Why Cybersecurity and Risk Management Professionals Often Do Not Truly Understand Their Digital Business
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
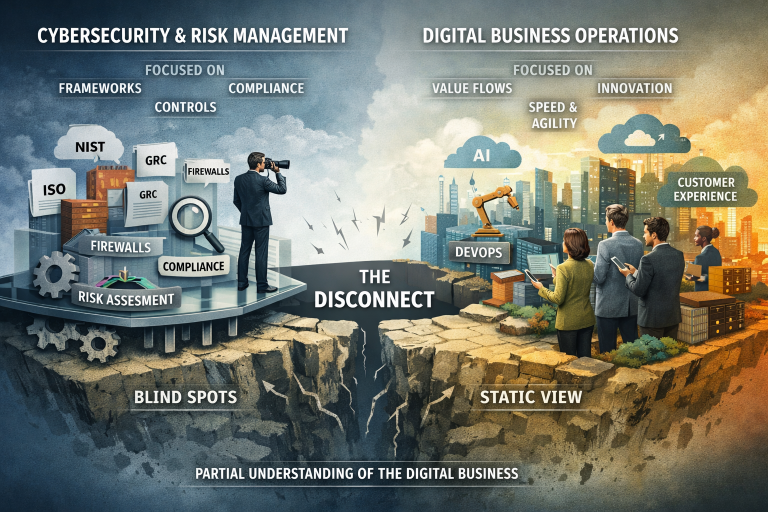
Modern organizations invest heavily in cybersecurity and risk management. They adopt recognized frameworks, hire credentialed professionals, deploy sophisticated tools, and comply with regulatory requirements. Yet, despite these efforts, catastrophic digital failures continue to occur—often in organizations that appear, on paper, to be well-governed and well-protected. This persistent disconnect suggests a deeper issue: many cybersecurity and risk management professionals do not truly understand the digital businesses they are meant to protect.
This lack of understanding is not due to incompetence or negligence. Instead, it is a structural and conceptual problem rooted in how cybersecurity and risk management have evolved as disciplines—separate from how digital value is created, delivered, and sustained.
A Control-Centric View Detached from Business Reality
Cybersecurity and risk management functions are typically organized around controls, compliance, and technical assets. Professionals are trained to identify threats, vulnerabilities, and control gaps; assess risks; and ensure alignment with standards such as the NIST CSF, ISO 27001, or regulatory mandates. While these activities are necessary, they are rarely sufficient to capture the true nature of a digital business’s operations.
Digital businesses are not collections of isolated systems. They are dynamic networks of products, services, data flows, partners, customers, and automated decision-making processes. Value is created through interactions across organizational, technological, and ecosystem boundaries. When cybersecurity professionals focus primarily on systems, controls, and compliance artifacts, they often lose sight of how those elements contribute—or fail to contribute—to business outcomes.
As a result, security is managed as an overlay of technical safeguards rather than as an intrinsic property of how value is designed, delivered, and governed.
Functional Silos Fragment Understanding
Another reason cybersecurity and risk professionals struggle to understand the digital business is organizational fragmentation. Cybersecurity, risk management, IT operations, software development, compliance, and business leadership typically operate in separate silos, each with its own language, incentives, and success metrics.
Security teams focus on threat mitigation. Risk teams focus on registers and assessments. IT focuses on availability and performance. Development teams prioritize speed and innovation. Business leaders focus on growth, customer experience, and revenue. Rarely is there a shared model that explains how these perspectives fit together to sustain digital value under normal and stressed conditions.
Without an integrated view, cybersecurity professionals see only a slice of the business. They may understand networks and applications in technical terms, but not how those systems enable specific value propositions, revenue streams, or regulatory obligations. When failures occur—such as breaches, outages, or systemic risk events—they often emerge at the boundaries between silos, where responsibility and visibility are weakest.
Risk Is Abstracted Away from Value
Risk management frameworks commonly emphasize abstract risk statements, likelihoods, and impacts. While helpful in reporting, these abstractions can obscure the fundamental mechanisms by which digital value is compromised. Risk becomes something to be documented and rated, rather than something to be actively managed within operational processes.
This abstraction encourages a false sense of control. Organizations may believe they “understand their risks” because they have comprehensive risk registers and dashboards, even though they lack a concrete understanding of how digital services behave under stress, how dependencies cascade, or how decisions are made in real time.
Proper understanding of a digital business requires tracing risk to specific value flows: how data moves, how decisions are automated, how services depend on third parties, and how failures propagate. Many cybersecurity and risk professionals are not equipped—or organizationally empowered—to perform this kind of analysis.
Frameworks Are Adopted, Not Integrated
Most organizations adopt multiple frameworks: cybersecurity frameworks, risk frameworks, IT service management models, development methodologies, and compliance standards. These frameworks are often implemented independently, each addressing a narrow concern. While individually sound, together they form a fragmented governance landscape.
Cybersecurity professionals may be fluent in one or more frameworks, but fluency does not equate to integration. Frameworks describe what should exist, not how digital value functions across the enterprise. When frameworks are treated as checklists rather than as components of a coherent system, professionals end up managing compliance artifacts rather than addressing business realities.
This creates a dangerous illusion: the organization appears mature and well governed, while its underlying digital operations remain poorly understood and weakly coordinated.
Technology Has Outpaced Governance Models
Digital businesses increasingly rely on cloud services, APIs, automation, AI, and complex supply chains. These technologies introduce speed, scale, and non-linearity that traditional governance and risk models were never designed to handle. Decisions are automated, systems adapt dynamically, and failures can propagate faster than human oversight.
Many cybersecurity and risk professionals were trained in an era of relatively static systems and linear processes. Applying those mental models to modern digital ecosystems leads to blind spots. The business evolves faster than the governance structures meant to oversee it, leaving professionals managing yesterday’s risks while tomorrow’s failures accumulate unnoticed.
Understanding Requires a Shift in Perspective
To truly understand a digital business, cybersecurity and risk management professionals must shift from a control-centric, siloed mindset to a value-centric, systems-based perspective. This means understanding not just assets and threats, but how value is intentionally designed, operationalized, measured, and protected across its entire lifecycle.
It requires seeing cybersecurity not as a defensive function, but as a contributor to digital trust, resilience, and performance. It requires integrating risk management into how decisions are made, services are designed, and outcomes are governed—rather than treating risk as an after-the-fact assessment.
Until this shift occurs, organizations will continue to experience failures not because they lack frameworks or expertise, but because those frameworks and experts do not reflect how the digital business truly works.
Conclusion
Cybersecurity and risk management professionals are highly skilled within their domains, yet often constrained by outdated models, fragmented structures, and abstracted views of risk. In a world where digital value is complex, dynamic, and deeply interconnected, partial understanding is no longer sufficient.
True digital resilience depends on understanding the business as a living system—one where value, risk, security, and performance are inseparable. Until cybersecurity and risk management evolve to reflect this reality, organizations will remain vulnerable at the very boundaries where their digital value is created.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
DVMS Cyber Resilience Professional Accredited Certification Training
Teaching Enterprises How to Govern, Assure, and Account for Operational Resilience in Living Digital Ecosystems
Moving From Paper to Practice-Based Operational Resilience
Explainer Video – Governing By Assurance
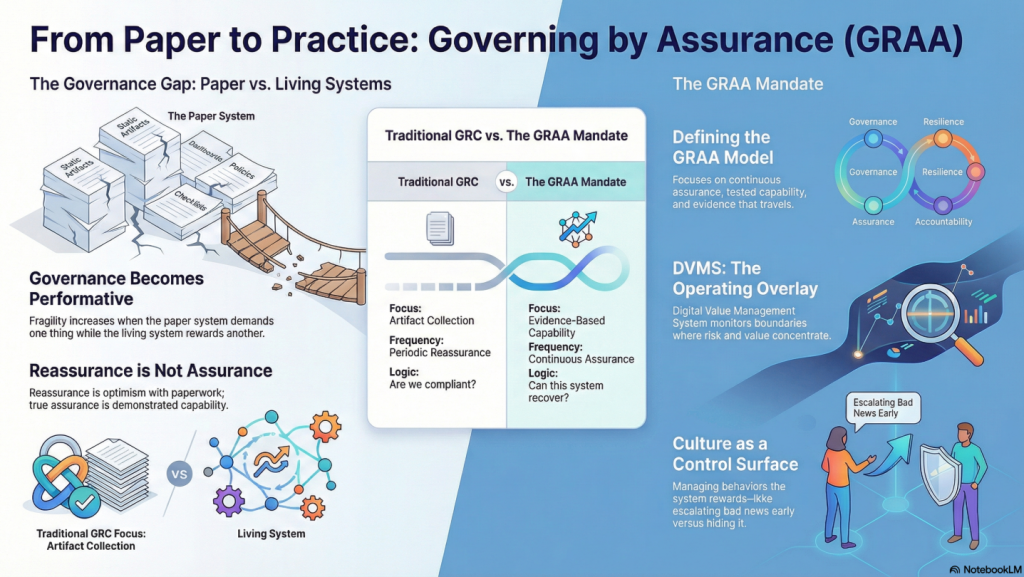
Despite an abundance of frameworks, metrics, and dashboards, many leaders still lack a clear line of sight into how their digital value streams perform when conditions deteriorate.
Strategic intent, organizational structures, and day-to-day behaviors are evaluated separately, producing static snapshots that fail to reveal how decisions, dependencies, and human actions interact within a dynamic digital system.
The result is governance that appears comprehensive in documentation yet proves fragile under pressure, leaving leaders to reconcile disconnected controls rather than systematically strengthen operational resilience.
What is needed is a framework-agnostic operating overlay that enables operational resilience to be governed, assured, and accounted for coherently across complex, living digital ecosystems.
DVMS Institute White Papers – The Assurance Mandate Series
Explainer Video – From Compliance Rituals to Evidence-Based Resilience
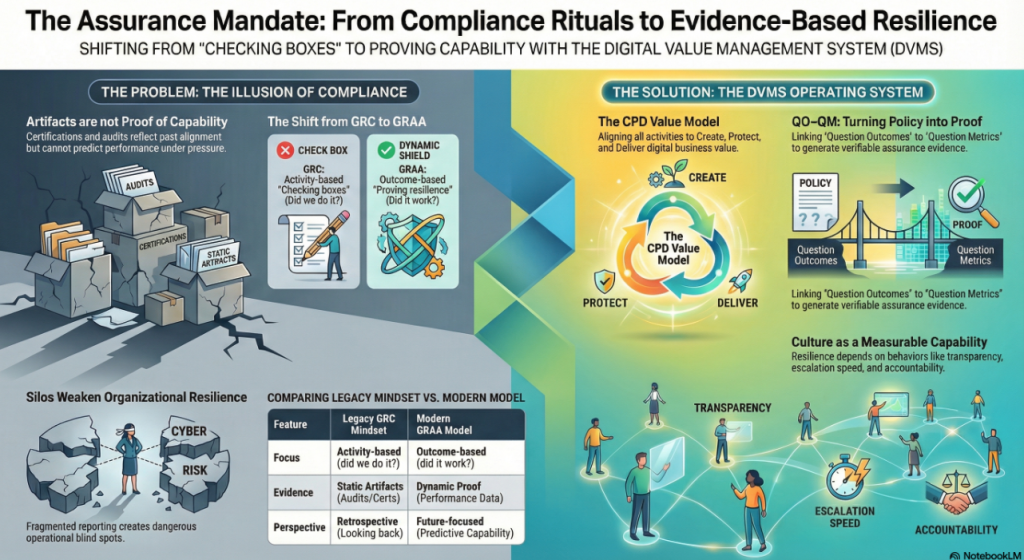
The whitepapers below present a clear progression from compliance-driven thinking to a modern system of Governance, Resilience, Assurance, and Accountability (GRAA). Together, they define an evidence-based approach to building and governing resilient digital enterprises.
The Assurance Mandate Paper explains why traditional compliance artifacts offer reassurance, not proof, and challenges boards to demand evidence that value can be created, protected, and delivered under stress.
The Assurance in Action Paper shows how DVMS turns intent into execution by translating outcomes into Minimum Viable Capabilities, aligning frameworks through the Create–Protect–Deliver model, and producing measurable assurance evidence of real performance.
The Governing by Assurance Paper extends this model to policy and regulation, positioning DVMS as a learning overlay that links governance intent, operational capability, and auditable evidence—enabling outcome-based governance and proof of resilience through measurable performance data.
The Digital Value Management System® (DVMS)
Explainer Video – What is a Digital Value Management System (DVMS)
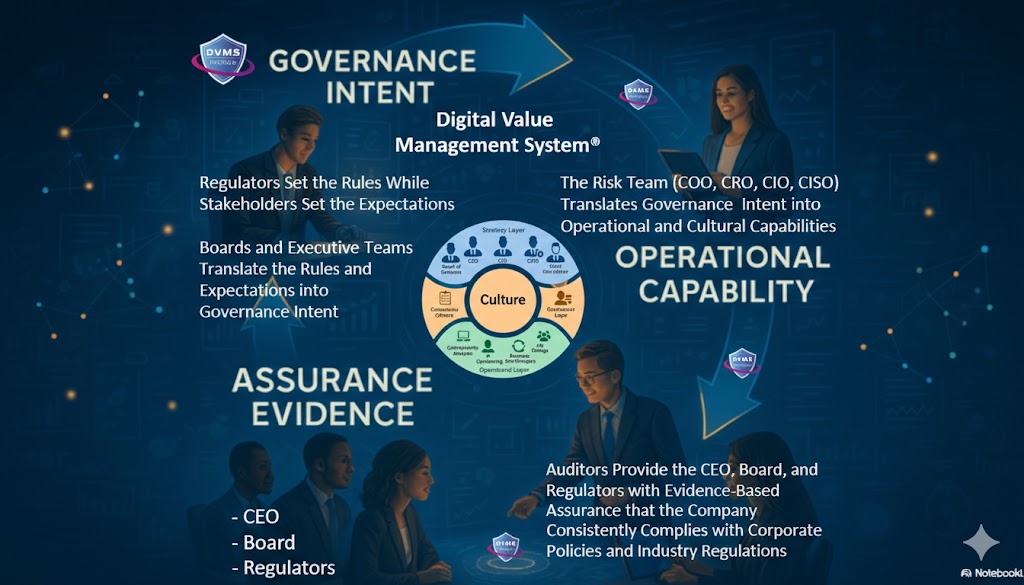
The DVMS is an overlay management system that governs, assures, and accounts for operational resilience in complex, living digital ecosystems. It does so by ensuring living-system outcomes account for paper-system intent.
At its core, the DVMS is a simple but powerful integration of:
- Governance Intent – shared expectations and accountabilities
- Operational Capabilities – how the digital business performs
- Assurance Evidence – proof that outcomes are achieved and accountable
- Cultural Learning – for governance intent and operational capability fine-tuning
Underpinning this integration are three distinctive DVMS models
Create, Protect, and Deliver (CPD) – The CPD Model™ is a systems-based model within the DVMS that links strategy-risk and governance to execution to create, protect, and deliver digital business value as an integrated, continuously adaptive capability.
3D Knowledge (3DK) – The 3D Knowledge Model is a systems-thinking framework that maps team knowledge over time (past, present, future), cross-team collaboration, and alignment to strategic intent to ensure that organizational behavior, learning, and execution remain integrated and adaptive in delivering digital business value.
Minimum Viable Capabilities (MVC) – The Minimum Viable Capabilities (MVCs) model supports the seven essential, system-level organizational capabilities—Govern, Assure, Plan, Design, Change, Execute, and Innovate—required to reliably create, protect, and deliver digital business value in alignment with strategy-risk intent.
The models work together to enable the following organizational capabilities:
A Governance Overlay that replaces fragmentation with unity. The DVMS provides organizations with a structured way to connect strategy with day-to-day execution. Leaders gain a consistent mechanism to direct, measure, and validate performance across every system responsible for digital value.
A Behavioral Engine that drives high-trust, high-velocity decision-making. The DVMS embeds decision models and behavioral patterns that help teams think clearly and act confidently, even in uncertain situations. It is engineered to reduce friction, prevent blame-based cultures, and strengthen organizational reliability.
A Learning System that makes culture measurable, adaptable, and scalable. Culture becomes a managed asset—not an abstract concept. The DVMS provides a repeatable way to observe behavior, collect evidence, learn from outcomes, and evolve faster than threats, disruptions, or market shifts.
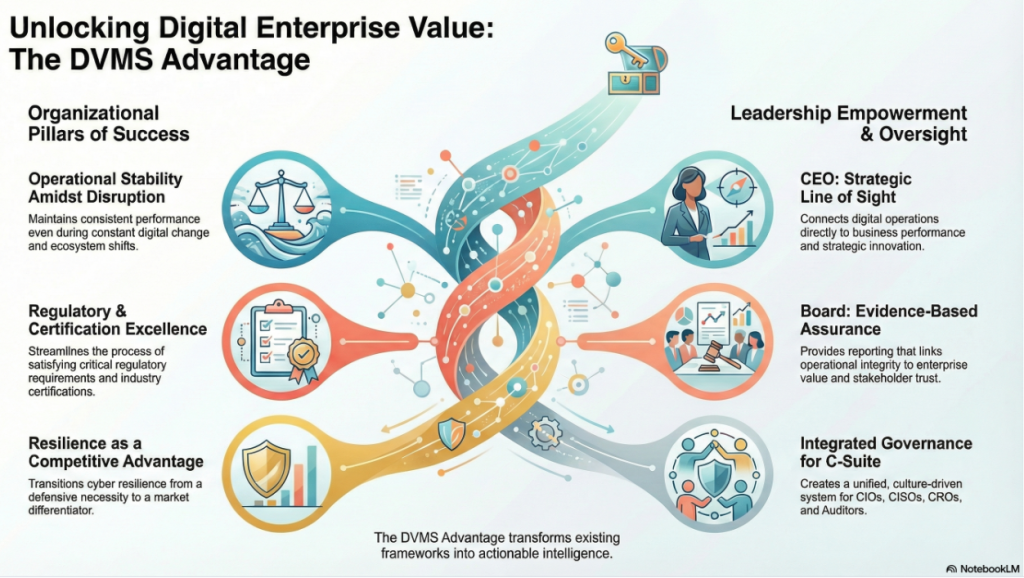
DVMS Benefits – Organizational and Leadership
Explainer Video – DVMS Organization and Leadership Benefits
Instead of replacing existing operational frameworks and platforms, the DVMS elevates them, connecting and contextualizing their data into actionable intelligence that validates performance and exposes the reasons behind unmet outcomes.
By adopting a DVMS, enterprises are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
The Digital Value Management System (DVMS) provides leaders with a unified, evidence-based approach to governing and enhancing their digital enterprise, aligning with regulatory requirements and stakeholder expectations.
For the CEO, the DVMS provides a clear line of sight between digital operations, business performance, and strategic outcomes—turning governance and resilience into enablers of growth and innovation rather than cost centers.
For the Board of Directors, the DVMS provides ongoing assurance that the organization’s digital assets, operations, and ecosystem are governed, protected, and resilient—supported by evidence-based reporting that directly links operational integrity to enterprise value and stakeholder trust.
For the CIO, CRO, CISO, and Auditors, an integrated, adaptive, and culture-driven governance and assurance management system that enhances digital business performance, resilience, trust, and accountability.
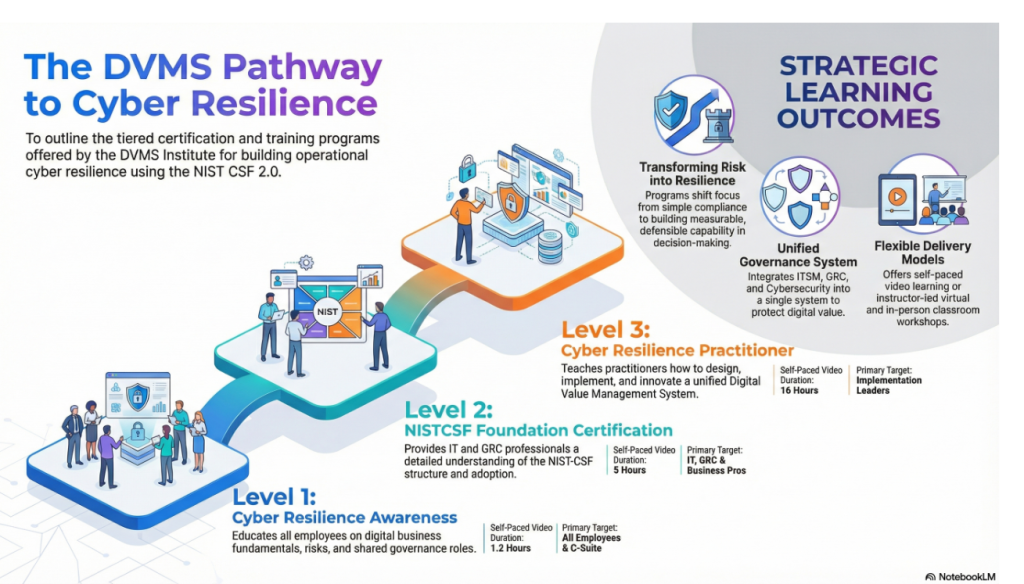
DVMS – Accredited Certification Training Program
Explainer Video – The DVMS Training Pathway to Cyber Resilience
The Digital Value Management System® (DVMS) training programs teach leadership, practitioners, and employees how to integrate fragmented systems into a unified, culture-driven governance and assurance system that accounts for the resilience of digital value within a living digital ecosystem.
DVMS Cyber Resilience Awareness Training
The DVMS Cyber Resilience Awareness course and its accompanying body of knowledge publication educate all employees on the fundamentals of digital business, its associated risks, the NIST Cybersecurity Framework, and their role within a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS NISTCSF Cyber Resilience Foundation Certification Training
The DVMS NISTCSF Cyber Resilience Foundation certification training course and its accompanying body of knowledge publications provide ITSM, GRC, Cybersecurity, and Business professionals with a detailed understanding of the NIST Cybersecurity Framework and its role in a shared model of governance, resilience, assurance, and accountability for creating, protecting, and delivering digital value.
DVMS Cyber Resilience Practitioner Certification Training
The DVMS Practitioner certification training course and its accompanying body of knowledge publications teach ITSM, GRC, Cybersecurity, and Business practitioners how to elevate investments in ITSM, GRC, Cybersecurity, and AI business systems by integrating them into a unified governance, resilience, assurance, and accountability system designed to proactively identify and mitigate the cyber risks that could disrupt operations, erode resilience, or diminish client trust.
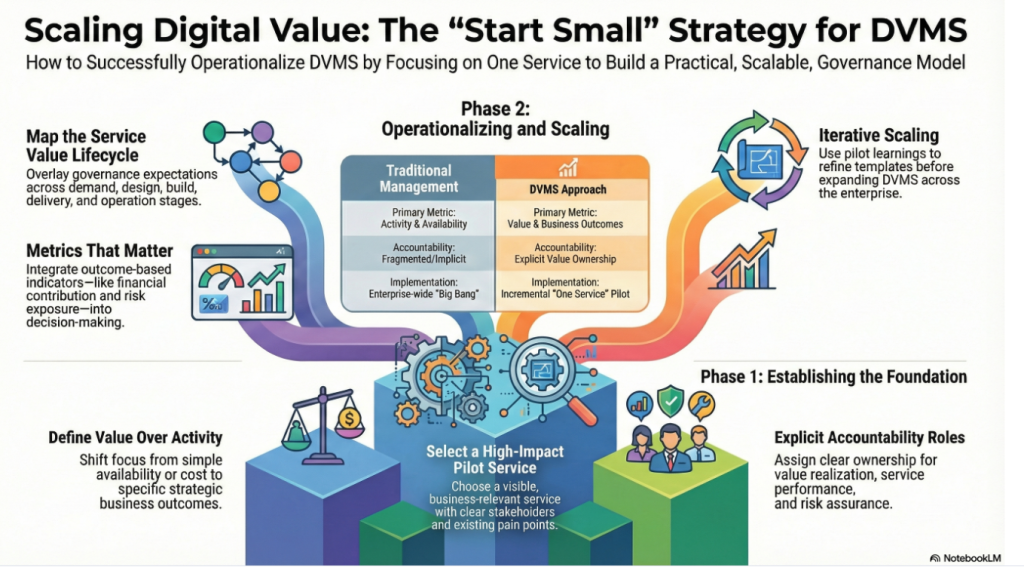
A FastTrack Approach to Launching Your DVMS Program
Explainer Video – Scaling a DVMS Program
The DVMS FastTrack approach is a phased, iterative approach that helps organizations mature their DVMS over time, rather than trying to do everything simultaneously.
This approach breaks the DVMS journey into manageable phases of success. It all starts with selecting the first digital service you want to make cyber resilient. Once that service becomes resilient, it becomes the blueprint for operationalizing cyber resilience across the enterprise and its supply chain.
Company Brochures and Presentation
Explainer Videos
- DVMS Architecture Video: David Moskowitz explains the DVMS System
- DVMS Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- DVMS Overlay Model – What is an Overlay Model
- DVMS MVC ZX Model – Powers the CPD
- DVMS CPD Model – Powers DVMS Operations
- DVMS 3D Knowledge Model – Powers the DVMS Culture
- DVMS FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved