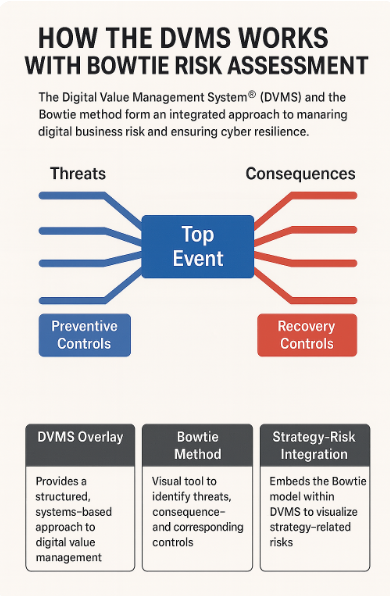
How the DVMS Works with Bowtie Method Risk Assessment
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Introduction: Converging Resilience and Visualization
In today’s complex digital landscape, organizations must protect digital business value while navigating an ever-expanding threat surface. The Digital Value Management System® (DVMS) and the Bowtie risk assessment method complement each other in supporting this challenge. The DVMS provides a strategic and systems-based overlay that enables organizations to create, protect, and deliver digital value. At the same time, the Bowtie method offers a visual and structured way to understand risk paths, controls, and outcomes. They form a holistic, actionable approach to managing digital business risk and ensuring cyber resilience when integrated.
The DVMS as an Overlay: Structure for Continuous Resilience
The DVMS is not a framework or method but an overlay. It maps onto what organizations already do, using a systems-thinking approach to expose performance gaps and structure organizational behavior around seven minimum viable capabilities (MVCs): Govern, Assure, Plan, Design, Change, Execute, and Innovate.
Within this overlay, the DVMS supports an enterprise-wide view of risk that incorporates culture, strategy, and accountability. It enables resilience by supporting organizations as complex adaptive systems (CAS), recognizing that value creation and protection must occur concurrently. This concurrent approach aligns perfectly with the Bowtie method’s structure: visualizing threats, consequences, and control barriers around a central risk event.
Bowtie Method: Visualizing and Managing Threats
The Bowtie method is a graphical risk analysis tool that depicts the pathway from a hazard through preventive and mitigative barriers to outcomes. At its core is a “top event” representing a potential loss or disruption, with threats on the left and consequences on the right. Preventive controls aim to stop the event from occurring, while recovery controls aim to minimize its impact once it happens.
This approach aligns well with the NIST CSF Functions—especially PROTECT, DETECT, RESPOND, and RECOVER—and helps organizations see where controls are missing or weak.
Integrating the Bowtie Model into the DVMS CPD Model
The DVMS CPD Model—Create, Protect, Deliver—is a dynamic representation of digital value flow through an organization. When you overlay the Bowtie method onto this model, you gain:
- Create Phase: Identify what digital value is generated and where potential threats originate. Here, Bowtie threat pathways help define where strategic risks could materialize.
- Protect Phase: Bowtie’s preventive barriers align with the DVMS practice areas of Plan, Design, and Change. These barriers represent technical and organizational controls meant to prevent a top event.
- Deliver Phase: The consequence and recovery side of the Bowtie integrates with DVMS’s Assure and Execute capabilities, ensuring that responses and recovery strategies are in place to maintain stakeholder trust and operational integrity.
This integration transforms traditional risk assessments’ static nature into a dynamic learning loop guided by systems thinking and cultural adaptation.
Strategy-Risk and the Central “Top Event”
In the DVMS, “strategy-risk” is a central concept that positions risk as an inseparable aspect of strategy. The Bowtie “top event” becomes a practical representation of strategy-risk within a particular system or value stream. Using Bowtie, the DVMS overlay can model what happens when a strategic goal is threatened, whether through a cyberattack, system failure, or cultural breakdown.
For example, if the top event is “Data Exfiltration,” the Bowtie method allows DVMS risk teams to map upstream causes (e.g., phishing, misconfigurations) and downstream consequences (e.g., reputational harm, regulatory fines), enabling governance, assurance, and design teams to assign responsibility for barriers across the DVMS MVCs.
Operationalizing the Model with Praxis and FastTrack
The DVMS FastTrack approach provides an iterative, phased implementation plan (Initiate, Basic Hygiene, Expand, Innovate) that fits naturally with the Bowtie model. For example:
- Phase 0: Initiate – Use Bowtie to visualize high-risk areas and align governance structures accordingly.
- Phase 1: Basic Hygiene – Identify critical “top events” and ensure basic preventive controls exist.
- Phase 2: Expand – Refine detection and recovery mechanisms linked to identified consequence paths.
- Phase 3: Innovate – Use Bowtie analytics to drive continuous innovation in threat modeling and risk-informed decision-making.
Similarly, the Praxis approach used by the DVMS for building high-performance teams ensures that risk modeling, threat assessment, and mitigation are embedded in team workflows and learning culture.
Cultural and Behavioral Adaptation
Perhaps the most powerful convergence between the DVMS and Bowtie is cultural. The DVMS recognizes that behaviors and beliefs—mental models—drive how risks are understood and addressed. Bowtie diagrams visually reinforce these relationships, making abstract concepts concrete and shareable across the organization.
As DVMS leaders model questioning and transparency, Bowtie visuals support a culture of curiosity, accountability, and systemic thinking—vital for identifying latent conditions and preventing system failures.
Conclusion: Seeing the Whole, Not Just the Risk
Integrating the Bowtie method within the DVMS overlay system enables organizations to “see the whole” by visualizing, structuring, and managing digital business risks in alignment with strategic outcomes. While the DVMS provides the governance, cultural scaffolding, and minimum viable capabilities, Bowtie gives teams a transparent and collaborative tool to engage with risk dynamically. Together, they transform cybersecurity from a technical silo into a business-aligned, resilience-driven endeavor, achieving not just protection but sustainable value creation.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
In today’s digitally driven economy, cyber disruptions are no longer an “if” but a “when.”
The DVMS Institute’s Certified Training Programs teach organizations the skills to build a Holistic and Culture-Aligned Overlay System capable of coordinating Adaptive, Governance, Resilience, and Assurance actions across a Complex Digital Ecosystem.
Achieving true cyber resilience across a complex digital ecosystem requires seamless alignment between organizational Strategy, Governance, and Operations, underpinned by a culture dedicated to sustaining and continuously innovating organizational digital value.

The DVMS positions cyber resilience as a strategic, enterprise-wide capability powered by the Institute’s CPD, Z-X, and 3D Knowledge models.
This systems-based approach to cyber operational resilience demands active engagement from all members of the Digital Ecosystem, with each member playing a distinct role in proactively identifying and mitigating the systemic risks that threaten digital business operations.
This adaptive, forward-looking approach to Governance, Resilience, and Assurance (GRA) positions businesses to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Drive Agility and Trust Across Your Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Explainer Videos
- Architecture Video: David Moskowitz explains the DVMS System
- Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- Overlay Model – What is an Overlay Model
- ZX Model – The MVC’s that power operational resilience
- CPD Model – Adaptable governance and assurance
- 3D Knowledge Model – Enabling holistic organizational learning
- FastTrack Model – A phased approach to cyber resilience
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved