Navigating the Chaotic World of Multi-Vendor Digital Services
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Strategic Imperative in a Multi-Vendor Era
An unprecedented level of complexity shapes today’s digital business environment. Organizations adopting multi-vendor IT architectures to accelerate innovation and scale operations also inherit a tangled web of integration, governance, and cyber risk challenges. The pressure is on for IT, Cybersecurity, and Risk leaders to manage a sprawling ecosystem of vendors, technologies, and regulations without compromising resilience or trust.
This reality marks a critical inflection point. The shift toward highly distributed digital services is no longer simply a trend—it’s a defining feature of modern organizations’ operations. But with every vendor and every API, the attack surface expands. The result is a high-stakes environment where agility and exposure coexist in tension.
The Internet of Everything—and Its Security Implications
The foundation of this complexity is the explosive growth of interconnected devices, commonly referred to as the Internet of Things (IoT). From smart city infrastructure to personal wearables and industrial sensors, the digital estate now comprises billions of endpoints continuously generating, consuming, and transmitting data.
Every device represents a node in a digital mesh, and each node is a potential attack vector. This mesh is not static—it evolves continuously, dynamically changing the network’s topology. For IT leaders, the implications are profound: the boundaries of the enterprise are now fluid, and securing this amorphous edge requires strategies that are adaptive, predictive, and resilient.
Moreover, the scale and variability of data—its volume, velocity, and variety—compound the challenge. Cybersecurity teams are expected to safeguard an environment where data is both the lifeblood of innovation and a high-value target for attackers. This duality demands a new paradigm for threat detection and data governance: real-time, intelligence-driven, and operationally embedded.
Multi-Cloud and Hybrid IT: The Double-Edged Sword of Agility
The move to multi-cloud and hybrid IT architectures offers organizations unparalleled flexibility and scalability. However, it also introduces complexity that can quickly outpace an organization’s ability to manage risk. Each cloud platform—AWS, Azure, GCP, or private clouds—has its own control frameworks, tooling, and compliance obligations.
This fragmented infrastructure landscape creates several key challenges:
- Visibility and Control – Tracking data movement, enforcing policies, and detecting anomalies across multiple environments is nearly impossible without centralized visibility.
- Integration Overload – With hundreds of APIs and middleware connectors facilitating communication between systems, the attack surface expands dramatically, and vulnerabilities multiply.
- Compliance Fragmentation – Legal and regulatory mandates vary across jurisdictions and data types, making unified compliance governance a constant uphill battle.
The role of IT and Cybersecurity leaders here is strategic: enabling innovation without sacrificing control. Success depends on architecting security as an integral infrastructure layer, not an afterthought. This includes adopting cloud-native security tooling, ensuring end-to-end observability, and embedding compliance into DevOps pipelines.
Microservices: Agility at the Cost of Complexity
The shift to microservices and containerized applications has transformed how software is built and deployed. Gone are the days of monolithic applications. In their place: a constellation of microservices, each independently developed and deployed, often in different programming languages and environments.
This architectural model allows for rapid iteration and scalability. But it also introduces challenges that IT and security teams must reckon with:
- Dependency Management – Each microservice depends on others. If one fails or is compromised, the ripple effect can be immediate and catastrophic.
- Security Sprawl – With more components comes more potential vulnerabilities. Securing containers, APIs, and inter-service communications requires both automation and discipline.
- Operational Blind Spots – Observability becomes more difficult. Tracking logs, monitoring performance, and diagnosing faults across a distributed mesh demands advanced tooling and cross-functional collaboration.
In this environment, security must “shift left”—directly into the development lifecycle. DevSecOps is no longer optional; it is the only sustainable path forward for organizations operating at the pace of digital business.
Evolving Threats and Advanced Adversaries
If infrastructure complexity weren’t enough, the threat landscape would grow more dynamic and dangerous. Advanced Persistent Threats (APTs), ransomware syndicates, and nation-state actors use increasingly sophisticated techniques to infiltrate and exploit enterprise environments.
Unlike opportunistic attacks, these threats are:
- Targeted – APTs often focus on high-value organizations or assets, employing tailored tactics to gain long-term access.
- Stealthy – Many go undetected for weeks or months, exfiltrating data or preparing for destructive actions.
- Innovative – Attackers leverage artificial intelligence, automation, and polymorphic malware to outpace traditional defenses.
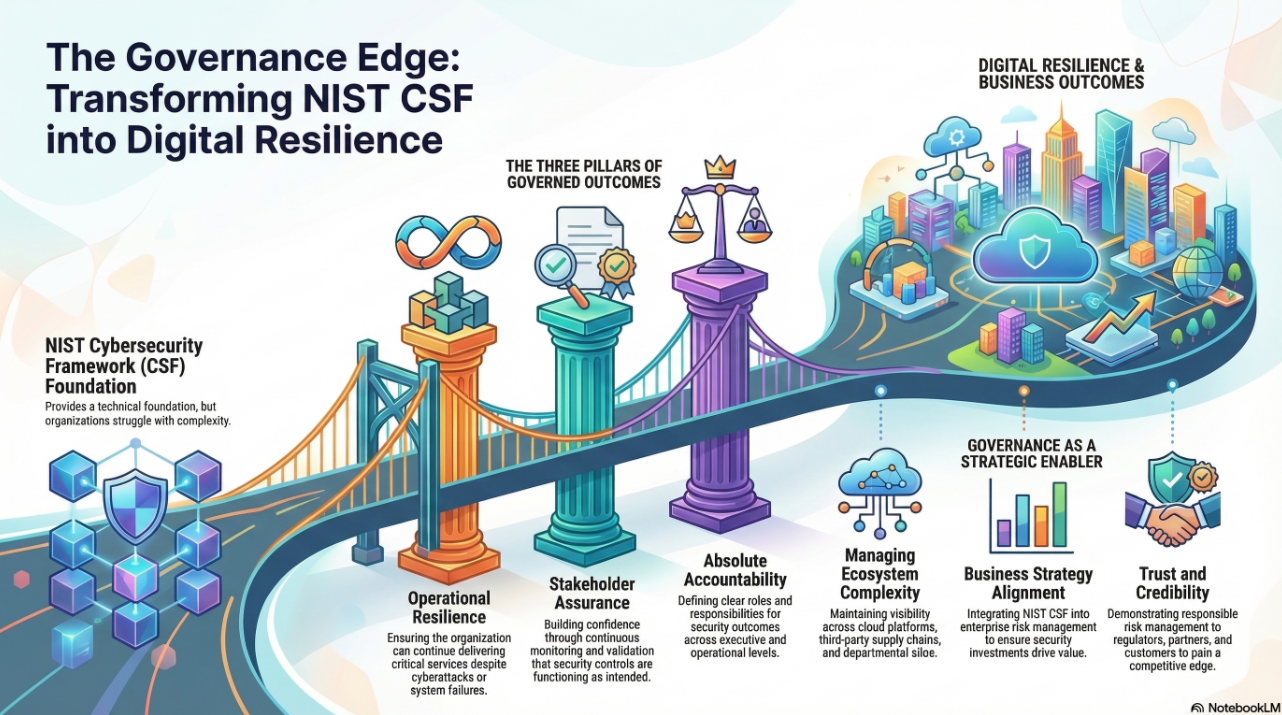
The takeaway for CISOs and cyber risk leaders is clear: legacy security models centered around perimeter defense and static detection are obsolete. The future lies in adaptive, behavior-based security architectures—augmented by threat intelligence and machine learning. Security teams must become more proactive, leveraging analytics to predict threats and orchestrate responses at machine speed.
Regulatory Complexity: Compliance as a Strategic Capability
Another defining challenge is the proliferation of global data protection and cybersecurity regulations. From GDPR and CCPA to HIPAA and PCI DSS, the regulatory burden is growing. Organizations must manage compliance across an expanding matrix of laws, often with overlapping and conflicting mandates.
Key considerations include:
- Data Sovereignty – Knowing where data resides, how it’s accessed, and who controls it is essential for legal compliance and audit readiness.
- Cross-Border Complexity – Regulations vary widely by jurisdiction. Multinational enterprises must implement policy engines and governance frameworks that accommodate regional nuance.
- Operational Overhead – Compliance is costly. Without automation, it drains resources and slows innovation.
For CIOs and CCOs, the challenge is transforming compliance from a reactive burden into a strategic asset. This means automating evidence collection, adopting compliance-as-code, and aligning compliance programs with business goals to enable faster, safer innovation.
Leadership Imperatives in the Face of Complexity
IT, Cybersecurity, and Cyber Risk leaders must embrace new operating models. Complexity is not going away—it is the new normal. Success in this environment requires:
- End-to-End Visibility – Achieving unified telemetry across vendors, clouds, endpoints, and users is foundational to effective risk management.
- Zero-trust architectures – By default, Trust no user, device, or application. Continuously verify and monitor access across the ecosystem.
- Vendor Governance – Multi-vendor environments demand mature third-party risk management. This includes contractual security requirements, regular assessments, and shared incident response plans.
- Workforce Alignment – The human element remains critical. Building cross-functional teams that blend IT, security, and compliance expertise ensures shared accountability and faster response.
- Board-Level Engagement – Complexity, resilience, and cyber risk must be elevated to the boardroom. Executive leaders need to treat cybersecurity as a business enabler, not a technical silo.
Conclusion: A Call to Modernize, Govern, and become Resilient to Disruption
In this world of multi-vendor driven digital services, complexity is both the cost of innovation and the source of existential risk. Now is the time to modernize security, re-architect for resilience, and align digital transformation with enterprise risk objectives.
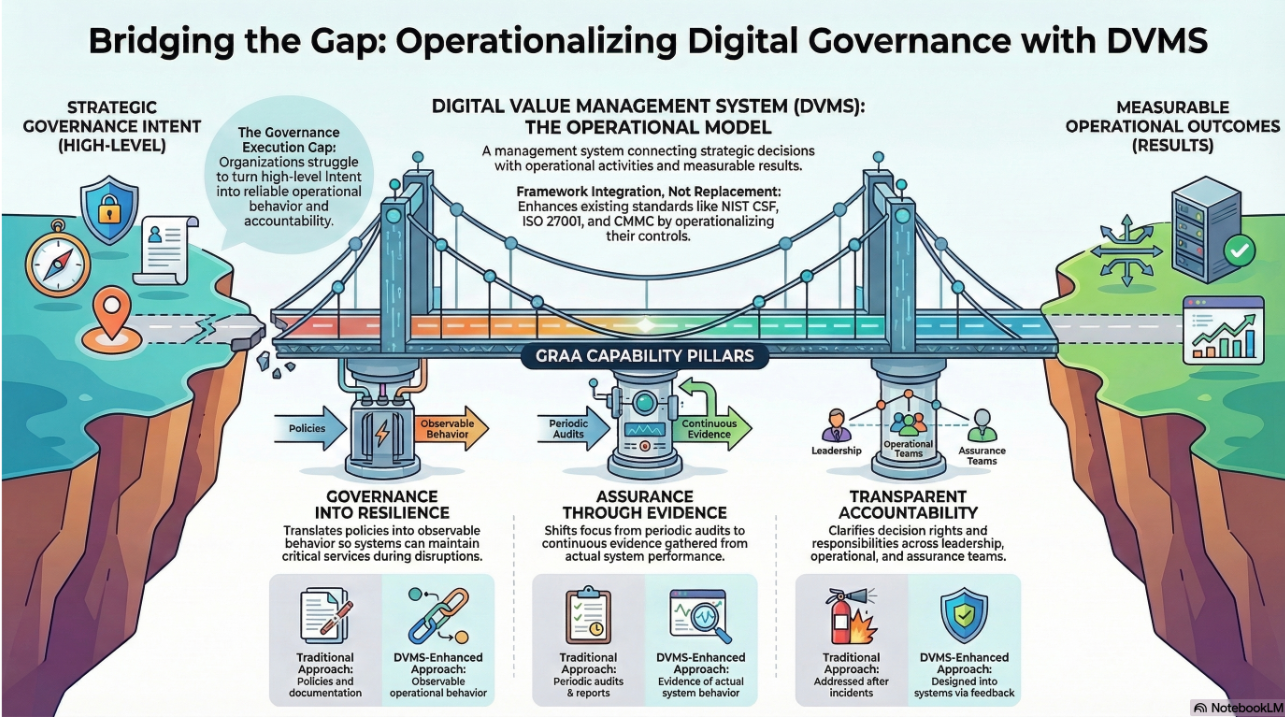
Executive leadership and its board must meet this challenge with a clear strategy on building true cyber resilience by aligning the organizations Strategy, Governance, and Operations business layers with a culture committed to sustaining and continually innovating digital business operations performance
This adaptive, forward-looking approach to Governance, Resilience, and Assurance (GRA) positions businesses to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Drive Agility and Trust Across Your Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
In today’s digitally driven economy, cyber disruptions are no longer an “if” but a “when.”
The DVMS Institute’s NIST-CSF-DVMS Certified Training Programs teach organizations the skills to build and operate a Holistic, Adaptive, and Culture Aligned System capable of coordinating Cyber Operational Resilience actions across a Complex Digital Ecosystem.
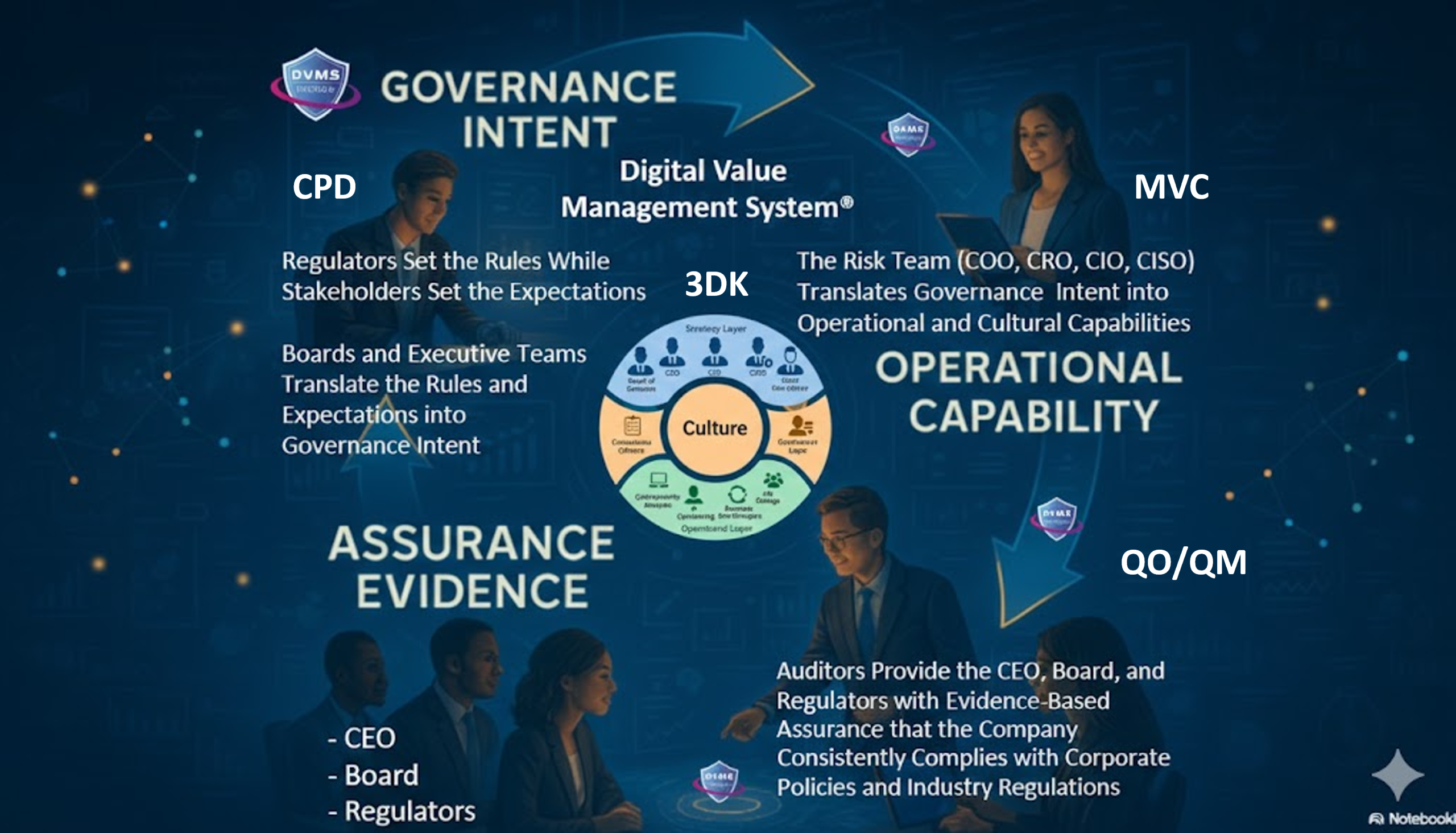
True cyber resilience requires the seamless alignment of organizational Strategy, Governance, and Operations supported by a culture committed to sustaining and continually innovating digital business operations performance.

The DVMS positions cyber resilience as a strategic, enterprise-wide capability powered by the Institute’s CPD, Z-X, and 3D Knowledge models.
This systems-based approach to cyber operational resilience requires engagement from all Employees and Partners, each playing a distinct role in proactively identifying and mitigating the systemic risks that threaten digital business operations.
This adaptive, forward-looking approach to Governance, Resilience, and Assurance (GRA) positions businesses to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Drive Agility and Trust Across Your Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage
DVMS Explainer Videos
- Architecture Video: David Moskowitz explains the DVMS System
- Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- Overlay Model – What is an Overlay Model
- ZX Model – The MVC’s that power operational resilience
- CPD Model – Adaptable governance and assurance
- 3D Knowledge Model – Enabling holistic organizational learning
- FastTrack Model – A phased approach to cyber resilience
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2025 All Rights Reserved