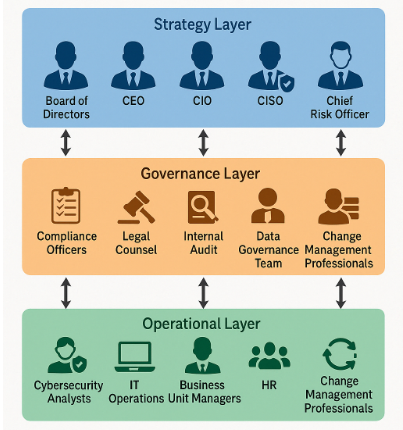
The People That Power The Strategy, Governance, Operations and Cultural Layers of a DVMS Program
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Delivering the outcomes of the NIST Cybersecurity Framework (CSF) integrated with the Digital Value Management System® (DVMS) requires coordinated action across an enterprise’s strategy, governance, and operational layers.
Each of these layers contains unique roles that, when aligned and functioning cohesively, enable the organization to protect digital assets and adaptively manage digital business risks while delivering sustained digital value and resilience.
The DVMS positions cyber resilience not as a technical function but as a strategic, enterprise-wide responsibility. This systems-based approach, which includes the CPD Model (Create, Protect, Deliver) and the Z-X Capability Model (Govern, Assure, Plan, Design, Execute, Change, Innovate), mandates engagement from top executives to frontline implementers, each fulfilling distinct responsibilities.
Strategy Layer: Shaping Vision and Direction
At the strategic layer, the key roles are those of executive leadership and the board of directors. These actors are responsible for setting the vision and strategic intent for the organization’s cybersecurity posture and ensuring that cybersecurity is framed as a business issue, not merely a technology concern.
The Chief Executive Officer (CEO) and Chief Operating Officer (COO) are essential in ensuring digital business value is created and protected as a concurrent activity, not as sequential steps. This concept is central to the DVMS philosophy, where unprotected value is considered to have no sustainable worth.
As the highest form of strategic oversight, the board of directors holds ultimate accountability for embedding cybersecurity risk into the organizational enterprise risk management (ERM) program. They are responsible for setting risk tolerance thresholds and ensuring the organization defines its “strategy-risk” profile. This DVMS concept treats strategy and risk as inseparable components of value creation. The board must authorize and fund the resources needed to adopt and adapt the NIST CSF and support DVMS as a scalable overlay across the organization.
Another critical role at this layer is that of the Chief Information Security Officer (CISO)—the CISO bridges high-level business strategy and the governance and operational processes that bring cybersecurity to life. At the strategic level, the CISO participates in board-level discussions, articulates the cyber risk landscape, and ensures that digital value protection is aligned with the organization’s goals. The CISO is also a key contributor to the organizational Target Profile and cybersecurity maturity journey using the CSF’s tiered model.
Equally important is the Chief Risk Officer (CRO) or the equivalent Enterprise Risk Manager, who oversees how digital risk integrates with other forms of enterprise risk, such as financial, operational, reputational, and compliance risk. This individual supports the framing of risk in strategic terms and helps ensure the use of the CSF and DVMS to shape decisions at the highest levels of the organization. These roles must ensure that cybersecurity becomes a fundamental component of the organizational mission and strategic plan, not merely a line item or technical initiative.
Governance Layer: Translating Strategy into Control and Accountability
The governance layer transforms strategic direction into policies, standards, oversight structures, and performance measurement systems. It ensures that the organizational environment can achieve the intended CSF and DVMS outcomes. The DVMS Z-X Model identifies core capabilities at this layer, particularly “Govern,” “Assure,” and “Plan.
The Chief Governance Officer, or a designated senior governance lead, is typically responsible for policy development, ensuring that all cybersecurity-related governance aligns with the broader business governance framework. This includes the cascade of policies that define how work is conducted across the enterprise, from executive mandates to operational protocols. This role works closely with the CISO and other leaders to craft a governance system that aligns with the CSF’s GOVERN Function and supports the continuous improvement expectations of the DVMS FastTrack phases.
Compliance officers and legal counsel also play vital roles in this layer. They ensure the organizational cybersecurity policies meet legal and regulatory requirements, such as SEC, NIS2, DORA, SOCI, SAMA, IMO, GDPR, HIPAA, and other sector-specific mandates (HITRUST, CMMC). These individuals are instrumental in mapping CSF outcomes and DVMS practice areas to external compliance obligations. They also manage risk mitigation strategies around contractual obligations, third-party relationships, and incident response liabilities.
Another key role is the Internal Audit Function. Internal auditors verify that the CSF and DVMS processes are followed consistently, accurately, and effectively. They provide independent assurance on the maturity and efficacy of cybersecurity practices across departments and functions. Auditors help inform the organization’s Current Profile under the CSF and support assurance functions within the DVMS by identifying non-conformance or potential risk exposure areas.
The Information and Data Governance Team is also central to governance. These professionals, often including data stewards and architects, ensure that the organization knows what digital assets it owns, where they reside, how they are classified, and how they are protected. Their work directly contributes to CSF IDENTIFY and PROTECT Functions and supports the DVMS capabilities associated with quality, compliance, and data-driven decision-making.
Operational Layer: Execution, Integration, and Continuous Improvement
The operational layer comprises the individuals and teams that execute cybersecurity activities, integrate them into business operations, and drive iterative improvement. These roles turn policies and plans into outcomes that align with both CSF Functions and DVMS practice areas, such as “Execute,” “Design,” “Change,” and “Innovate.”
Cybersecurity analysts, engineers, architects, and IT infrastructure specialists are key actors. These professionals operationalize the CSF’s technical outcomes—monitoring networks, managing identity and access control, maintaining endpoint protection, and ensuring effective detection and response systems. Their actions underpin the CSF’s PROTECT, DETECT, RESPOND, and RECOVER Functions. In the DVMS, these actors contribute to operational excellence and innovation, ensuring systems are designed and operated securely, resiliently, and with value protection.
Business process owners and departmental managers are also essential at the operational layer. As the custodians of daily operations, they must embed cybersecurity into their standard operating procedures. They participate in developing and maintaining Organizational Profiles, articulate operational risks, and ensure that cybersecurity practices do not hinder performance or innovation. Their understanding of business context enables them to make risk-informed decisions aligned with the organization’s strategy.
Human Resources (HR) also plays an operational role, supporting security through training, workforce development, and policy enforcement. HR is critical in cultivating a culture of accountability and cyber awareness. They help onboard security competencies, design behavior-based training programs, and reinforce expectations tied to roles and responsibilities.
Change management professionals, including project and program managers, are crucial for integrating the CSF and DVMS into business transformation efforts. These individuals plan and oversee initiatives that adapt business systems, platforms, and processes to meet security and resilience goals. They support the organization through the DVMS FastTrack phases: Initiate, Basic Hygiene, Expand, and Innovate. Their expertise in coordinating across teams ensures that change is sustainable and that lessons learned inform future efforts.
Finally, external-facing roles—such as procurement officers, vendor managers, and supply chain specialists—apply CSF and DVMS principles to the broader ecosystem. These roles assess third-party risks, enforce contract-level security requirements, and monitor vendor compliance. This is essential to meeting supply chain governance outcomes under CSF and maintaining a secure and trusted digital ecosystem defined by the DVMS.
Cultural Layer: Making the DVMS Work in Practice
Culture is the foundation that makes a Digital Value Management System (DVMS) work in practice. While frameworks, processes, and technologies provide the structure, it is the shared values, behaviors, and mindsets across the organization that determine whether those structures deliver real outcomes.
A culture of collaboration, accountability, and continuous learning enables people to see governance, resilience, and assurance not as compliance checkboxes but as part of how they create and protect digital value every day. By fostering trust, transparency, and adaptability, culture drives alignment between strategy and execution, empowers teams to act with agility in complex digital ecosystems, and embeds the DVMS principles into the organization’s DNA—turning them from “programs” into sustainable, value-driven practices.
Conclusion
To deliver the outcomes of the NIST CSF and the DVMS across an enterprise, roles must be aligned and empowered across the strategy, governance, and operational layers. Strategic leaders provide the vision, governance roles establish policy and assurance, and operational teams bring it all to life.
Together, these roles create an adaptive, risk-informed, and resilient organization capable of thriving in a complex, volatile digital environment. The CSF provides the outcome taxonomy and structure. At the same time, the DVMS offers a systems-based, scalable overlay for organizations to govern, assure, execute, and continually improve the security and value of their digital operations.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
Rick has 40+ years of passion and experience creating solutions to give organizations a competitive edge in their service markets. In 2015, Rick was identified as one of the top five IT Entrepreneurs in the State of Rhode Island by the TECH 10 awards for developing innovative training and mentoring solutions for boards, senior executives, and operational stakeholders.
In today’s digitally driven economy, cyber disruptions are no longer an “if” but a “when.”
The DVMS Institute Certified Training Programs teach organizations how to transform their ITSM, GRC and Cybersecurity programs into an integrated Digital Value Management System® (DVMS) capable of powering adaptive governance, operational resilience, performance assurance, regulatory compliance, and trust across a complex digital supply chain.
The DVMS—driven by its MVC, CPD, 3D Knowledge, and FastTrack models integrates digital Strategy, Governance, Operations, and Culture into a single adaptive overlay system that continually sustains and advances digital business operations and performance.
By adopting a DVMS, organizations are positioned to:
- Maintain Operational Stability Amidst Constant Digital Disruption
- Deliver Digital Value and Trust Across A Digital Ecosystem
- Satisfy Critical Regulatory and Certification Requirements
- Leverage Cyber Resilience as a Competitive Advantage

DVMS Explainer Videos
- Architecture Video: David Moskowitz explains the DVMS System
- Case Study Video: Dr. Joseph Baugh Shares His DVMS Story.
- Overlay Model – What is an Overlay Model
- MVC ZX Model – Powers the CPD
- CPD Model – Powers DVMS Operations
- 3D Knowledge Model – Powers the DVMS Culture
- FastTrack Model – Enables A Phased DVMS Adoption
Digital Value Management System® is a registered trademark of the DVMS Institute LLC.
® DVMS Institute 2024 All Rights Reserved