How a Digital Value Management Overlay System Enables Adaptive Cyber Resilience
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
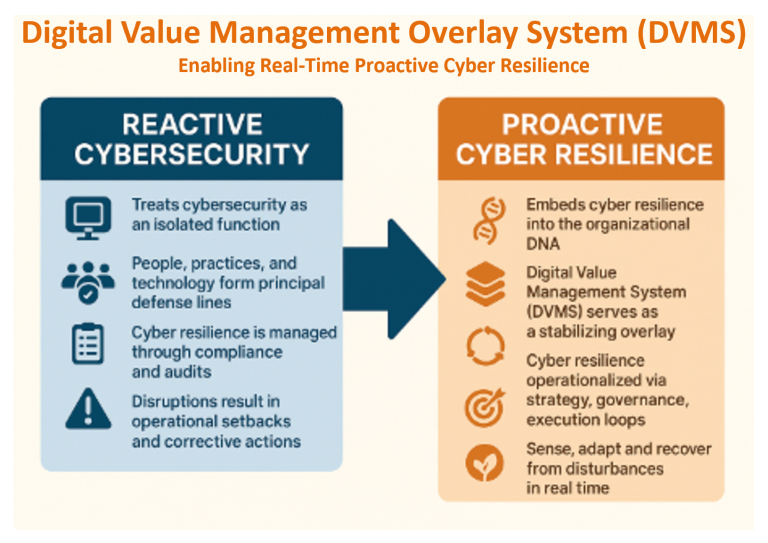
When the first three lines of cyber defense—people, practice, and technology—fail, the Digital Value Management System (DVMS), working in partnership with the NIST Cybersecurity Framework (CSF) and other existing digital best practice frameworks and systems, emerges as the indispensable mechanism that saves the day. Unlike traditional approaches that compartmentalize cybersecurity as a technical function, the DVMS embeds cyber resilience within the organizational DNA. It ensures that cybersecurity is not an isolated department but an intrinsic element of the entire value creation, protection, and delivery system. This article explores how the DVMS, with its layered architecture and principle-based strategy-risk approach, operationalizes cyber resilience when conventional defenses falter.
Understanding Failure Across the First Three Lines
Modern cyber threats are increasingly capable of bypassing initial defenses. The “first line” of people fails when phishing attacks deceive employees or when insider threats exploit access privileges. The “second line,” organizational practices, often fail due to outdated policies, misaligned compliance strategies, or an inadequate understanding of how governance should evolve alongside emerging threats. The “third line,” technology, is breached when systems are misconfigured, unpatched, or inherently vulnerable. Traditional defense-in-depth approaches assume that these layers are sufficient. Yet, real-world incidents such as the SolarWinds breach, Target’s vendor portal compromise, and Marks & Spencer in the UK have demonstrated how systemic failure can and does occur.
At this point, when attackers have infiltrated systems, outmaneuvered controls, and exposed organizational blind spots, the question isn’t “How do we prevent this?” but rather “How do we ensure the organization survives and recovers?” This is where the DVMS becomes essential.
The DVMS: A Systems Overlay for Cyber Resilience
The DVMS is not a framework or a standalone method—it is a scalable overlay that integrates and stabilizes existing organizational capabilities. It operates through three interconnected layers:
- DVMS Layer (Top): This represents what the organization already does—its current frameworks, standards, processes, and systems. This black box becomes the starting point for assessing organizational maturity and identifying stabilization needs.
- Z-X Model (Middle): This is the heart of the DVMS, composed of seven Minimum Viable Capabilities (MVCs): Govern, Assure, Plan, Design, Change, Execute, and Innovate. These universal capabilities ensure organizations can operate cohesively, adapt to threats, and build feedback mechanisms.
- CPD Model (Bottom): CPD stands for Create, Protect, and Deliver. This layer captures the entire lifecycle of digital business value and is where cyber resilience becomes measurable. The CPD Model operationalizes the Z-X Model, linking strategy and governance to execution and assurance.
By implementing this layered approach, organizations no longer depend solely on the front lines of defense. Instead, they cultivate a resilient system capable of absorbing, adapting to, and recovering from attacks.
From Reactive Defense to Proactive Strategy-Risk
At the core of the DVMS is a shift in mindset—from viewing cybersecurity as reactive defense to integrating it into “strategy-risk,” a fused concept where strategy and risk are inseparable. When attackers breach the perimeter, organizations guided by the DVMS don’t scramble for answers—they refer to pre-established governance loops, assurance controls, and adaptive execution plans.
This strategic integration is crucial. It ensures that risk assessments are not one-off compliance activities but continuous inputs into decision-making. For example, in the Strategy/Governance Loop, a board may define cyber-resilience metrics that feed directly into design and innovation efforts. Through the Governance/Assurance Loop, these directives are continually tested and refined based on real-world feedback and audit results.
Cybersecurity as a By-product of Digital Business Resilience
One of the most powerful aspects of the DVMS is that cybersecurity is not treated as the goal; it is the by-product of a well-run, value-focused organization. The real goal is cyber resilience—the ability to continue delivering value in the face of disruption. The CPD Model frames this resilience by creating structured loops of Governance/Execution, Governance/Assurance, and Strategy/Governance. These loops ensure that no part of the system operates in isolation, allowing the organization to “sense and respond” in real time.
If a ransomware attack disables operations, the DVMS enables the organization to assess which value streams are affected (via Identify), reconfigure operations to protect other assets (via Protect), detect the scope of the compromise (via Detect), initiate pre-tested response playbooks (via Respond), and implement recovery workflows (via Recover). Each NIST CSF 2.0 function finds a practical home in the DVMS loops, often turning a chaotic scramble into a guided, systemic response.
Organizational Culture: The Hidden Backbone
Culture is a critical enabler in this transformation. Many security incidents escalate not because of technological failure, but due to cultural shortcomings—fear of reporting, siloed communication, or lack of trust. The DVMS addresses this head-on by emphasizing a “generative” culture, where transparency, psychological safety, and continual learning are normalized. This cultural shift ensures that feedback loops don’t stop at department walls but circulate across teams, enhancing collective resilience.
When the first three lines fail, an organization with a deeply embedded DVMS doesn’t implode—it adapts. Employees are empowered to surface anomalies, teams coordinate across silos, and executives lead from a position of informed confidence rather than reactive panic.
Case-Based Resilience: DVMS in Action
Consider a scenario where a supply chain attack hits a multinational financial services firm. The initial entry vector was a compromised third-party integration, undetected by the traditional three lines. Thanks to the DVMS:
- The Governance/Execution Loop already incorporates real-time third-party risk scoring and contractual obligations for incident reporting.
- The CPD Model traced the value chain impacted by the attack, prioritizing business services based on criticality.
- The Governance/Assurance Loop surfaced gaps in vendor compliance and initiated control redesign.
- The Strategy/Governance Loop quickly reviewed long-term implications and adjusted sourcing strategies.
This wasn’t just about surviving an incident—it was about using the incident as a lever to increase future resilience, demonstrating why the DVMS is not a reactive framework, but a proactive system for thriving amid chaos.
Conclusion: The DVMS Saves the Day—Every Day
When traditional defenses fail—and they inevitably will—the DVMS saves the day by ensuring that resilience is not a last resort but a built-in capability. By aligning digital business strategy with risk, embedding cybersecurity into organizational loops, and cultivating an adaptive culture, the DVMS offers more than incident response. It delivers strategic confidence, operational integrity, and ultimately, protected value creation. In a world where “if” has been replaced by “when,” the DVMS doesn’t merely react to breaches—it transforms them into catalysts for stronger, more innovative, and more secure digital enterprises.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
The DVMS Institute’s NIST Cybersecurity Framework Digital Value Management System® certified training programs teach Internal or 3rd Party Digital Service Providers the skills to build a Holistic, Adaptive, and Culture-Powered Overlay System for Cyber Operational Resilience.
The NIST-CSF-DVMS positions cyber resilience not as a technical function but a strategic, enterprise-wide capability that mandates engagement from top Leadership to Frontline Employees, trained to proactively identify, classify, and mitigate the systemic cyber risks that impact cyber business operations.
Enabling organizational resilience requires a coordinated effort across an organization’s Strategy, Governance, and Operational business layers. When each layer is aligned and operating cohesively as an integrated system, service providers can proactively protect their cyber assets and ensure the continuity of cyber business operations.
This unique and innovative approach to Adaptive Governance, Resilience, and Assurance (GRA) also enables service providers to comply with any government-mandated cyber regulation (SEC, DORA, NIS2 etc.) or maturity model program (SCF, HITRUST, CMMC etc.).
® DVMS Institute 2025 All Rights Reserved