No longer limited to critical infrastructure, the Framework now applies to all sectors and all sizes of organizations. Most notably, it explicitly refocuses attention on desired cybersecurity outcomes, rather than prescriptive control implementations. The Framework is structured around six Functions — Govern, Identify, Protect, Detect, Respond, and Recover — which organize high-level outcomes that can be tailored to each organizational mission and risk tolerance.
This outcomes-centric architecture enables organizations to align cybersecurity with enterprise risk management. It facilitates a move away from “what are we required to do?” toward “what must we achieve to protect and sustain our mission?”
Outcomes Over Compliance: A Governance Imperative
The “Govern” Function, newly added in CSF 2.0, underscores the importance of embedding cybersecurity within enterprise strategy, culture, and governance. It directs organizations to establish cybersecurity risk management expectations, roles, and authorities, elevating cybersecurity from a control domain to a board-level concern.
Governance outcomes aren’t achieved by adopting a policy alone; they are realized through organizational behaviors, decision-making processes, and cultural norms. They require leadership engagement, cross-functional collaboration, and a deep understanding of digital business value and how it’s protected.
Adopting CSF 2.0 with an outcomes lens means embedding cybersecurity into strategic governance processes — integrating it into how value is created, protected, and delivered.
Strategic Risk and the DVMS Overlay
The Digital Value Management System® (DVMS) NIST Cybersecurity Framework certified training from the DVMS Institute advances this idea by linking cybersecurity directly to strategic outcomes and business value. It frames cybersecurity as an organizational responsibility, not merely a technical one. By adopting a “strategy-risk” perspective, the DVMS compels organizations to consider cybersecurity in the context of mission performance, stakeholder value, and operational resilience.
Under this model, cybersecurity is a byproduct of managing digital business risk. Organizations must continuously adapt to evolving threats, shifting regulations, and changing stakeholder expectations. A compliance lens is reactive and static; an outcomes lens is dynamic and proactive.
Profiles and Tiers: Tools for Outcome-Centric Planning
CSF 2.0’s Profiles and Tiers are practical tools for operationalizing an outcomes focus. An Organizational Profile defines the current and target state of cybersecurity outcomes, while Tiers describe the maturity and rigor of risk governance practices.
The use of Profiles shifts the conversation from “Are we compliant?” to “Are we achieving the outcomes that matter most to our organization, customers, and regulators?” Profiles allow organizations to tailor the CSF to their unique mission, threat landscape, and business context, not someone else’s checklist.
Tiers provide a maturity-based view of how integrated and adaptive an organization’s cybersecurity practices are. They help leaders frame cybersecurity as a continuum of improvement, not a static state of control implementation.
The Cultural Shift: Seeing Cybersecurity as Value Protection
At the heart of the outcomes-based approach is a fundamental cultural shift. Cybersecurity must no longer be seen as the “cost of doing business” or a technical overhead. It must be understood as essential to protecting and delivering digital value. As one DVMS author puts it: “Value creation and value protection are two sides of the same coin. An unprotected value has no value.
This principle reframes how organizations evaluate cybersecurity decisions. Instead of asking “What will it cost to be secure?” leaders should ask “What is the cost of not protecting the value we create?” This orientation invites new questions — not about control sufficiency, but outcome effectiveness and stakeholder trust.
Systems Thinking and Adaptability
The outcomes lens also encourages systems thinking, seeing cybersecurity not as a set of isolated technical controls but as an integrated system that must evolve with the business. The DVMS promotes an overlay model that enables any organization, regardless of its frameworks or tools, to continuously assess and improve its cybersecurity capabilities across seven minimal viable capabilities (Govern, Assure, Plan, Design, Change, Execute, Innovate).
This adaptability is essential in today’s digital environment, where risk is dynamic and disruption is constant. Compliance may help with audits, but only adaptability ensures resilience.
Cyber Operational Resilience: The Ultimate Outcome
Ultimately, the goal is not compliance or cybersecurity per se. The goal is cyber operational resilience—the ability of the organization to anticipate, withstand, respond to, and recover from adverse conditions, stresses, and cyber events while continuing to fulfill its mission and deliver value.
An outcomes-centric use of the NIST CSF supported by a DVMS guides organizations toward this end state. It provides a common language for cross-functional communication, supports strategic alignment, and fosters a culture of continual improvement. It helps organizations ask better questions, understand their exposure, and invest in the practices that matter most, not just the ones that are easiest to audit.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
In today’s digitally driven economy, cyber disruptions are no longer an “if” but a “when.”
The DVMS Institute’s Certified Training Programs teach organizations the skills to build a Holistic and Culture-Aligned Overlay System capable of coordinating Adaptive, Cyber Operations Governance, Resilience, and Assurance across a Complex Digital Ecosystem.
Achieving true cyber resilience across a complex digital ecosystem requires seamless alignment between organizational Strategy, Governance, and Operations, underpinned by a culture dedicated to sustaining and continuously innovating organizational digital value.

The DVMS positions cyber resilience as a strategic, enterprise-wide capability powered by the Institute’s CPD, Z-X, and 3D Knowledge models.
This systems-based approach to cyber operational resilience demands active engagement from all members of the Digital Ecosystem, with each member playing a distinct role in proactively identifying and mitigating the systemic risks that threaten digital business operations.
This adaptive, forward-looking approach to Governance, Resilience, and Assurance (GRA) positions businesses to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Drive Agility and Trust Across Your Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Explainer Videos
- Architecture Video: David Moskowitz explains the DVMS System
- Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- Overlay Model – What is an Overlay Model
- ZX Model – The MVC’s that power operational resilience
- CPD Model – Adaptable governance and assurance
- 3D Knowledge Model – Enabling holistic organizational learning
- FastTrack Model – A phased approach to cyber resilience
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved