What the Three Mile Island and Modern Cyber Incidents Have in Common
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Introduction: Different Domains, Shared Lessons
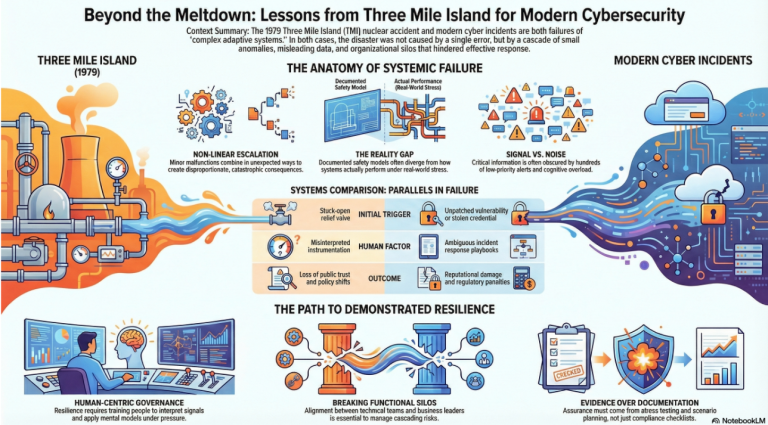
At first glance, the 1979 Three Mile Island (TMI) nuclear accident and modern cybersecurity incidents appear to belong to entirely different domains. One involved a partial nuclear reactor meltdown in Pennsylvania; the other typically involves malicious code, stolen data, or disrupted digital services. Yet beneath the surface, both reflect systemic failures in complex, tightly coupled socio-technical systems. Each reveals how technology, human decision-making, organizational design, and governance interact under stress. When examined through the lens of resilience and assurance, Three Mile Island and major cybersecurity incidents share striking commonalities that offer enduring lessons for digital enterprises.
Complex Systems That Fail in Non-Linear Ways
Both nuclear power plants and modern digital enterprises are complex adaptive systems. They contain thousands of interdependent components, automated safeguards, human operators, and feedback loops. In such systems, failure rarely results from a single catastrophic mistake. Instead, it emerges from a chain of small, interacting anomalies that escalate in unexpected ways.
At Three Mile Island, a relatively minor mechanical malfunction, a stuck-open relief valve, combined with misleading instrumentation and operator assumptions to create a cascading crisis. In cybersecurity incidents, an unpatched vulnerability, a misconfigured identity role, or a compromised vendor credential can similarly combine with routine operational activity to produce disproportionate consequences. In both cases, the system does not fail because no controls existed; it fails because controls interact in ways designers did not fully anticipate. Complexity amplifies small deviations into systemic risk.
The Gap Between Design and Reality
A defining feature of the Three Mile Island incident was the divergence between the plant’s designed safety model and the reality operators faced in the control room. Instrumentation did not clearly indicate that coolant was escaping. Operators misinterpreted signals because their training emphasized certain failure scenarios over others. The “paper system” of engineered safeguards did not align with the “living system” of human interpretation under pressure.
Cybersecurity incidents exhibit the same gap. Organizations maintain policies, diagrams, and control frameworks that describe how systems should behave. Access controls are documented. Monitoring processes are defined. Incident response playbooks are approved. Yet during an actual breach, teams often discover that logging was incomplete, alert thresholds were poorly tuned, or escalation paths were ambiguous. The documented architecture differs from the operational reality. In both nuclear and digital contexts, resilience depends not merely on design, but on how the system performs under real-world stress.
Misleading Signals and Information Overload
At Three Mile Island, operators were overwhelmed by alarms—hundreds of alerts triggered in a short period. The sheer volume of signals obscured the root cause. Critical information was technically available but not cognitively accessible in a way that supported rapid understanding.
Modern cybersecurity operations centers (SOCs) face a similar challenge. During a major incident, analysts may confront thousands of alerts, many of which are false positives or low-priority events. Signal competes with noise. Teams struggle to distinguish early indicators of systemic compromise from routine anomalies. Attackers exploit this reality by blending malicious activity into normal traffic patterns.
In both scenarios, the problem is not the absence of data but the lack of clarity. Systems generate information without ensuring it supports sound decision-making under pressure. When cognitive overload replaces situational awareness, small errors compound.
Human Factors Under Stress
Three Mile Island underscored the centrality of human factors in high-risk environments. Operators made decisions consistent with their training and understanding, yet those decisions inadvertently worsened the situation. Under uncertainty, they acted to preserve what they believed was reactor integrity, unaware that coolant levels were dangerously low.
Cybersecurity incidents similarly unfold in high-pressure environments where time, ambiguity, and incomplete information shape behavior. Incident commanders must decide whether to isolate systems, shut down production, notify regulators, or negotiate with attackers. Misjudgments are rarely due to incompetence; they arise from the difficulty of interpreting evolving conditions within complex systems.
Both cases demonstrate that resilience cannot rely solely on technical controls. It must account for how people interpret signals, apply mental models, and coordinate action under stress. Training, rehearsal, and clear decision rights are as critical as engineered safeguards.
Organizational Silos and Communication Breakdowns
Another parallel lies in organizational structure. Investigations of Three Mile Island revealed communication gaps between engineering teams, management, regulators, and plant operators. Information was not always shared or contextualized effectively. Decision-making authority and situational understanding were unevenly distributed.
In cybersecurity incidents, similar silos frequently emerge. Security teams detect anomalies but struggle to gain attention from business leaders. IT operations may resist system shutdowns due to service commitments. Legal, compliance, and communications teams become involved only after escalation. Fragmented governance slows coordinated response.
When roles, responsibilities, and escalation paths are unclear, the system’s ability to contain failure weakens. Both nuclear and digital incidents reveal that resilience is not just technical; it is organizational. Alignment across functions is essential to manage cascading risk.
The Illusion of Safety
Prior to Three Mile Island, the nuclear industry possessed strong confidence in its safety systems. Plants were engineered with multiple redundant safeguards. Regulatory frameworks were established. The accident exposed how confidence based on design assumptions can mask untested vulnerabilities.
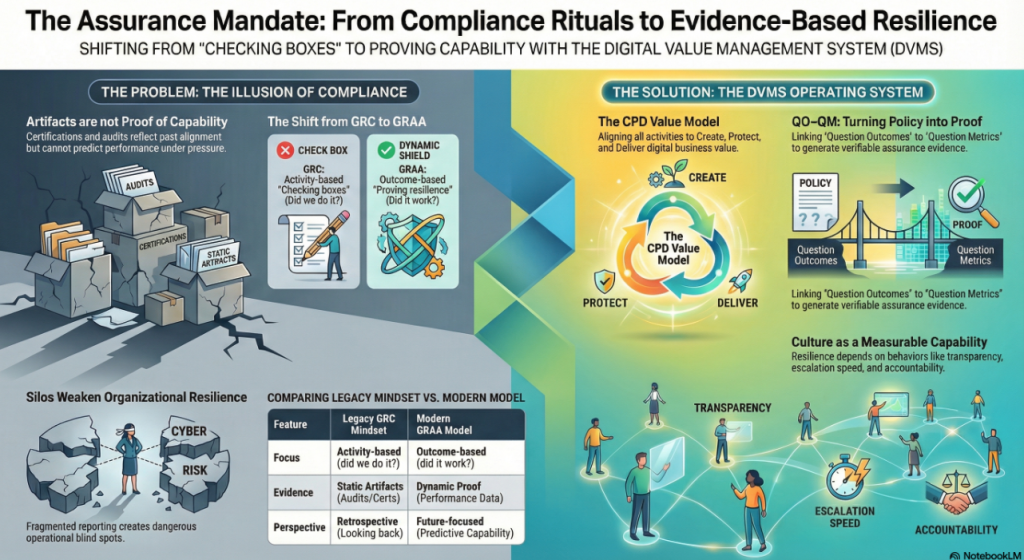
Similarly, many organizations enter cybersecurity incidents with high confidence, based on compliance certifications, audit reports, and risk dashboards. Controls appear mature. Policies are up to date. External assessments yield favorable ratings. Yet a single successful phishing campaign or software supply chain attack can reveal systemic blind spots.
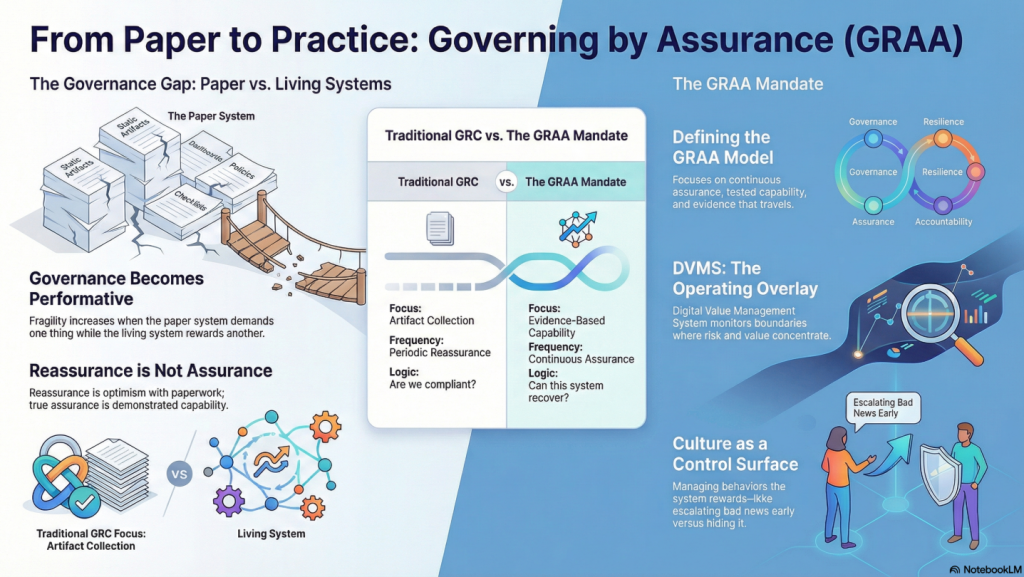
In both contexts, reassurance—confidence derived from documentation—proved insufficient. Assurance requires evidence that systems can withstand real-world stress, not just that safeguards exist in theory.
Cascading Consequences Beyond the Immediate Event
The impact of Three Mile Island extended far beyond the reactor itself. Public trust in nuclear energy declined sharply. Regulatory scrutiny intensified. Industry economics shifted. The incident reshaped policy and perception for decades.
Cybersecurity incidents have comparable ripple effects. A breach can erode customer trust, depress stock value, trigger regulatory penalties, and invite class-action lawsuits. Supply chain disruptions can affect downstream partners and customers. Reputational damage often exceeds direct technical loss.
Both events illustrate that in interconnected systems, localized failures produce systemic consequences. The true cost of disruption includes intangible factors such as trust, legitimacy, and strategic momentum.
Regulatory and Governance Evolution
In the aftermath of Three Mile Island, the nuclear industry underwent significant reform. Operator training improved. Control room designs were re-evaluated. Regulatory oversight intensified. The event catalyzed a shift toward a more rigorous safety culture and performance monitoring.
Cybersecurity regulation is following a similar trajectory. Major breaches have prompted expanded disclosure requirements, stricter data protection laws, and increased board-level accountability. Regulators now expect evidence of resilience, not just compliance with baseline controls.
Both domains demonstrate how high-impact incidents drive governance evolution. Crises reveal systemic weaknesses that routine oversight fails to detect. The challenge for modern enterprises is to learn proactively rather than reactively.
The Central Lesson: Resilience Must Be Demonstrated
Perhaps the most enduring commonality between Three Mile Island and cybersecurity incidents is this: resilience must be demonstrated, not assumed. Safety mechanisms at TMI were real, yet they were not sufficient under the specific conditions that emerged. Cybersecurity controls are often real, yet they may not perform as expected when adversaries exploit unanticipated interactions.
Demonstrated resilience requires stress testing, scenario planning, and continuous learning. It demands that organizations examine how systems behave when degraded, not only when functioning normally. It requires bridging the gap between documentation and lived reality.
Conclusion: Governing Living Systems
Three Mile Island and modern cybersecurity incidents remind us that high-risk systems fail at the intersection of technology, people, and governance. Both reveal the danger of mistaking procedural completeness for operational readiness. Both show how complexity, cognitive overload, and fragmented accountability can transform manageable anomalies into systemic crises.
The lesson for digital enterprises is clear. Cyber resilience cannot be confined to technical safeguards or compliance artifacts. It must be governed as a living capability—continuously monitored, tested, and improved. Just as the nuclear industry was forced to confront the realities of complex system failure, today’s organizations must recognize that cybersecurity incidents are not merely technical events. They are manifestations of systemic fragility. And, like Three Mile Island, they offer a choice: respond with incremental documentation or fundamentally strengthen the system’s resilience.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
DVMS Cyber Resilience Professional Accredited Certification Training
Teaching Enterprises How to Govern, Assure, and Account for Operational Resilience in Living Digital Ecosystems
Moving From Paper to Practice-Based Operational Resilience
Explainer Video – Governing By Assurance
Despite an abundance of frameworks, metrics, and dashboards, many leaders still lack a clear line of sight into how their digital value streams perform when conditions deteriorate.
Strategic intent, organizational structures, and day-to-day behaviors are evaluated separately, producing static snapshots that fail to reveal how decisions, dependencies, and human actions interact within a dynamic digital system.
The result is governance that appears comprehensive in documentation yet proves fragile under pressure, leaving leaders to reconcile disconnected controls rather than systematically strengthen operational resilience.
What is needed is a framework-agnostic operating overlay that enables operational resilience to be governed, assured, and accounted for coherently across complex, living digital ecosystems.
DVMS Institute White Papers – The Assurance Mandate Series
Explainer Video – From Compliance Rituals to Evidence-Based Resilience
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
The Assurance Mandate Paper explains why traditional compliance artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
The Digital Value Management System® (DVMS)
Explainer Video – What is a Digital Value Management System (DVMS)
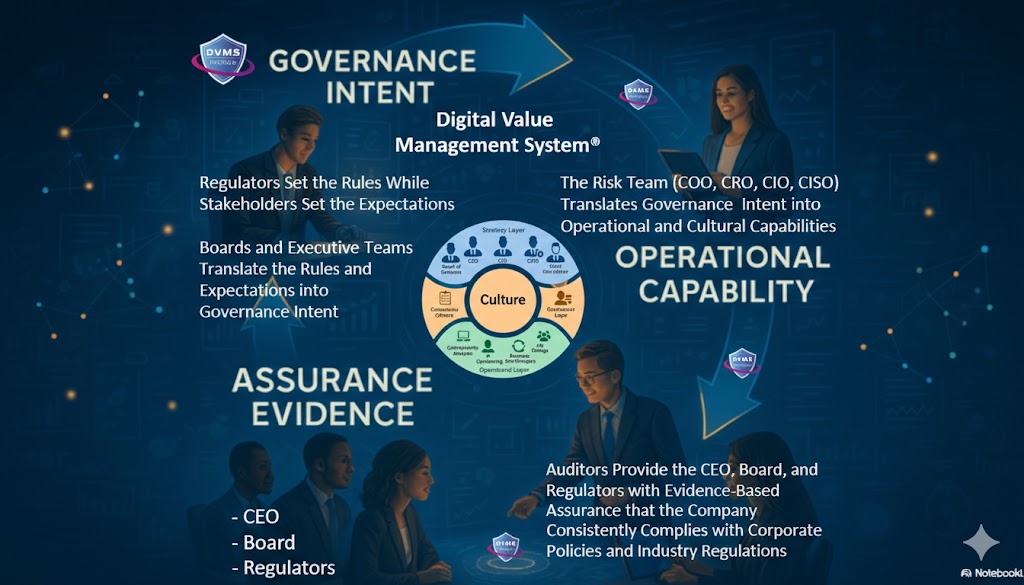
The DVMS is an overlay management system that governs, assures, and accounts for operational resilience in complex, living digital ecosystems. It does so by ensuring living-system outcomes account for paper-system intent.
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business performs
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Learning – for governance intent and operational capability fine-tuning
Underpinning this integration are three distinctive DVMS models
Create, Protect, and Deliver (CPD) – The CPD Model™ is a systems-based model within the DVMS that links strategy-risk and governance to execution to create, protect, and deliver digital business value as an integrated, continuously adaptive capability.
3D Knowledge (3DK) – The 3D Knowledge Model is a systems-thinking framework that maps team knowledge over time (past, present, future), cross-team collaboration, and alignment to strategic intent to ensure that organizational behavior, learning, and execution remain integrated and adaptive in delivering digital business value.
Minimum Viable Capabilities (MVC) – The Minimum Viable Capabilities (MVCs) model supports the seven essential, system-level organizational capabilities—Govern, Assure, Plan, Design, Change, Execute, and Innovate—required to reliably create, protect, and deliver digital business value in alignment with strategy-risk intent.
The models work together to enable the following organizational capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Benefits – Organizational and Leadership
Explainer Video – DVMS Organization and Leadership Benefits
Instead of replacing existing operational frameworks and platforms, the DVMS elevates them, connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
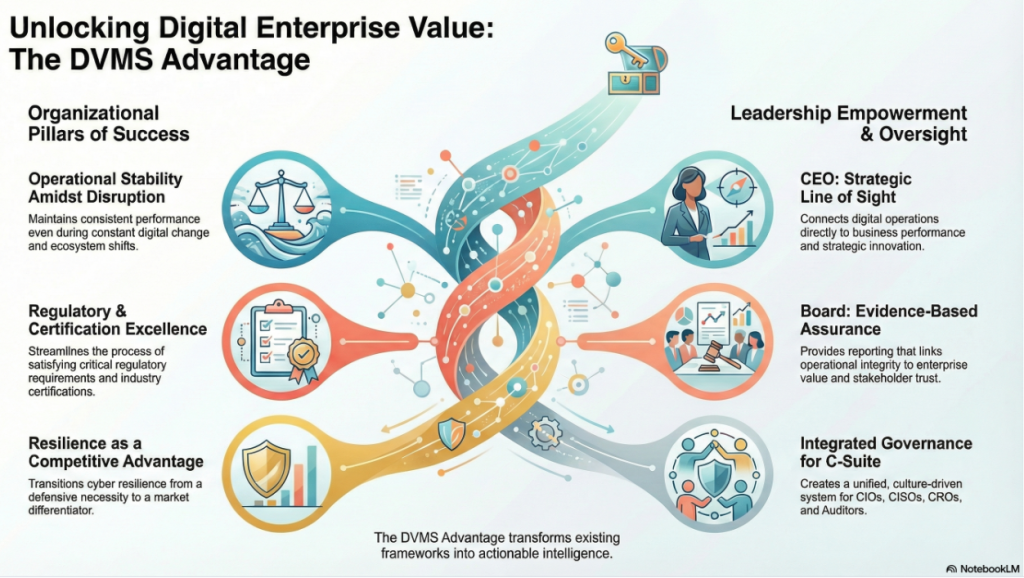
By adopting a DVMS, enterprises are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors, an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability.
DVMS – Accredited Certification Training Program
Explainer Video – The DVMS Training Pathway to Cyber Resilience
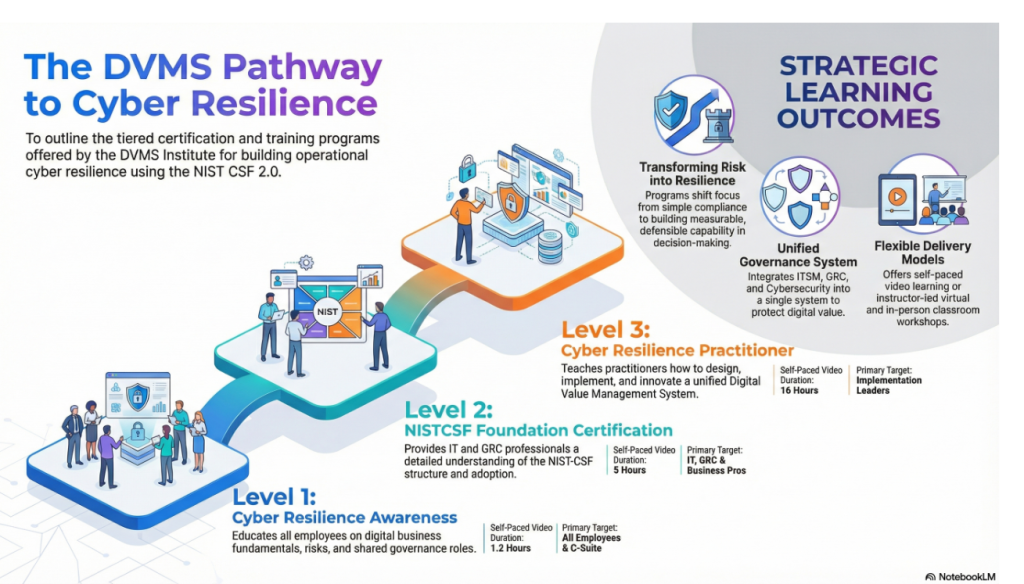
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to integrate fragmented systems into a unified, culture-driven governance and assurance system that accounts for the resilience of digital value within a living digital ecosystem.
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS NISTCSF Cyber Resilience Foundation Certification Training
The DVMS NISTCSF Cyber Resilience Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
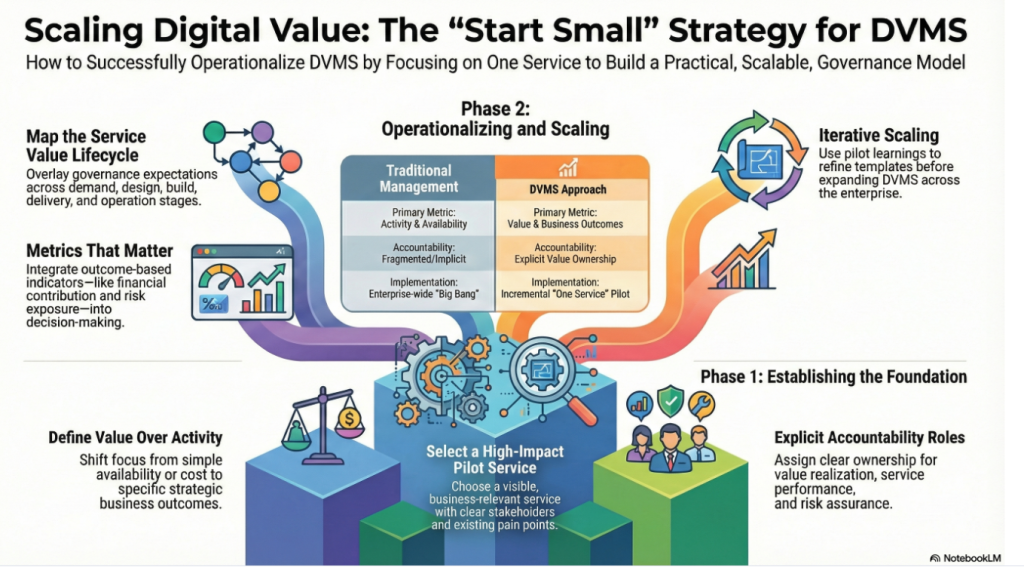
A FastTrack Approach to Launching Your DVMS Program
Explainer Video – Scaling a DVMS Program
The DVMS FastTrack approach is a phased, iterative approach that helps organizations mature their DVMS over time, rather than trying to do everything simultaneously.
This approach breaks the DVMS journey into manageable phases of success. It all starts with selecting the first digital service you want to make cyber resilient. Once that service becomes resilient, it becomes the blueprint for operationalizing cyber resilience across the enterprise and its supply chain.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved