Where Resilience Actually Breaks, Dependencies, Handoffs, & Suppliers – The GRAA Management Series Part 5
David Nichols – Co-Founder and Executive Director of the DVMS Institute
Managers rarely lose sleep over the things they fully control. We lose sleep over the things we depend on. A service can be well-run, well-staffed, and well-governed within its own boundaries and still fail because the ecosystem it relies on does something unexpected. That is not a complaint. It is the reality of modern digital operations.
This is also why the emotional center of the GRAA Leadership Series – Part Two, “Your Organization Doesn’t Have a Framework Problem: It Has an Overlay Problem” – matters. Framework overlays are not particularly helpful if the system’s fundamental couplings are not visible or manageable. An organization can map controls across multiple frameworks and still be fragile if dependencies are assumed rather than governed.
In this management article, we will focus on where resilience breaks: the seams between teams, functions, and enterprises. The good news is that managers can govern these seams. We cannot eliminate dependencies, but we can stop treating them as invisible. We can establish boundaries, create fallbacks, and gather evidence that the ecosystem can operate within tolerable limits. That shift is how you turn dependency anxiety into operational confidence.
The manager reality: you own an outcome you do not fully control
Most enterprises have been built on a foundation of functional ownership. Teams own platforms, applications, networks, security controls, compliance processes, vendor management, and so on.
Customers, boards, and regulators do not experience the enterprise in the same way. They experience outcomes. Can I place an order? Can I receive care? Can I access my account? Can I get paid? Can I ship a product?
Managers sit in the middle. We are accountable for outcomes, even when they span multiple teams and suppliers. That tension is not going away. It is increasing. Dependencies are multiplying, and shared platforms have become the default. Even when you “own” a system, it relies on identity, data, network, cloud, tooling, and third parties that can fail in ways you cannot predict.
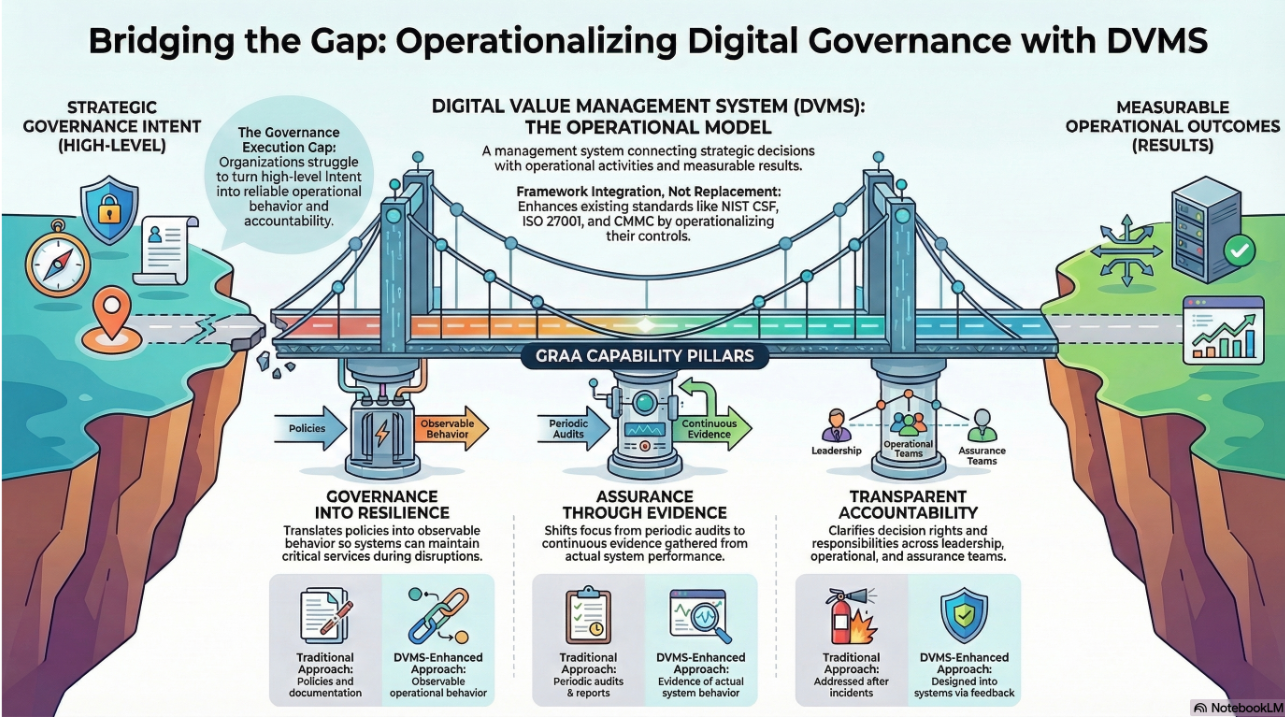
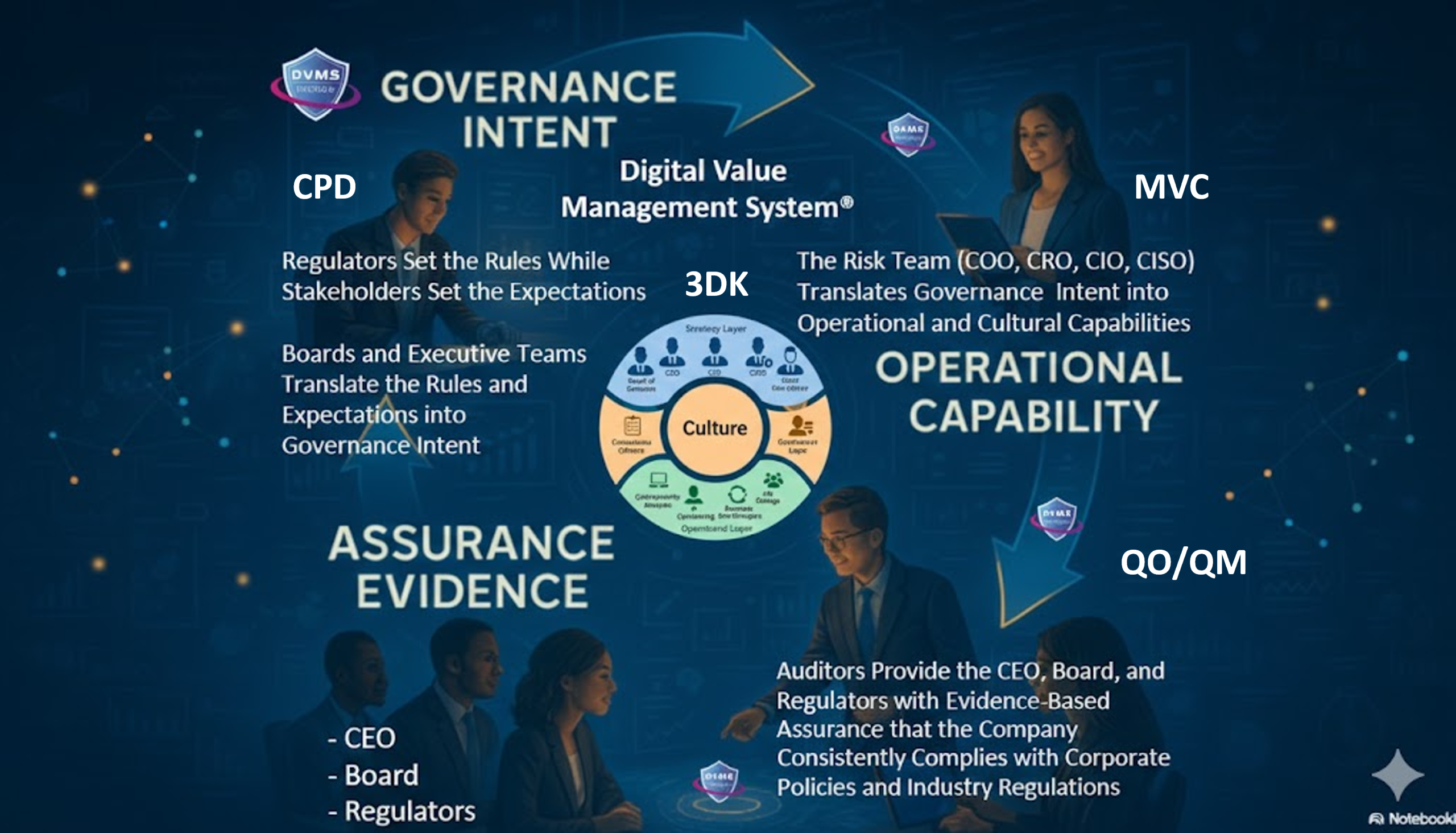
The goal is not to pretend you control the whole ecosystem. The goal is to make the ecosystem governable. This is where DVMS and GRAA are practical. They provide managers with a way to set boundaries and gather evidence across organizational seams.
Why “well-managed suppliers” still take you down
Managers often hear a comforting phrase: “That supplier is well managed.” Sometimes it is true. It still does not mean you are safe. There are a few reasons.
One is a hidden coupling. Two systems can appear independent until they share a platform, a data pipeline, an identity boundary, or a common provider. When that shared dependency fails, both fail in a correlated manner.
Another is synchronized change. If your organization and your supplier are both undergoing rapid changes, the likelihood of unexpected interactions increases. Even if each change is “approved,” the combined effect can still surprise you.
Another is mismatched tolerances. You may need a dependency to recover in two hours, while they may be designed to heal in eight. Their definition of “available” may not match your definition of “usable,” especially if integrity verification differs.
One more is assumption drift. A dependency that behaved one way last year may behave differently today. People change. Platforms change. Business models change. Contracts remain the same. Assumptions grow stale without anyone noticing.
Finally, there is the human factor. During a disruption, the supplier is also under pressure. Their priorities may not align with yours. Their communication may be constrained. Their escalation paths may not be the ones you expected. As a result, your outcome is at risk even if their internal story is “we are handling it.”
None of this is a reason to distrust suppliers. It is a reason to stop relying on assurances that lack evidence. Evidence trumps artifacts, and this is where that principle becomes urgent.
Seams inside the enterprise are the same problem.
Before we focus too much on suppliers, it helps to acknowledge something. Most of the seam problems that arise with suppliers also appear within your own organization.
The seam between product and operations is a classic example. A team may release a change that is correct in its own context yet destabilize an operational dependency. The seam between security and delivery is another. Protective constraints may be designed in a way that creates operational fragility if the control fails or becomes overly aggressive. The seam between risk and operations is another. Risk may be managed as a register, while operations manage risk as live variance. Both are valid. They have to connect.
This is why the GRAA Leadership Series – Part Four, “Seeing the System, A 3D View of Leadership, Structure and Behavior,” is so relevant here. Seams exist where structure does not align with outcomes and where local incentives shape behavior. Managers can’t fix this with slogans. We fix it by making seams visible and governable.
DVMS helps because Create, Protect, Deliver forces you to see the seam
DVMS is useful because it pushes you to view a value stream as a single system. It does not allow you to pretend that Create happens in one group, Protect in another, and Deliver somewhere else. Every outcome depends on all three, and seams exist where those modes are not coordinated. If you approach dependencies through Create, Protect, and Deliver, you ask better questions.
In Create, you define the outcome and tolerance, and identify the essential dependencies required for that outcome. This is where managers clarify what cannot be allowed to fail silently.
In Protect, you define unacceptable harm and constraints and identify which dependencies can cause harm or compromise integrity. This is where you determine where verification is required and where manual modes are necessary.
In Deliver, you define the operational behaviors that will carry you through dependency disruptions. These include degradation modes, alternate routing, fallback processes, and recovery sequencing.
This echoes the practical message of Thriving on the Edge of Chaos: Managing at the Intersection of Value and Risk in the Digital Era. The book advances a simple idea: in a dynamic environment, governance and resilience stem from operating the system at the edge, where value and risk meet. Dependencies are the edge.
Dependency governance: the manager’s version
When managers hear “vendor management,” they often think of contracts, SLAs, and quarterly reviews. Those matter, but they do not build resilience under pressure.
Dependency governance is different. It is outcome-centric and behavior-centric.
A manager’s dependency governance asks:
- What outcome does this dependency enable?
- What tolerances does our outcome require, including degradation and recovery?
- What degradation mode exists if the dependency is impaired?
- What manual mode exists if the dependency is unavailable?
- What alternate path exists if we need to route around it?
- How do we verify integrity when it returns?
- What evidence do we have that these behaviors work?
If you can answer those questions, you can manage the dependency with confidence. If you cannot, you will be surprised when disruption hits, even if your supplier is “well managed.”
The Dependency Boundary Card
In Part 1, we introduced the Boundary Card for an outcome. For dependencies, you can create a Dependency Boundary Card. It is straightforward. It is a practical tool that reduces seam risk.
A Dependency Boundary Card includes the shared outcome, the tolerance requirements, the escalation and communication path, the degrade and fallback options, the recovery sequence, and the evidence you expect to see. It also explicitly records assumptions, because assumptions are what decay over time.
You can use the same pattern for internal dependencies and external suppliers. That is a useful trick. It reduces complexity by treating dependencies consistently. This also supports the leadership series paradigm. In the GRAA Leadership Series – Part Six, “Running on CPD,” CPD is described as an operating rhythm. Dependency boundary management is one area where managers can establish that rhythm.
How evidence changes supplier conversations in a positive way
Managers often hesitate to ask suppliers for evidence because they fear it will create conflict. It doesn’t have to. The tone is not “prove you are competent.” The tone is “we want our shared system to behave predictably, and we want to align our recovery behaviors.”
This is collaborative, not adversarial. Instead of asking, “Are you compliant?” a manager can ask:
- When you have an outage, what do you degrade first, and why?
- What is your recovery sequence, and how do you decide which services return first?
- How do you verify integrity before declaring service restored?
- What was the result of your last restore test, and what did you learn?
- What do you need from us during disruption to recover faster?
- How do we communicate when tolerance is threatened?
These are evidence-driven questions. They do not insult the supplier. They invite a joint resilience posture.
They also produce something valuable. They provide proof points you can use internally, both for assurance and for accountability. That aligns with GRAA Leadership Series – Part Seven, “You Do Not Need More Dashboards.” A supplier status dashboard is not an assurance. Evidence of recovery behavior is.
A manager scenario: the dependency that fails, and the fallback that saves you
Imagine a shared payment or authorization service used across multiple business processes. Your team’s outcome depends on it. An incident at the supplier or internal platform causes transactions to slow, time out, or fail.
In an artifact-driven environment, the initial response is uncertain. People debate whether to pause operations. Customer support is flooded. Leadership seeks confidence. Teams scramble for answers from the dependency owner. The outage spreads.
In an evidence-driven environment, the response is different.
The Outcome Boundary Card defines tolerances. The Dependency Boundary Card defines what happens when the dependency is impaired. There is a degrade mode that preserves core transactions while deferring non-critical ones. There is a manual mode for a narrow set of high-value cases. An escalation trigger is tied to the tolerance threshold. Communication is routed through a defined path, and the supplier knows what evidence to provide.
The manager quickly enters degrade mode because decision rights are clear. The team captures evidence as they conduct their operations. Leadership receives a coherent update grounded in tolerances and subsequent actions. As the dependency begins to recover, the team restores it in a known sequence and verifies its integrity before scaling back to normal operations.
From the outside, the customer experience is degraded but not chaotic. From the inside, the operation behaves as designed. That is resilience, and it is built at the seam. This is not theoretical. It is the kind of difference that separates “we had an incident” from “we had a crisis.”
The internal seam: accountability across teams
Dependency resilience also makes accountability fairer. In Part 4, we described accountability anchors: decision rights, escalation obligations, and evidence obligations. Dependencies are where those anchors often break because accountability is split across teams.
If you use Boundary Cards and evidence expectations across seams, accountability becomes shared but clear. Each team understands its obligations. The dependency owner understands the evidence needed to support the consuming outcomes. The consuming team understands the degradation and fallback behaviors it must implement.
That reduces blame. It increases coordination. It makes the system governable. It also helps audit and GRC partners. Evidence is now tied to operational behavior across seams rather than trapped in isolated functional artifacts.
A practical manager plays the dependency drill.
To quickly improve resilience, conduct a dependency drill. Pick one critical outcome that depends on a single critical dependency. The goal is not to simulate every technical detail. The goal is to validate boundaries and behaviors.
Walk through a scenario where the dependency is degraded. Ask: What triggers our degrade mode? Who authorizes it? How do we communicate? What evidence do we capture? What do we do if the dependency is unavailable for longer than the tolerance? What manual modes exist? What do we restore first? What do we verify?
This drill will reveal seams immediately. It will also reveal unclear decision rights, missing fallback paths, unrealistic assumptions, and evidence gaps. Fix one or two of those seams. Update the Boundary Cards. Capture the evidence changes. You will be measurably more resilient, and you will have proof.
This is the management expression of “From Chaos to Capability” in Part Five of the GRAA Leadership Series. Capability is not a claim. It is a behavior, and evidence suggests that it exists.
Dependency resilience is a management discipline, not a supplier problem.
Managers cannot eliminate dependencies, and we do not need to. We need to manage them as part of the system. When you treat dependencies as governable boundaries, you change the game. You move from surprise to predictability. You reduce chaos. You improve recovery. You strengthen accountability. You also make audits less of a paper chase because evidence is generated through normal operations.
In Parts Five and Six of this management series, we will bring everything together into a practical framework. We will discuss how managers can run GRAA as an operating rhythm, week by week and month by month, using Create, Protect, Deliver as the flow of work and boundary, evidence, and accountability practices as the glue that makes resilience real.
About the Author

Dave is the Executive Director of the DVMS Institute.
Dave spent his “formative years” on US Navy submarines. There, he learned complex systems, functioning in high-performance teams, and what it takes to be an exceptional leader. He took those skills into civilian life and built a successful career leading high-performance teams in software development and information service delivery.
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2026 All Rights Reserved