The Illusion of Control in Modern Enterprises
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Most GRC, ITSM, and cybersecurity platform companies promise visibility, control, and confidence amid growing digital complexity. Their marketing emphasizes dashboards, heatmaps, workflows, and maturity scores that suggest organizations can be managed through structured data and standardized processes. Yet many executives and practitioners experience a persistent gap between what these platforms report and how their organizations behave under pressure. Incidents recur, risks emerge unexpectedly, and cultural or coordination failures undermine otherwise well-designed controls. The core problem is that most platforms are built to manage artifacts and abstractions, not the living system of people, processes, and technologies that produce real outcomes.
Platforms Optimized for Frameworks, Not Systems
A fundamental limitation of most GRC, ITSM, and cybersecurity platforms is that they are optimized around frameworks rather than systems. They encode standards such as NIST, ISO, COBIT, ITIL, or regulatory requirements into catalogs of controls, processes, and assessments. This approach helps organizations demonstrate alignment and compliance, but it assumes that faithfully implementing the framework’s elements leads to the desired behavior. Frameworks are static representations of good practice, while organizations are dynamic systems shaped by competing priorities, local adaptations, and human judgment. Platforms that mirror frameworks tend to reinforce a checklist mentality, where success is measured by completion and coverage rather than by how the system responds to stress, change, and uncertainty.
Fragmentation by Design
Most platforms reflect the same functional silos that exist within organizations. GRC tools focus on risks, controls, audits, and issues. ITSM platforms concentrate on incidents, changes, and service levels. Cybersecurity platforms emphasize threats, vulnerabilities, and detections. Each domain is internally coherent, but the boundaries between them are rigid. As a result, leadership intent, structural design, and operational behavior are captured in different systems, using different vocabularies, metrics, and cadences. The organization’s reality, however, unfolds across these boundaries, especially within end-to-end value streams. When platforms cannot natively connect these perspectives, leaders are left to mentally integrate fragmented views, relying on experience and intuition rather than shared, system-level insight.
Static Models in a Dynamic World
Another core issue is that most platforms rely on static or slowly changing models of the organization. Risk registers, control libraries, service catalogs, and asset inventories are periodically updated snapshots. They struggle to represent how workflows, how decisions are made in real time, or how priorities shift under pressure. Complex systems, by contrast, are defined by interactions and feedback loops that evolve continuously. Behavior changes in response to incentives, leadership signals, workload, and external events. Platforms that treat the organization as a stable structure miss these dynamics, leading to a false sense of predictability and control. When reality diverges from the model, the divergence often only becomes apparent after failure.
Overemphasis on Process Compliance
GRC, ITSM, and cybersecurity platforms typically assume that process compliance is the primary driver of good outcomes. Workflows are designed to ensure approvals are obtained, steps are followed, and evidence is captured. While process discipline is important, it is not sufficient in complex environments where judgment, trade-offs, and improvisation are unavoidable. People routinely encounter situations that fall between defined processes, or following the process exactly would create worse outcomes. Platforms rarely capture these moments or treat them as valuable signals about system health. Instead, deviations are logged as exceptions or noncompliance, reinforcing a gap between formal processes and lived reality.
Neglect of Leadership Signals and Incentives
One of the most significant blind spots in most platforms is leadership behavior. What leaders emphasize, reward, tolerate, or ignore has a profound impact on how systems operate. Yet leadership signals are largely invisible in GRC, ITSM, and cybersecurity tools. Strategies, narratives, and implicit priorities are treated as context rather than as active forces shaping risk and performance. As a result, platforms may report strong control environments while teams are simultaneously responding to conflicting messages that drive risky shortcuts or silence escalation. Without a way to surface and examine how leadership intent interacts with structures and behaviors, organizations cannot diagnose why well-designed controls are underused or bypassed.
Behavior Treated as an Output, Not an Input
Most platforms treat behavior as an outcome to be measured after the fact, rather than as a control surface. Incidents, breaches, outages, and audit findings are recorded and analyzed retrospectively. Culture surveys may be appended as separate artifacts. What is missing is a continuous view of how people make decisions, communicate concerns, and coordinate across boundaries in real time. Behavior is where risk materializes, and resilience is tested, yet platforms struggle to represent it beyond lagging indicators. This reinforces a reactive posture, where learning happens after harm rather than as part of ongoing system awareness.
Misaligned Metrics and Local Optimization
Platform-driven metrics often encourage local optimization at the expense of system performance. Risk scores, SLA compliance, mean time to resolve, vulnerability counts, and audit closure rates each make sense within their own domain. However, when teams are incentivized to optimize these metrics independently, the overall system can become more brittle. For example, pressure to meet delivery timelines may discourage risk escalation, while aggressive incident-closure targets may reduce learning. Platforms rarely make these trade-offs visible because they lack a shared model of value streams and cross-functional dependencies. The result is a system that appears efficient and controlled in parts, but fragile.
Tool-Centered Rather Than Work-Centered Design
Many platforms are designed around what is easy to configure and sell rather than around how work happens. They assume linear processes, clear ownership, and stable boundaries. In practice, modern organizations rely on informal coordination, temporary teams, suppliers, and digital ecosystems that defy neat categorization. When tools force work to conform to their models, people create workarounds, parallel systems, or shadow processes. These adaptations are rational responses to tool limitations, but they further reduce visibility and trust in the reported data. Platforms end up documenting an idealized version of work rather than supporting the messy reality that produces value.
The Absence of System-Level Sensemaking
At their core, most GRC, ITSM, and cybersecurity platforms are record-keeping and workflow engines, not sensemaking tools. They collect and organize information but provide limited support for understanding how patterns emerge across leadership, structure, and behavior. Dashboards summarize indicators, but they rarely help users ask better questions about why the system behaves as it does. Complex systems require shared language, contextual interpretation, and ongoing dialogue. Without these capabilities, platforms reinforce reporting upward rather than learning across the system.
Toward Capabilities That Match Complexity
The reason most platform companies fall short is not a lack of sophistication or effort, but a mismatch between their underlying assumptions and the nature of complex socio-technical systems. Managing people, processes, and technologies requires capabilities that integrate intent, structure, and behavior around real value streams, over time. It requires tools that support learning, adaptation, and judgment, not just compliance and automation. Until platforms shift from managing artifacts to enabling system-level understanding and action, organizations will continue to invest heavily in tools that provide confidence on paper while leaving the real system only partially seen and poorly governed.
The DVMS as a System-Level Response
The Digital Value Management System (DVMS) addresses these shortcomings by starting from a fundamentally different premise: organizations must be understood and governed as living systems, not as collections of controls, tickets, or risk statements. Rather than centering on frameworks or tools, the DVMS focuses on shared, minimum viable capabilities that anchor leadership intent, structural design, and real behavior around actual value streams. It provides a common language that allows executives, GRC, IT, security, and operations to see how decisions, constraints, and human responses interact in practice, especially under stress and change. By integrating governance, resilience, assurance, and accountability into a single system view, the DVMS enables sensemaking rather than just reporting, helping organizations intervene where misalignment truly exists—whether in leadership signals, structural design, or behavioral norms—and thereby turning GRC from a retrospective compliance exercise into an active capability for steering complex digital systems.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
DVMS Cyber Resilience Professional Accredited Certification Training
Designing a Governance Overlay System that Transforms Digital Services into Resilient, Assured, and Accountable (GRAA) Digital Business Outcomes
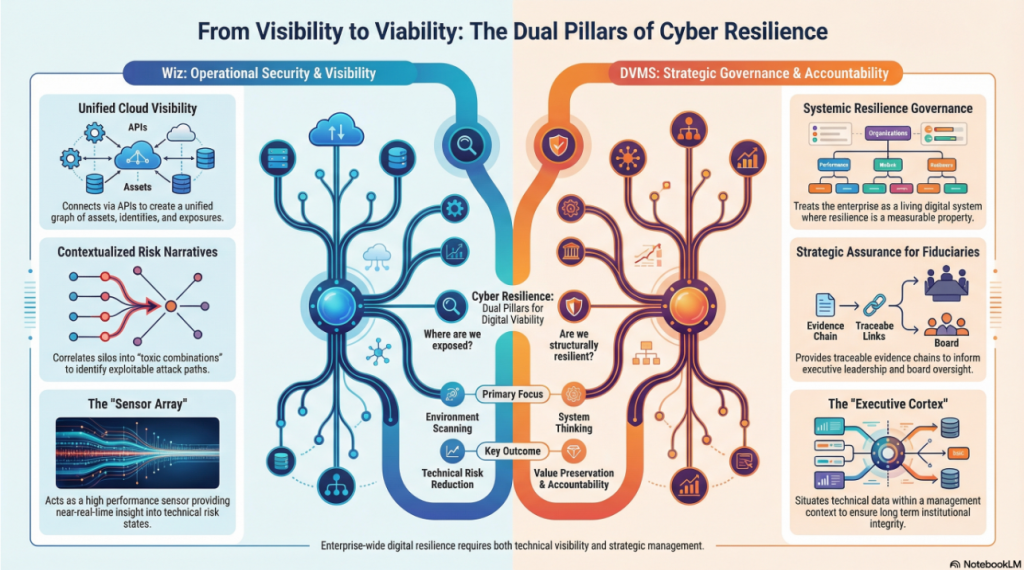
From Visibility to Viability – The Dual Pillars of Cyber Resilience
Explainer Video – The Dual Pillars of Cyber Resilience
As enterprises accelerated their adoption of complex, cloud-native architectures, they encountered a new order of complexity. Infrastructure dissolved into services, workloads became ephemeral, and security boundaries blurred. In that environment, Wiz emerged as a transformational force in cloud technical security, offering radical visibility and risk prioritization across multi-cloud ecosystems.
At the same time, a broader and more consequential challenge emerged, one that extends well beyond isolated technical misconfigurations or discrete vulnerabilities.
Modern organizations function as dynamic, highly interconnected digital ecosystems shaped by siloed frameworks, technologies, applications, processes, data flows, and human actors, all operating in continuous interaction. Within this complexity, risks and outcomes are not confined to individual components; they arise from the relationships and dependencies between them.
This is the domain in which the Digital Value Management System® (DVMS) operates.
While Wiz redefined how organizations see and secure cloud environments, DVMS is redefining how enterprises govern, assure, and account for resilient digital value as an integrated dimension of digital business performance.
The Digital Value Management System® (DVMS)
Explainer Video – What is a Digital Value Management System (DVMS)
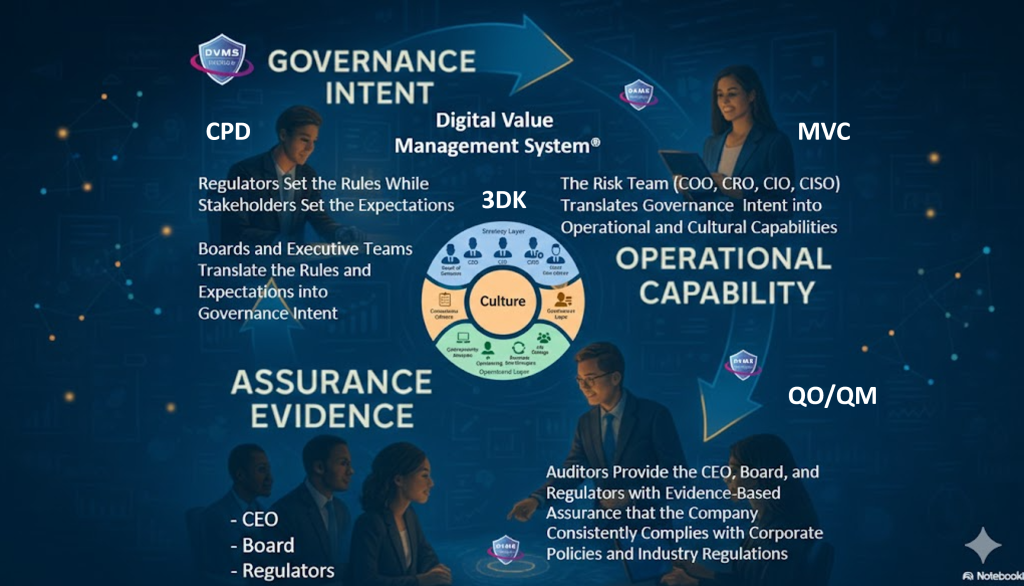
The DVMS is a governance overlay system that transforms digital services into resilient, assured, and accountable (GRAA) digital business outcomes.
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business performs under stress
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Learning – for governance and operational fine-tuning
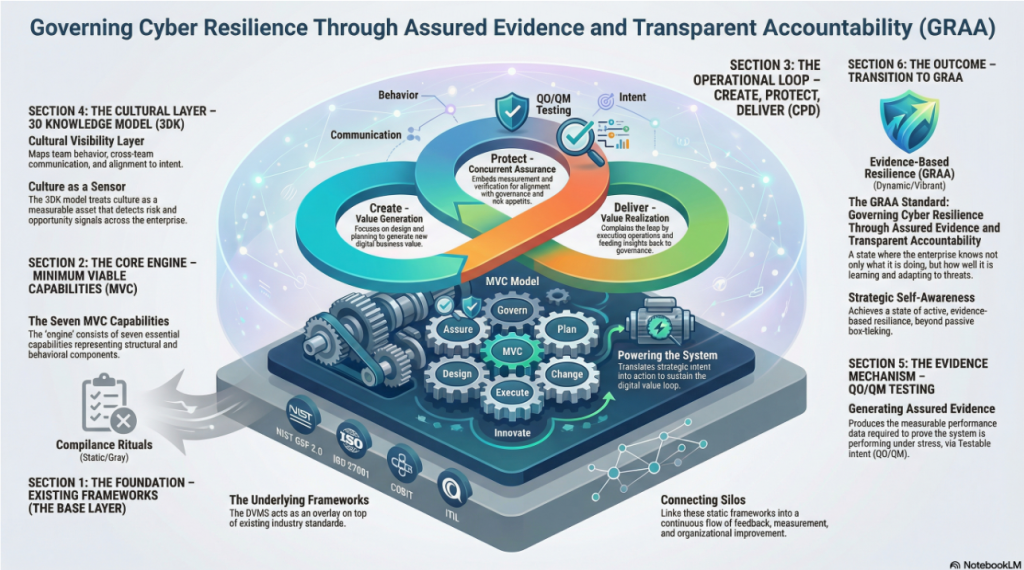
The DVMS GRAA Engine
Explainer Video – How a DVMS GRAA Engine Works
The overlay GRAA engine is powered by four DVMS models:
Create, Protect, and Deliver (CPD) – The CPD Model™ is a systems-based model within the DVMS that links strategy-risk and governance to execution to create, protect, and deliver digital business value as an integrated, continuously adaptive capability.
Minimum Viable Capabilities (MVC) – The Minimum Viable Capabilities (MVCs) model supports the seven essential, system-level organizational capabilities—Govern, Assure, Plan, Design, Change, Execute, and Innovate—required to reliably create, protect, and deliver digital business value in alignment with strategy-risk intent.
3D Knowledge (3DK) – The 3D Knowledge Model is a systems-thinking framework that maps team knowledge over time (past, present, future), cross-team collaboration, and alignment to strategic intent to ensure that organizational behavior, learning, and execution remain integrated and adaptive in delivering digital business value.
Question Outcome / Question Metric (QO/QM) – The QO/QM approach supports governance as testable intent by defining a clear Question Outcome (QO), the specific value or resilience condition that must be true at a given boundary, and pairing it with one or more Question Metrics (QM) that provide observable, decision-relevant evidence that the system can actually create, protect, and deliver that outcome under complex, living system operating conditions
The models then work together to operationalize the capabilities below that will transform digital strategy into governed, resilient, assured, and accountable digital value outcomes
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Benefits – Organizational and Leadership
Explainer Video – DVMS Organization and Leadership Benefits
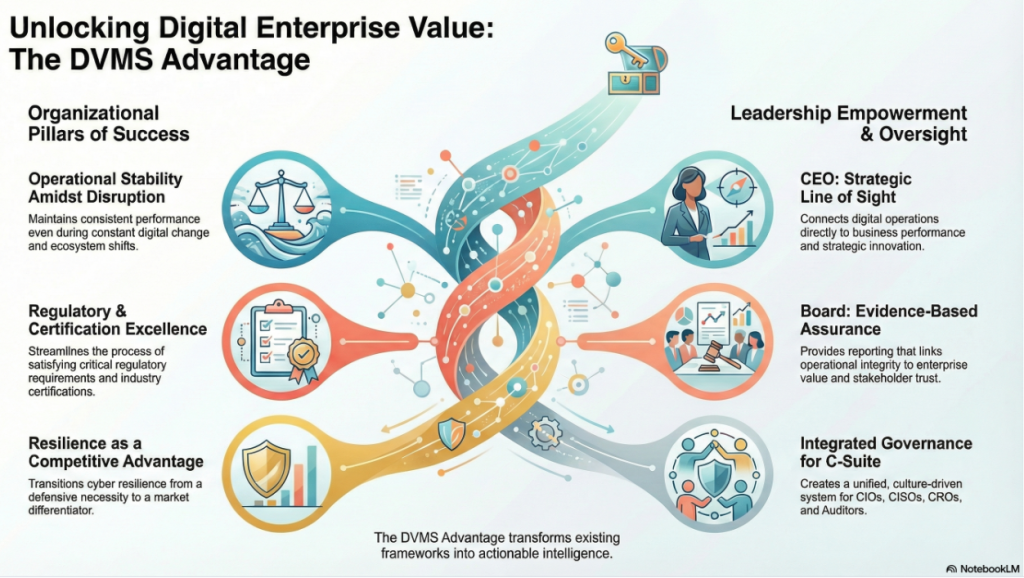
Instead of replacing existing operational frameworks and platforms, the DVMS elevates them, connecting and contextualizing their data into actionable intelligence that enables organizations to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across Complex Digital Ecosystems
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors, the DVMS provides a unified approach to organizational digital value management, operational resilience, and regulatory compliance.
DVMS – Accredited Certification Training Programs
Explainer Video – The DVMS Training Pathway to Cyber Resilience
The DVMS Institute’s accredited (APMG International) and certified (NCSC/GCHQ) training programs equip enterprises with the skills to build a governance overlay system that transforms digital services into resilient, assured, and accountable digital business outcomes.
Through structured learning, applied certification, and authoritative publications, the Institute teaches a disciplined, outcome-driven approach to managing resilience as an integrated dimension of digital business performance.
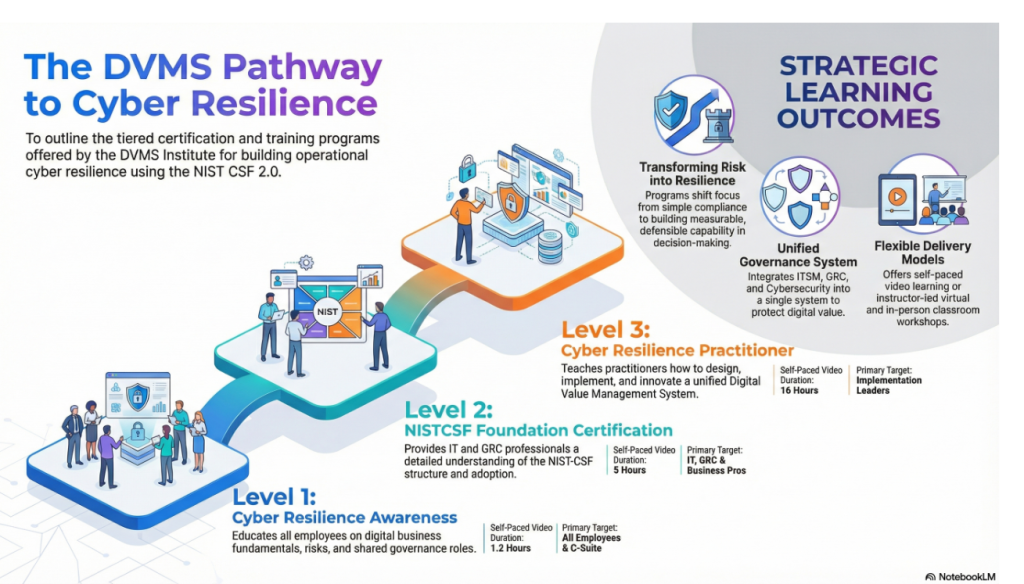
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness non-certification course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for resilience in complex digital ecosystems.
DVMS NISTCSF Cyber Resilience Foundation Certification Training
The DVMS NISTCSF Cyber Resilience Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for achieving resilience in complex digital ecosystems.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to build a unified governance, resilience, assurance, and accountability system designed to operationalize resilience in complex digital ecosystems.
Launching A DVMS Program
Explainer Video – Scaling a DVMS Program
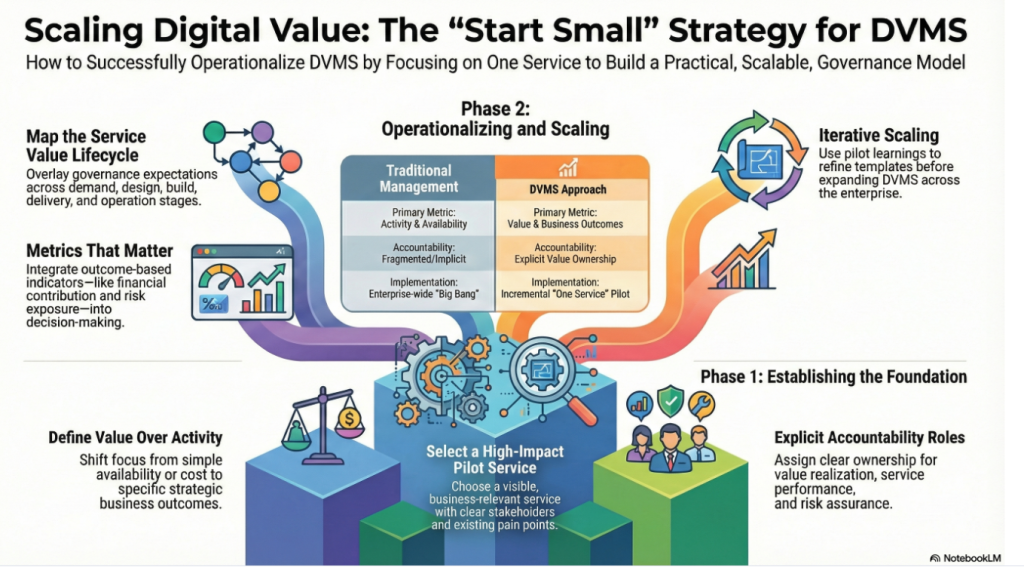
The DVMS FastTrack is a phased, iterative approach that helps organizations mature a DVMS program over time, rather than trying to do everything simultaneously. This approach breaks the DVMS journey into manageable phases of success.
It all starts with selecting the first digital service you want to operationalize with the new DVMS capabilities. That service will then serve as the blueprint for operationalizing DVMS across the remaining services.
DVMS Institute White Papers – The Assurance Mandate Series
Explainer Video – From Compliance Rituals to Evidence-Based Resilience
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
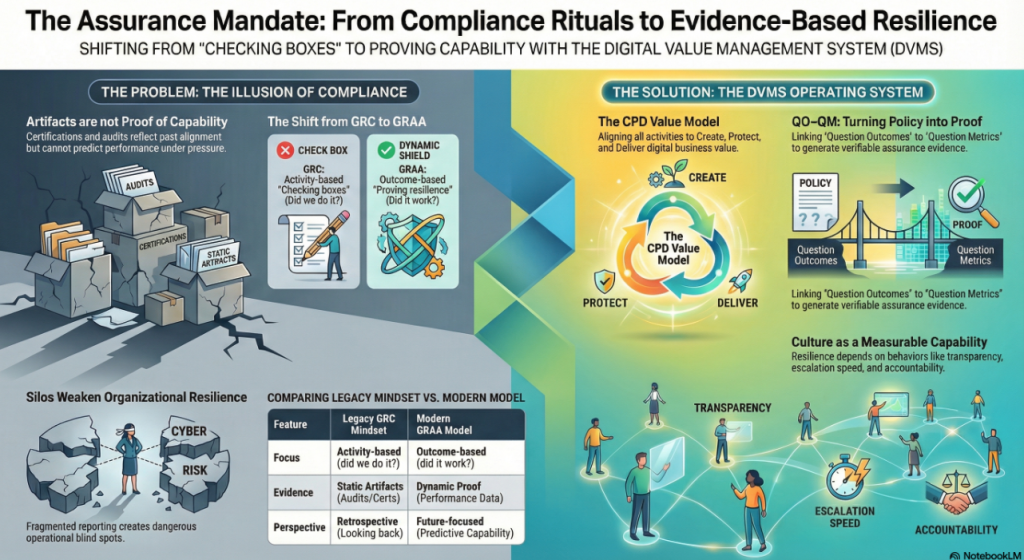
The Assurance Mandate Paper explains why traditional compliance artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
Company Brochures and Presentation
- DVMS One Pager
- DVMS Briefing Paper
- DVMS Company Brochure
- DVMS Product Brochure
- DVMS Company Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved