The Most Prominent Threats Organizations Face in Protecting Cyber Operational Resilience
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Introduction: Operational Resilience and Its Rising Importance
In today’s volatile, uncertain, complex, and ambiguous (VUCA) environment, operational resilience has emerged as a core business imperative. No longer confined to IT systems alone, operational resilience refers to an organization’s capacity to prepare for, withstand, recover from, and adapt to adverse conditions, disruptions, and threats. Cybersecurity sits at the heart of this capability. However, protecting operational resilience is increasingly complex due to an evolving threat landscape that combines technical, human, cultural, and systemic vulnerabilities. This essay explores organizations’ most prominent threats when safeguarding operational resilience, drawing insights from the DVMS Institute NIST Cybersecurity Framework (CSF) Digital Value Management System (DVMS).
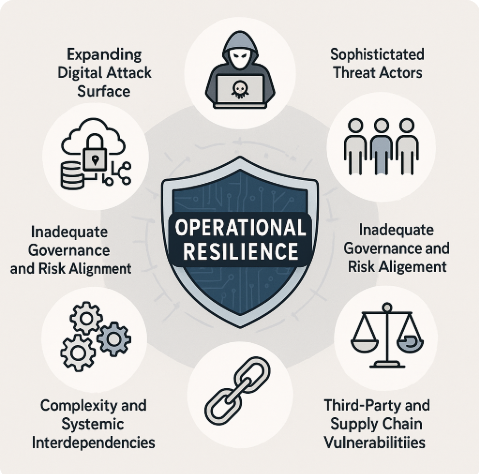
Expanding Digital Attack Surface
One of the foremost threats is the continually expanding digital attack surface. As organizations adopt cloud computing, IoT devices, artificial intelligence, interconnected supply chains, and SaaS based digital business systems, digital entry points increase dramatically. Each new service, device, or system introduces new vulnerabilities, often without corresponding improvements in security posture.
Organizations often fail to recognize that value and risk increase together; anything of value is inherently a target. The threat landscape is no longer confined to technical systems—it now spans people, processes, and third-party ecosystems. For example, attackers have shifted from direct technical exploits to targeting employees or exploiting soft targets in the supply chain.
Sophisticated and Adaptive Threat Actors
Cyber attackers are more organized and better funded than ever. Nation-states, criminal syndicates, and hacktivists employ sophisticated tools like artificial intelligence and zero-day exploits. Advanced persistent threats (APTs) can remain undetected for months, quietly exfiltrating sensitive data or planting logic bombs to be triggered later.
Threat actors also experiment and learn continuously. A notable example involves hackers combining exfiltrated résumé data from job boards with onboarding timelines from public websites to target newly hired employees before they complete cybersecurity training.
Such adversaries are agile and well-informed, often better than the organizations they target, making reactive strategies obsolete and necessitating a proactive, systems-based defense.
Organizational Silos and Weak Cybersecurity Culture
A significant non-technical threat to operational resilience is the organizational culture itself. Critical gaps emerge when cybersecurity is treated as an IT problem rather than a business-wide responsibility. Decision-makers may undervalue or misunderstand cybersecurity risks, leading to underinvestment and fragmented governance.
Cyber resilience requires a cultural transformation where cybersecurity is embedded into the organization’s strategic DNA. Leaders must model behavior, and policies must cascade through every level. All employees must understand their role in protecting digital value. Failing to do this leaves the organization vulnerable to attacks and systemic inertia that hinders response and recovery.
Inadequate Governance and Risk Alignment
Operational resilience depends on aligning cybersecurity with business strategy, yet many organizations still operate with misaligned governance models. According to CSF 2.0, the “Govern” function underpins all other cybersecurity activities. Weak governance structures, unclear responsibilities, and poor communication can hinder timely risk identification and response.
When governance fails to incorporate supply chain risks, geopolitical instability, or internal process flaws, the organization becomes susceptible to systemic failures that could be mitigated. NIST-CSF 2.0 recommends using profiles and tiers to align governance with evolving risk landscapes continuously.
Third-Party and Supply Chain Vulnerabilities
Today’s organizations depend heavily on vendors, cloud services, and supply chains—all of which introduce external risks. A prime example is the SolarWinds breach, where attackers compromised a vendor to gain access to thousands of downstream customers.
Third-party risks are hazardous because they often lie outside the organizational direct control, yet are deeply embedded in daily operations. Without visibility, risk assessments, and contingency plans, a disruption in one supplier can cascade into significant operational impacts across multiple domains.
Complexity and Systemic Interdependencies
Organizations operate as complex adaptive systems composed of interdependent parts. This complexity is both a strength and a threat. Small changes in one part of the system—such as a single misconfigured server or outdated software component—can have outsized ripple effects.
Because these interdependencies often go unnoticed until failure occurs, they make systems brittle and unpredictable. Organizations that fail to apply systems thinking cannot anticipate how disruptions propagate, making them more vulnerable to cascading failures that compromise operational resilience.
Insufficient Detection and Response Capabilities
While preventive controls are necessary, the ability to detect and respond to incidents is vital for resilience. Many organizations still lack real-time monitoring, incident response playbooks, or automated recovery mechanisms.
The NIST CSF 2.0 emphasizes DETECT, RESPOND, and RECOVER as essential components of resilience, not just afterthoughts. When incidents inevitably occur, organizations that fail to build these capabilities face extended downtimes, regulatory penalties, and reputational damage.
Regulatory and Compliance Pressures
Regulatory demands, such as data privacy, operational continuity, or sector-specific mandates, can pressure organizations to meet compliance standards. However, viewing compliance as the goal, rather than a minimum threshold, results in a false sense of security.
Compliance checklists rarely reflect the full scope of risk or the pace of technological change. Organizations that treat regulatory requirements as endpoints rather than baselines are more likely to miss emerging threats and struggle to achieve real operational resilience.
Conclusion: From Cybersecurity to Cyber Resilience
The threats to operational resilience are multifaceted, ranging from technical vulnerabilities and sophisticated attackers to cultural, organizational, and systemic challenges. Organizations must shift from reactive, control-based cybersecurity postures to proactive, adaptive, and governance-driven resilience strategies. Frameworks like NIST CSF 2.0 and overlay models like the DVMS offer blueprints for integrating security into the broader organizational mission.
Ultimately, resilience is not just about surviving disruption but thriving in the face of it. Treating cybersecurity as an enterprise-wide responsibility requires a cultural and strategic shift. Organizations that recognize this and act accordingly will be better prepared to protect their digital value and ensure operational continuity in an age of constant change.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
In today’s digitally driven economy, cyber disruptions are no longer an “if” but a “when.”
The DVMS Institute’s Certified Training Programs teach organizations the skills to build a Holistic and Culture-Aligned Overlay System capable of coordinating Adaptive, Governance, Resilience and Assurance (GRA) actions across a Complex Digital Ecosystem.
Achieving true cyber operational resilience requires seamless alignment between organizational Strategy, Governance, and Operations, underpinned by a culture dedicated to sustaining and continuously innovating the Creation, Protection And Delivery of organizational digital value.

The DVMS positions cyber resilience as a strategic, enterprise-wide capability powered by your best practice systems (NISTCSF, ITSM, GRC etc.) and the DVMS MVC, CPD, and 3D Knowledge models.
This systems-based approach to cyber operational resilience demands active engagement from all members of the Digital Ecosystem. Each member plays a distinct role in proactively identifying and mitigating the systemic risks that threaten digital business operations.
This forward-looking approach to adaptive Governance, Resilience, and Assurance (GRA) positions businesses to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Drive Agility and Trust Across Your Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Explainer Videos
- Architecture Video: David Moskowitz explains the DVMS System
- Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- Overlay Model – What is an Overlay Model
- ZX Model – The MVC’s that power operational resilience
- CPD Model – Adaptable governance and assurance
- 3D Knowledge Model – Enabling holistic organizational learning
- FastTrack Model – A phased approach to cyber resilience
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved