Resilience Is Designed into Daily Delivery– The GRAA Management Series Part 2
David Nichols – Co-Founder and Executive Director of the DVMS Institute
In Part One of this series, I argued that governance is about setting boundaries; this one is about the other side of that coin. Boundaries matter only if the system can behave within them, especially when conditions change.
That is what operational resilience is, not “we have a continuity plan,” but “the way we deliver work includes the ability to sustain outcomes through disruption, degrade safely when necessary, and recover predictably when possible.”
Most managers already understand this intuitively. What’s often missing is a shared design approach that connects daily delivery decisions to resilience outcomes and generates evidence along the way. That’s the gap this article closes.
It also aligns with what you’ve already put on the table in the GRAA Leadership Series. In Part Three, “The Hardest Control Surface in Your Enterprise Is Culture,” the point is not that culture is soft; it is that culture governs behavior at the moment decisions are made. In Part Four, “Seeing the System, A 3D View of Leadership, Structure and Behavior,” the point is that if you cannot see how intent, structure, and behavior align, you will continue to be surprised. And in Part Six, “Running on CPD,” the point is that Create, Protect, and Deliver is not a slogan; it is how the enterprise actually runs when it is healthy.
Managers live in that reality every day, and resilience has to be built there, not bolted on later.
The most useful definition of resilience for managers
“Resilience” can mean many things, so let’s start with the version managers can operationalize. Operational resilience is the ability to maintain a critical outcome despite disruptions, with controlled degradation and predictable recovery, without unacceptable harm. That definition matters because it gives you three practical design targets.
You need a way to sustain the outcome for as long as possible. You need a way to degrade safely when sustaining is no longer feasible. You need a way to recover in a known sequence, with verification, so you don’t restore a broken state and declare victory by accident. None of that requires heroics. It requires design.
Why resilience must be designed into delivery, not into documents
Here is a pattern most of us have seen. An organization builds robust documentation. It has policies, plans, and procedures. It passes audits. It has “owners.” On paper, it appears mature.
Then something changes. A dependency fails. A patch has an unexpected consequence. A supplier experiences an outage. A data store behaves differently under load. A team rotates, and tacit knowledge disappears. A process that was “fine” becomes fragile as the environment changes. The failure is rarely that you did not have a plan. The failure lies in the plan not being integrated into how work is delivered. It existed as an artifact, not as behavior.
This is precisely why the tone of the leadership series is essential. You are not trying to shame anyone. Most audit programs were built for a world where change was slower, dependencies were simpler, and controls could be evaluated as static conditions. In modern digital operations, resilience is dynamic, and evidence must come from how the system performs, not just from what the system claims.
So, the shift is not from GRC to “something else.” It is from artifacts to evidence and from static control assumptions to operational behavior. Managers are the ones who can make that shift real.
DVMS gives managers a design lens: Create, Protect, Deliver
The DVMS approach is effective here because it treats resilience as a property of the operating model rather than a separate program. It presents Create, Protect, and Deliver as three views of the same system. When managers adopt that lens, resilience stops being “the security team’s concern” or “the continuity team’s concern” and becomes a shared design discipline.
In Create, the resilience question is, “What outcome are we committing to, and what does acceptable performance look like under variance?” That is where you define criticality, tolerances, and priorities.
In Protect, the resilience question is, “What must not happen, which failure modes are unacceptable, and what constraints must always hold?” This is where safety, integrity, and non-negotiables reside.
In Deliver, the resilience question is, “How do we actually produce the outcome in the real world, with real dependencies, and what behaviors do we execute when things drift?” This is where resilience becomes a daily operating practice.
If you have read “Thriving on the Edge of Chaos: Managing at the Intersection of Value and Risk in the Digital Era,” the book reinforces this inseparability. Value and risk are not separate conversations; they are intertwined. They are the same conversation, viewed from different angles. Delivery is where that conversation becomes reality.
Resilience design patterns that managers can actually control
When managers hear “design resilience,” it can sound expensive or abstract. In practice, most early gains are achieved by embedding a few key patterns into daily delivery. One pattern is graceful degradation. Every critical service has functions that matter more than others. Resilience improves when you intentionally decide what can be reduced, delayed, or disabled first and build that into your operational playbooks. Graceful degradation is not only about technology; it’s also about people. It is also about process. What manual modes exist? What can be deferred without violating obligations? What can be rerouted? What can be throttled?
A second pattern is recovery sequencing. Recovery is not “everything comes back at once.” It is a controlled reassembly of dependencies and functions in the correct order. Managers can make recovery predictable by defining a sequence that aligns with business outcomes, not with team boundaries. That sequence should include verification points to ensure you have restored both integrity and availability.
A third pattern is verification discipline. Resilience is not just about restoring power; it’s about building a stronger foundation. It is about knowing the service is safe and trustworthy once it is back. Verification is where many organizations are surprised, because they restore systems that look “up” but are logically incorrect, incomplete, or inconsistent. A strong verification discipline defines what must be proven true before you declare normal operations.
A fourth pattern is dependency awareness. Most modern outcomes depend on shared platforms and suppliers. Resilience improves when you explicitly map those dependencies into your delivery design and build fallback paths or manual modes where feasible.
A fifth pattern is decision rights and escalation triggers, which we covered in Part 1. These are also resilience patterns. When decision rights are clear, and escalation is condition-based, you can execute degrade and recover behaviors quickly, proving what you did and why you did it.
These patterns are manager-friendly because they are grounded in reality. They describe how you work. They become real when they are incorporated into change planning, release readiness, incident response, and routine operational reviews.
The seam problem: where resilience actually fails
If you want a blunt truth that most managers know, it is this. Resilience usually fails at seams. The seam between product and operations. The seam between operations and security. The seam between internal teams and suppliers. The seam between “policy says” and “delivery must.” Seams create ambiguity. Ambiguity creates delay. Delay creates impact.
This is why the GRAA Leadership Series – Part Four, “Seeing the System, A 3D View of Leadership, Structure and Behavior,” matters so much. Managers often do the right things within their lane, but the system still fails because it is not aligned.
Resilience design is a seam discipline. It involves defining boundaries, designing degradation and recovery behaviors, and assigning evidence expectations across the seams. When done well, resilience stops being a scramble and becomes a practiced behavior.
A manager scenario: a controlled degradation beats an uncontrolled outage
Let’s use a scenario that is common enough to be real but generic enough to fit most enterprises. Your organization offers a customer-facing service that relies on identity, payment capabilities, and a data platform. You have good documentation, a continuity plan, and an incident process. Your control environment is decent.
Then a change lands, and your identity service begins to fail intermittently. Authentication latency increases, sessions drop, and some customers are unable to log in. The immediate question is, “Do we roll back, degrade, or wait?”
If governance is artifact-based, the team often hesitates. A rollback might violate a change policy. A degradation might breach a service commitment. Waiting might increase customer harm. Escalation becomes a meeting, not a trigger. If governance is boundary-based and resilience is designed into delivery, the team behaves differently.
They have agreed tolerances for authentication latency and failure rate. They know which features can be temporarily disabled. They have a pre-authorized degrade mode that preserves core transactions while limiting non-critical functionality. They know who can authorize the change and when escalation is necessary.
They execute the degrade mode. They communicate clearly. They capture evidence as they operate. They roll back if the tolerance is further threatened. They recover in a known sequence and verify integrity before declaring normal.
From the outside, customers experience a degraded service, not a total collapse. From the inside, managers see a system behaving as designed. That is the difference between “having a plan” and “designing resilience into delivery.”
Notice what also happened. Auditing becomes easier. Not because you produced more documents, but because you produced operational evidence that the system operated within defined boundaries. Evidence is not a scramble. It is the natural output of disciplined delivery.
How managers build “degrade and recover” into daily work
So how do you do this without launching a major initiative? You make resilience a regular part of delivery planning and operational cadence. When you plan changes, you don’t just ask, “Is it tested?” You ask, “What is the degradation mode if this goes wrong? What is the rollback path? What is the recovery sequence? And what do we verify?”
When reviewing incidents and near misses, you do not stop at identifying the root cause. You ask, “Did we act within boundaries? Did decision rights help or hinder? What evidence was missing? And what should we design into the next iteration?”
When you work with risk, security, and audit partners, you do not treat them as the team that approves work. You treat them as the team that helps define constraints and evidence expectations, enabling you to move faster with confidence.
This aligns with the spirit of the GRAA Leadership Series – Part Six, “Running on CPD.” CPD is not a separate process. It is an operating rhythm. Managers operationalize that rhythm by embedding resilience patterns into delivery, not by creating a parallel program.
A simple management practice: one outcome, one playbook, one rehearsal
If you want a practical starting point, here’s a discipline that works. Pick one critical outcome. Not a system, an outcome. Define a playbook for degradation and recovery. Keep it short. Make it executable. Then rehearse it. Even a tabletop is enough. You are not practicing theater. You are discovering seams.
During the rehearsal, watch for four situations where decision rights are unclear, escalation triggers are vague, recovery sequencing is disputed, and verification is missing. Those are your design gaps. They are also your audit and assurance gaps, because without those elements, evidence will be thin when scrutiny arrives.
After the rehearsal, update the playbook and capture the evidence expectations. Make that playbook part of daily delivery, part of release readiness, part of operational reviews. This is how resilience becomes a behavior, not a document.
Why is this positive for GRC, not a rejection of it?
It is worth saying this explicitly because managers are often caught in the middle. GRC exists for a reason. Audit exists for a reason. They protect the enterprise, its customers, and usually its license to operate. The frustration is not that these functions exist. The frustration arises when the enterprise invests heavily in artifacts yet still cannot demonstrate resilient behavior.
If you shift to evidence-based resilience, you are helping GRC and audit do their jobs. You are providing them with a more transparent chain of events from intent to operation. You are reducing the paper chase because evidence is continuously generated through everyday work.
This also respects the reality that managers live with. You cannot always prevent incidents. You can avoid chaos. You can prevent slow decisions. You can prevent avoidable harm. And you can prove what you did and why you did it. That is where evidence trumps artifacts without devaluing artifacts.
What to do this week
If you are a manager and you want to act on this without waiting for a program, here’s a simple move. Select one outcome that your team supports, which has a real business impact. Define the degradation mode and recovery sequence. Identify what must be verified before declaring a normal condition. Align decision rights and escalation triggers with the boundaries you set in Part One. Then run one rehearsal, even if it is just the right people in a room for 45 minutes. Capture what you learned. Update the playbook. Make evidence expectations explicit.
In Part Three – Assurance Is Operational Evidence, Not Compliance Artifacts, we focus on assurance, not as documentation, but as operational evidence that proves your system can operate within its boundaries, and that your decisions can be defended without a scramble for artifacts.
About the Author

Dave is the Executive Director of the DVMS Institute.
Dave spent his “formative years” on US Navy submarines. There, he learned complex systems, functioning in high-performance teams, and what it takes to be an exceptional leader. He took those skills into civilian life and built a successful career leading high-performance teams in software development and information service delivery.
DVMS Cyber Resilience Professional Accredited Certification Training
Designing a Governance Overlay System that Transforms Digital Services into Resilient, Assured, and Accountable (GRAA) Digital Business Outcomes
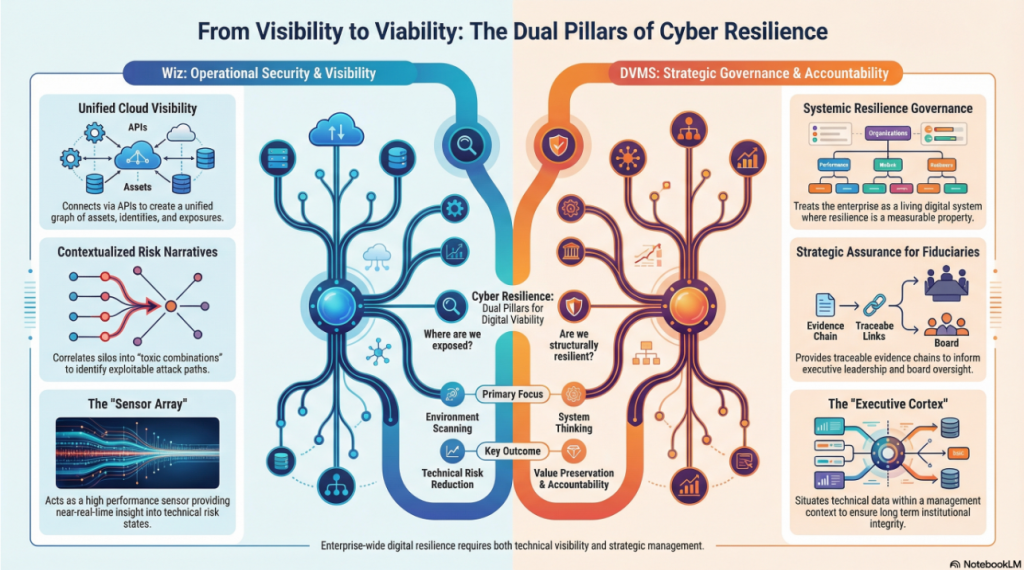
From Visibility to Viability – The Dual Pillars of Cyber Resilience
Explainer Video – The Dual Pillars of Cyber Resilience
As enterprises accelerated their adoption of complex, cloud-native architectures, they encountered a new order of complexity. Infrastructure dissolved into services, workloads became ephemeral, and security boundaries blurred. In that environment, Wiz emerged as a transformational force in cloud technical security, offering radical visibility and risk prioritization across multi-cloud ecosystems.
At the same time, a broader and more consequential challenge emerged, one that extends well beyond isolated technical misconfigurations or discrete vulnerabilities.
Modern organizations function as dynamic, highly interconnected digital ecosystems shaped by siloed frameworks, technologies, applications, processes, data flows, and human actors, all operating in continuous interaction. Within this complexity, risks and outcomes are not confined to individual components; they arise from the relationships and dependencies between them.
This is the domain in which the Digital Value Management System® (DVMS) operates.
While Wiz redefined how organizations see and secure cloud environments, DVMS is redefining how enterprises govern, assure, and account for resilient digital value as an integrated dimension of digital business performance.
The Digital Value Management System® (DVMS)
Explainer Video – What is a Digital Value Management System (DVMS)
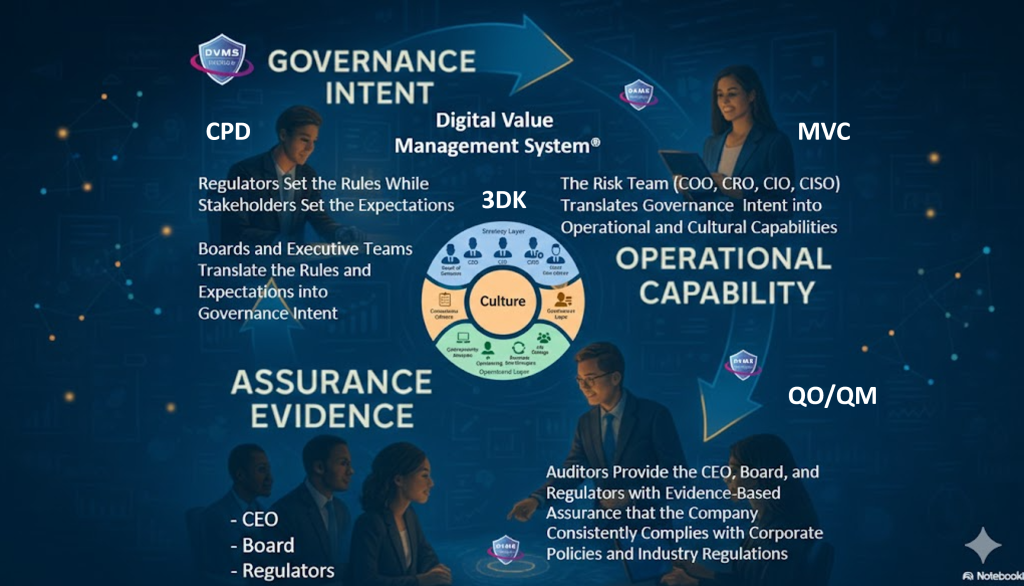
The DVMS is a governance overlay system that transforms digital services into resilient, assured, and accountable (GRAA) digital business outcomes.
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business performs under stress
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Learning – for governance and operational fine-tuning
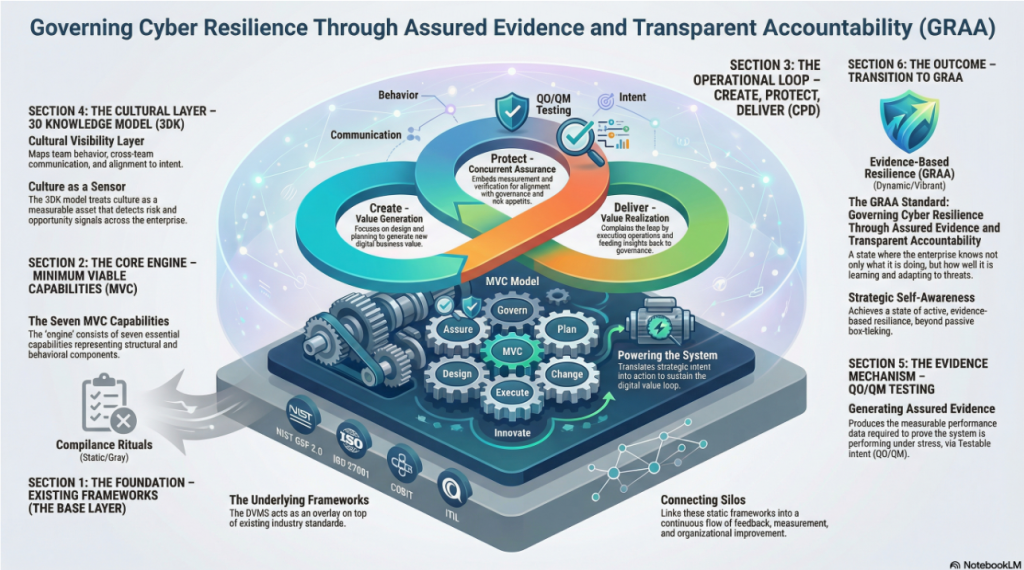
The DVMS GRAA Engine
Explainer Video – How a DVMS GRAA Engine Works
The overlay GRAA engine is powered by four DVMS models:
Create, Protect, and Deliver (CPD) – The CPD Model™ is a systems-based model within the DVMS that links strategy-risk and governance to execution to create, protect, and deliver digital business value as an integrated, continuously adaptive capability.
Minimum Viable Capabilities (MVC) – The Minimum Viable Capabilities (MVCs) model supports the seven essential, system-level organizational capabilities—Govern, Assure, Plan, Design, Change, Execute, and Innovate—required to reliably create, protect, and deliver digital business value in alignment with strategy-risk intent.
3D Knowledge (3DK) – The 3D Knowledge Model is a systems-thinking framework that maps team knowledge over time (past, present, future), cross-team collaboration, and alignment to strategic intent to ensure that organizational behavior, learning, and execution remain integrated and adaptive in delivering digital business value.
Question Outcome / Question Metric (QO/QM) – The QO/QM approach supports governance as testable intent by defining a clear Question Outcome (QO), the specific value or resilience condition that must be true at a given boundary, and pairing it with one or more Question Metrics (QM) that provide observable, decision-relevant evidence that the system can actually create, protect, and deliver that outcome under complex, living system operating conditions
The models then work together to operationalize the capabilities below that will transform digital strategy into governed, resilient, assured, and accountable digital value outcomes
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
DVMS Benefits – Organizational and Leadership
Explainer Video – DVMS Organization and Leadership Benefits
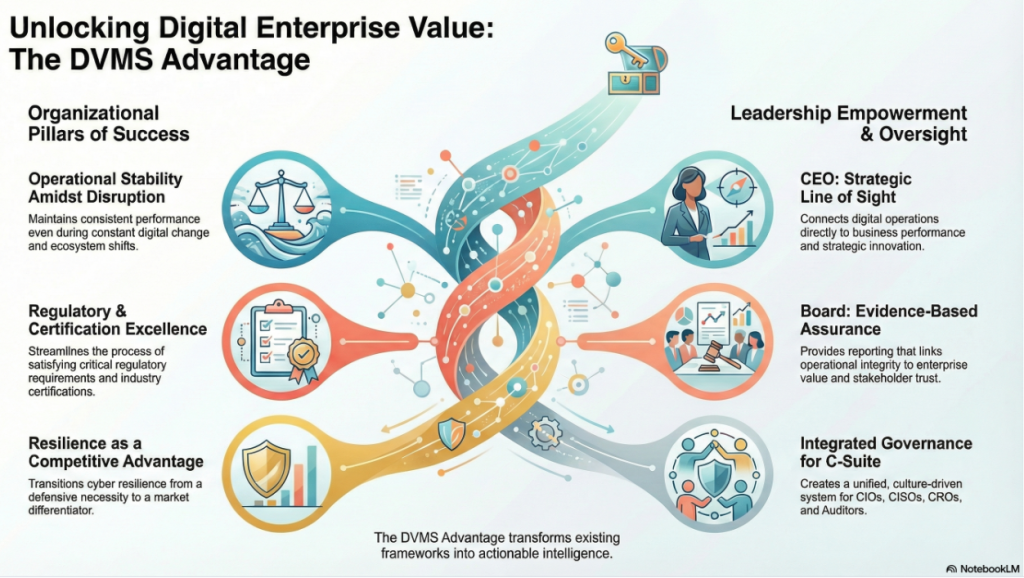
Instead of replacing existing operational frameworks and platforms, the DVMS elevates them, connecting and contextualizing their data into actionable intelligence that enables organizations to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across Complex Digital Ecosystems
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors, the DVMS provides a unified approach to organizational digital value management, operational resilience, and regulatory compliance.
DVMS – Accredited Certification Training Programs
Explainer Video – The DVMS Training Pathway to Cyber Resilience
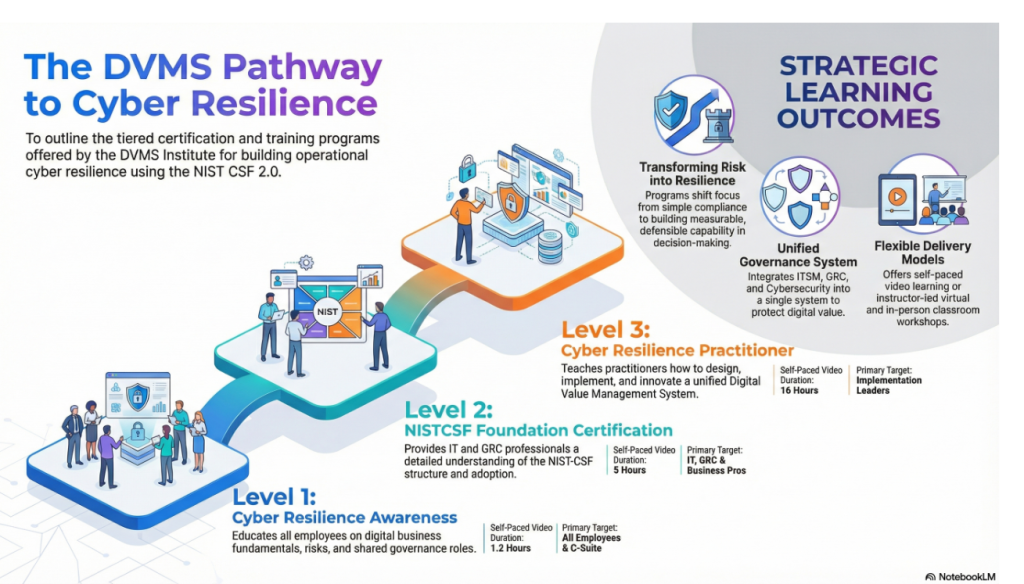
The DVMS Institute’s accredited (APMG International) and certified (NCSC/GCHQ) training programs equip enterprises with the skills to build a governance overlay system that transforms digital services into resilient, assured, and accountable digital business outcomes.
Through structured learning, applied certification, and authoritative publications, the Institute teaches a disciplined, outcome-driven approach to managing resilience as an integrated dimension of digital business performance.
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness non-certification course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for resilience in complex digital ecosystems.
DVMS NISTCSF Cyber Resilience Foundation Certification Training
The DVMS NISTCSF Cyber Resilience Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for achieving resilience in complex digital ecosystems.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to build a unified governance, resilience, assurance, and accountability system designed to operationalize resilience in complex digital ecosystems.
Launching A DVMS Program
Explainer Video – Scaling a DVMS Program
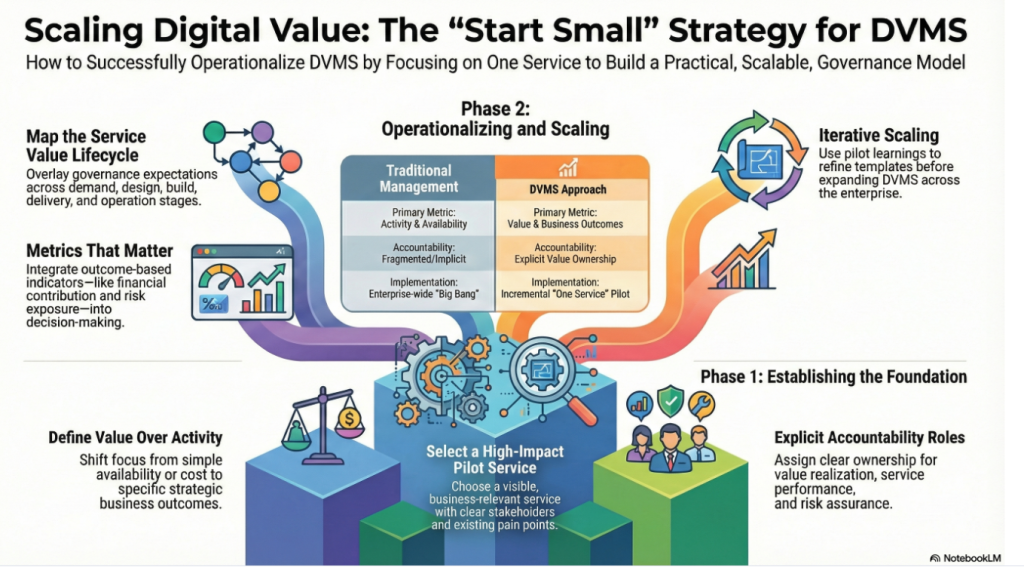
The DVMS FastTrack is a phased, iterative approach that helps organizations mature a DVMS program over time, rather than trying to do everything simultaneously. This approach breaks the DVMS journey into manageable phases of success.
It all starts with selecting the first digital service you want to operationalize with the new DVMS capabilities. That service will then serve as the blueprint for operationalizing DVMS across the remaining services.
DVMS Institute White Papers – The Assurance Mandate Series
Explainer Video – From Compliance Rituals to Evidence-Based Resilience
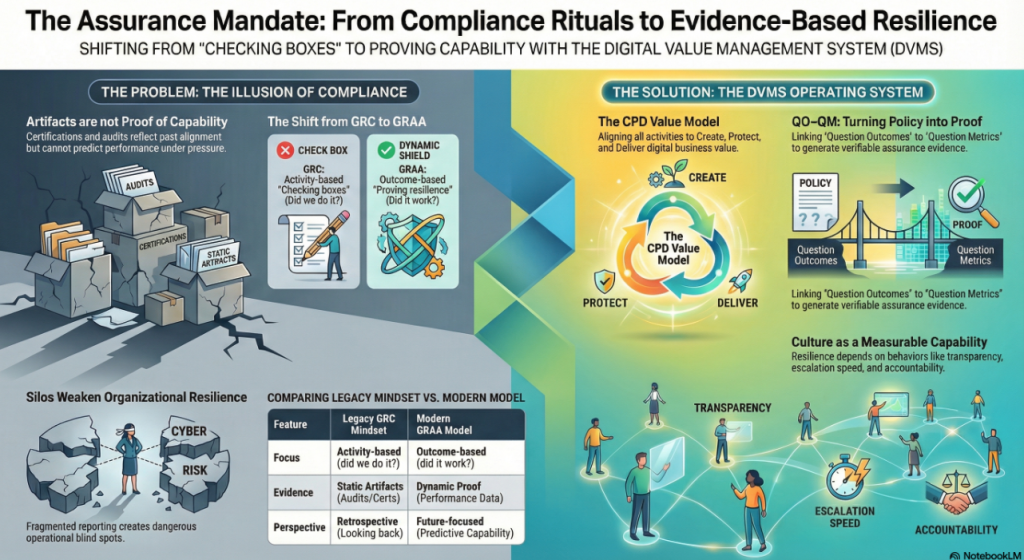
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
The Assurance Mandate Paper explains why traditional compliance artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
Company Brochures and Presentation
- DVMS One Pager
- DVMS Briefing Paper
- DVMS Company Brochure
- DVMS Product Brochure
- DVMS Company Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved