The Holistic Imperative: Why Cybersecurity Penetration Testing Must Extend Beyond Technology
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
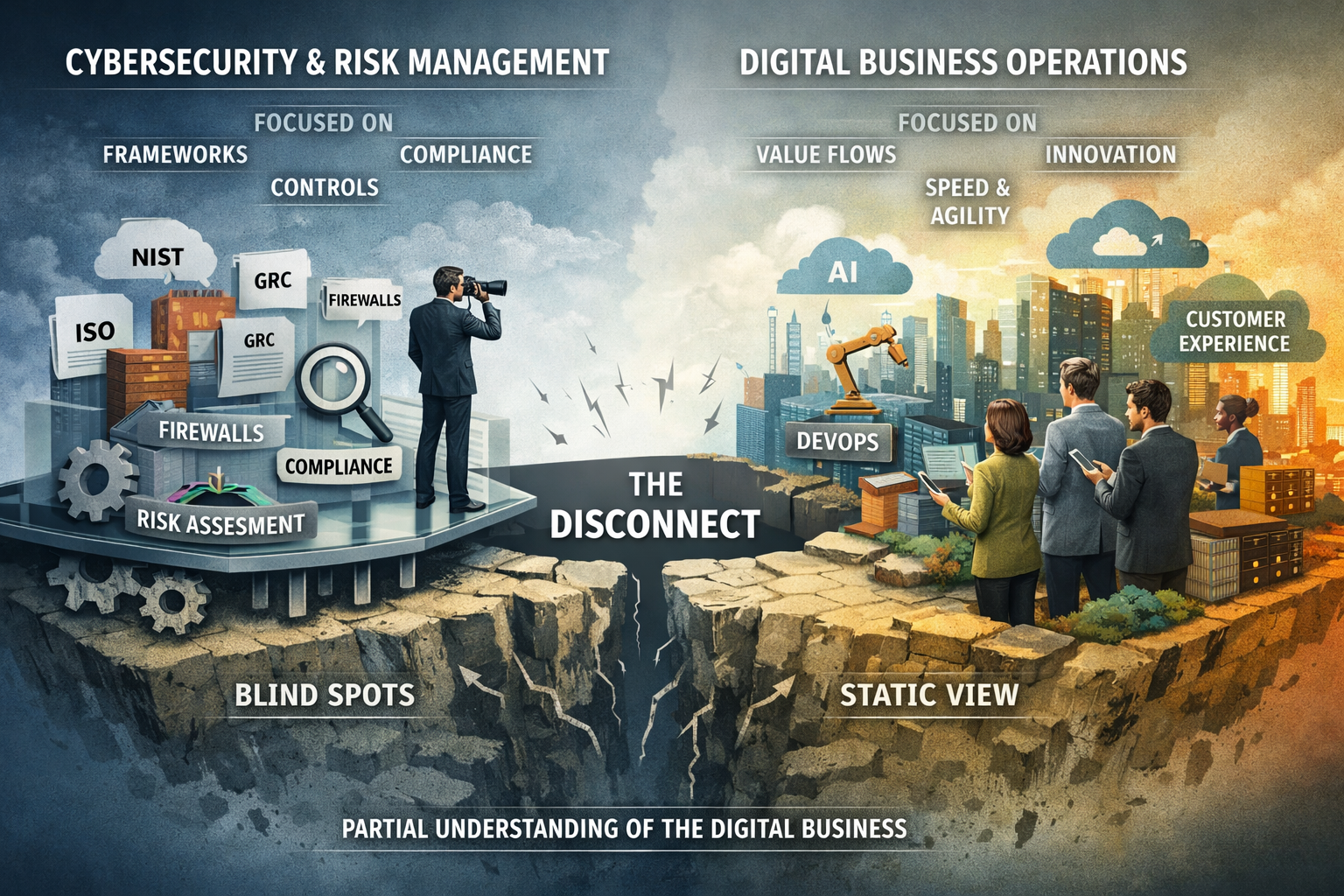
The limitations of a purely technical penetration test are becoming increasingly evident. Focusing solely on firewalls, intrusion detection systems, and software vulnerabilities overlooks the human element, often the weakest link in the security chain. Social engineering, phishing attacks, and insider threats exploit human psychology and organizational processes, not just technical flaws. A technically sound system can be rendered vulnerable by a well-crafted phishing email that tricks an employee into revealing their credentials. Therefore, a comprehensive penetration test must simulate these real-world scenarios, assessing the organizational susceptibility to such attacks and the effectiveness of its security awareness training.
Furthermore, a technical penetration test often fails to consider the broader business context. Different systems and data hold varying levels of importance to the organization. A vulnerability in a non-critical system might pose a minimal risk, while a similar vulnerability in a system containing sensitive customer data could have catastrophic consequences. A holistic penetration test considers the business impact of potential breaches, prioritizing the testing and remediation of vulnerabilities based on their potential to disrupt operations, damage reputation, or lead to financial losses. This business-centric approach ensures that resources are allocated effectively, focusing on the areas that pose the most significant risk to the organizational strategic objectives.
Integrating business capabilities into penetration testing is crucial for understanding how technology is used within the organization. Technical vulnerabilities often arise from misconfigurations or improper implementations of technology to support specific business processes. For example, a vulnerability in a web application might result from developers prioritizing speed over security during the development process. By understanding the business drivers behind technology adoption and usage, penetration testers can identify technical flaws and the underlying process weaknesses that contribute to these vulnerabilities. This insight allows for more targeted recommendations for improvement, addressing the root causes of security issues rather than just patching the symptoms.
Beyond technology and business processes, the organizational security culture plays a vital role in its overall security posture. A strong security culture fosters a sense of shared responsibility for security, encouraging employees to be vigilant and report suspicious activity. Conversely, a weak security culture can undermine even the most sophisticated technical defenses. Employees who are apathetic about security or view security measures as a hindrance to their work are likelier to make mistakes that can compromise the organizational systems. A holistic penetration test assesses the organizational security culture by evaluating employee awareness of security policies, adherence to them, and willingness to report security incidents. This assessment can involve surveys, interviews, and simulated social engineering attacks to gauge the organizational overall level of security consciousness.
Incorporating organizational technologies, business capabilities, and culture into penetration testing requires a shift in mindset and methodology. It demands a collaborative approach involving technical security experts and representatives from different business units, IT operations, and even human resources. This cross-functional collaboration ensures that the penetration test covers all relevant aspects of the organization and that all stakeholders understand and act upon the findings.
The expanded scope of a holistic penetration test necessitates the use of a wider range of testing techniques. In addition to traditional vulnerability scanning and exploit development, penetration testers must employ social engineering tactics, simulate phishing attacks, and conduct reviews of security policies and procedures. They must also be able to analyze business processes and identify potential associated security risks. This requires a diverse team of security professionals with expertise in various domains, including technical security, business analysis, and social engineering.
A holistic penetration test’s output is also different from that of traditional tests. While technical vulnerabilities are still identified and reported, the focus shifts to providing actionable recommendations that address the underlying causes of security issues. These recommendations might include technical fixes, process improvements, and security policy and training program changes. The report should also highlight the business impact of potential breaches, allowing organizations to prioritize remediation efforts based on risk.
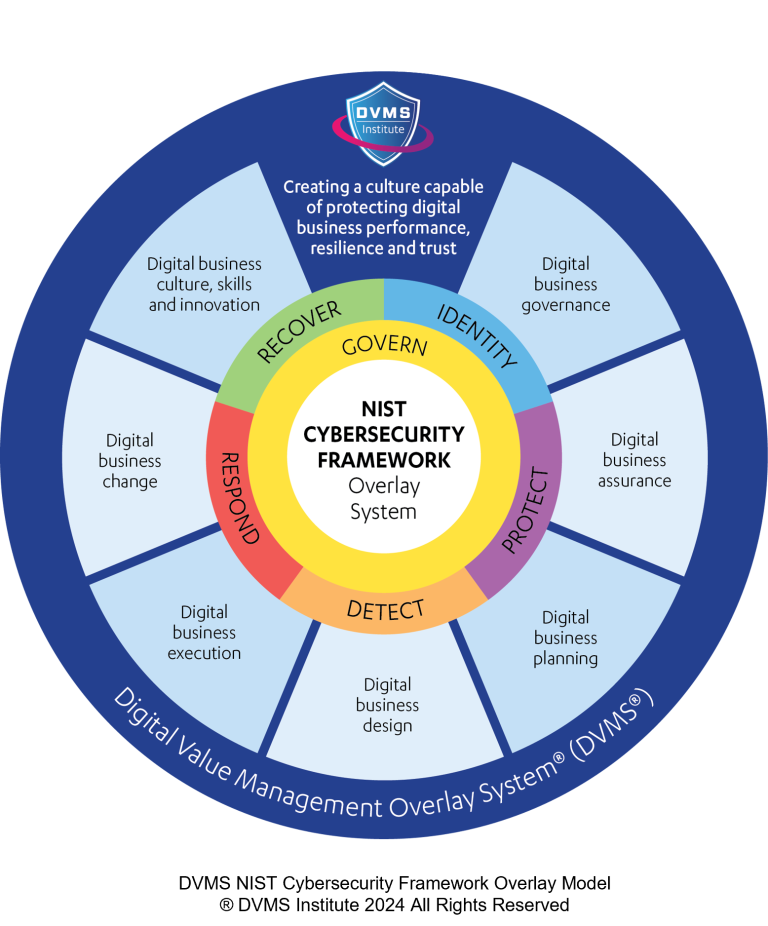
Cybersecurity penetration testing must evolve beyond its traditional focus on technology to embrace a holistic perspective incorporating organizational technologies, business capabilities, and culture. By considering these interconnected elements, organizations can better understand their security posture and identify hidden risks that might otherwise go unnoticed. This holistic approach enables more effective remediation efforts, improves security awareness, and fosters a stronger security culture, ultimately leading to a more resilient and secure organization. In today’s complex threat landscape, a holistic approach to penetration testing is not just a best practice but a necessity.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
DVMS Institute is a renowned provider of accredited (APMG International), Assured (NCSC-GCHQ-UK), and Recognized (DHS-CISA-NICCS) NIST Cybersecurity Framework, certification training programs designed to teach organizations of any size, scale, or complexity how to manage their organizational cyber risk and resiliency.
For cyber risk management, the DVMS FastTrack model provides a phased approach to adapting the NIST Cybersecurity Framework functions and its controls across an enterprise and its supply chain to identify and mitigate organizational cyber risks.
For cyber resilience management, the DVMS-CPD model teaches a holistic approach to digital value resiliency by connecting digital system outcomes to a culture of innovation trained to create, protect, and deliver organizational digital value.
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
® DVMS Institute 2024 All Rights Reserved