Why Technology Without a Strategy Fails in Cybersecurity and Cyber Resilience
Rick Lemieux – Co-Founder and Chief Product Officer of the DVMS Institute
Enterprises today face a relentless barrage of cyber threats, many of which exploit not just technical vulnerabilities but strategic and organizational ones. Despite billions spent globally on cybersecurity technologies—firewalls, antivirus software, endpoint detection and response tools, identity and access management systems, and more—many organizations still struggle to effectively reduce their cyber risk posture.
Why? Technology without a coherent, risk-informed strategy is not enough. It becomes a series of tactical fixes in search of a problem rather than an integrated solution aligned with enterprise objectives. Technology without strategy creates the illusion of protection while leaving organizations dangerously exposed.
Cybersecurity is an Enterprise Risk, not a Technical Challenge.
A key insight from the NIST CSF 2.0 and the DVMS Institute’s publications is that cybersecurity is not merely a technical domain. It is fundamentally a business issue rooted in enterprise risk management. As such, decisions about cyber protections must be tightly integrated into organizational strategy—not bolted on as afterthoughts driven by compliance checklists or reactive responses to incidents.
In A Practitioner’s Guide to Adapting the NIST Cybersecurity Framework, the authors argue that treating cybersecurity as an isolated department or siloed function—rather than a cross-functional responsibility guided by strategic goals—is a recipe for failure. Instead, enterprises need to adopt a strategy-risk approach, in which value creation and protection are two sides of the same coin. Risk must be treated not as a separate element from strategy but as an intrinsic part.
The Fallacy of Technology-First Thinking
Organizations that adopt a technology-first approach to cybersecurity often fall into the trap of thinking that more tools equal more protection. But buying tools without a coherent plan is like collecting construction materials without a blueprint. Tools alone do not address the foundational issues of governance, risk prioritization, stakeholder alignment, and cultural awareness.
As Thriving on the Edge of Chaos explains, digital environments are complex adaptive systems. Within such systems, threats are not linear and predictable—they evolve, propagate, and exploit systemic weaknesses, including poor communication, weak governance, and fragmented workflows. A technology-only response is ill-equipped to manage such complexity. Without a strategy, technology becomes noise: an overcomplicated ecosystem of overlapping, underutilized tools that often introduce more risk than they resolve.
Governance as the Anchor
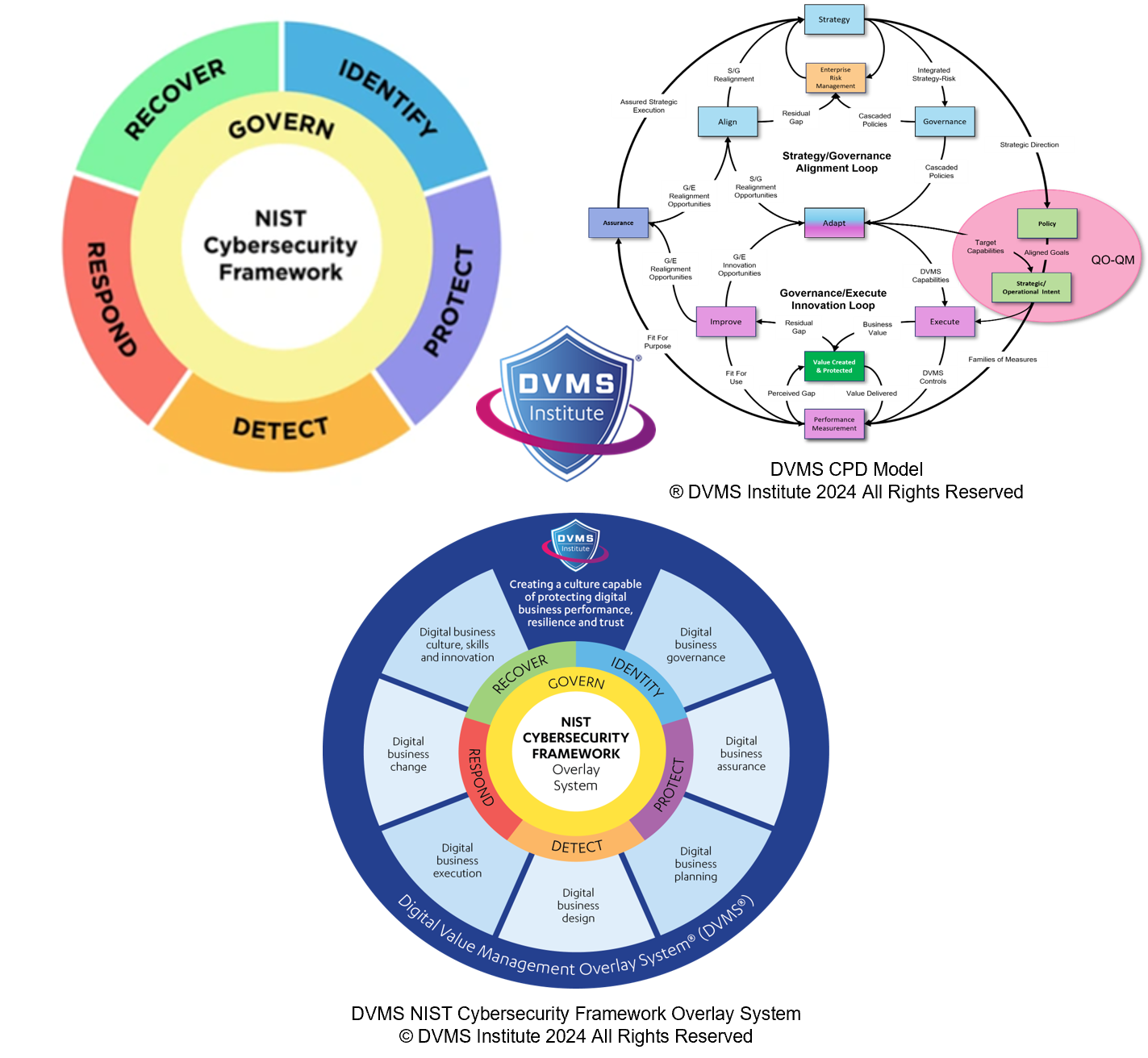
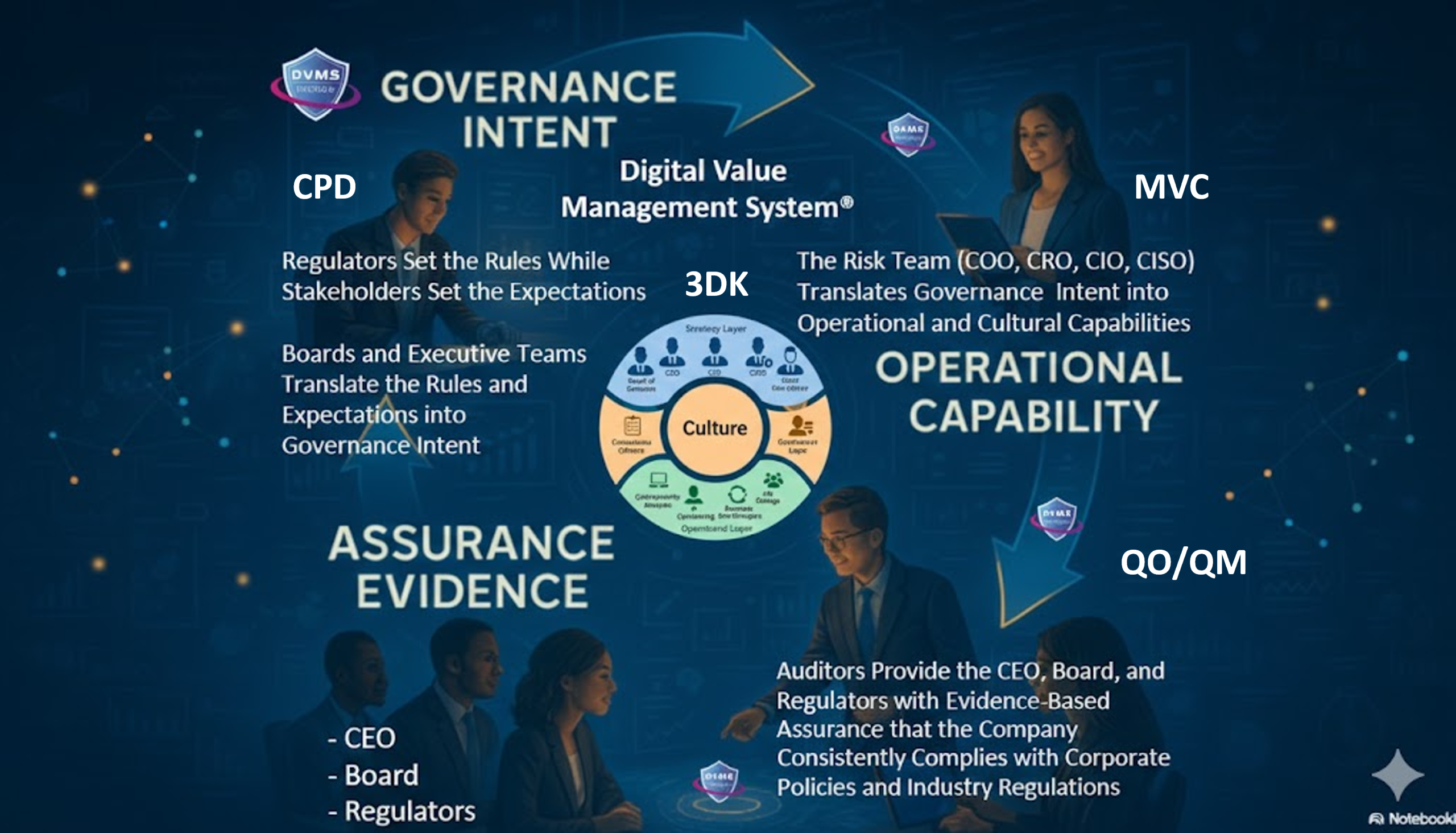
NIST CSF 2.0 introduces Govern (GV) as one of the six core Functions—an explicit acknowledgment that effective cybersecurity must begin with governance. Cybersecurity must be embedded into the organization’s strategic objectives, policies, and culture. The GOVERN Function defines outcomes around establishing and maintaining a cybersecurity risk management strategy, integrating cybersecurity into enterprise risk management, and ensuring that the organization’s policies, roles, and responsibilities support its cybersecurity goals.
This is reinforced by the DVMS CPD Model, which emphasizes the importance of “strategy-risk” and operational resilience. According to this model, organizations must see cybersecurity not as a project to implement or a tool to deploy, but as part of a continuous, systemic process of creating, protecting, and delivering digital business value.
Systems Thinking and Strategy-Risk Integration
The DVMS Institute strongly promotes systems thinking as a core capability in understanding and managing cyber risk. Systems thinking requires organizations to consider how people, processes, technology, and information interact—not in isolation but as parts of an interconnected ecosystem. For example, a sophisticated identity management tool might be ineffective if policies around access rights are not enforced, if users are not trained, or if monitoring data is siloed and unused.
Systems thinking leads naturally to strategy-risk, a term coined by the DVMS authors to describe the inseparable relationship between business strategy and risk management. Organizations must evaluate how digital initiatives (e.g., moving to the cloud, automating customer service) create new value and new risks and how those risks can be addressed holistically—not just by deploying tools but by aligning policies, behaviors, and investments with organizational goals.
The Culture Factor
One of the most potent arguments for strategy over technology comes from the role of organizational culture. The DVMS materials make clear that many breaches stem not from technology failures. Still, from human factors: poor training, misaligned incentives, lack of accountability, or inconsistent leadership engagement12603 DVMS Thriving on …. No tool can overcome a culture that treats cybersecurity as a cost center or views compliance as the endpoint rather than a starting point.
Embedding cybersecurity into organizational culture means defining clear roles and responsibilities, promoting a questioning mindset, and encouraging collaboration across teams. This is supported by NIST CSF’s inclusion of Profiles and Tiers, which help organizations understand their current cybersecurity posture and maturity—and provide a roadmap for continual improvement.
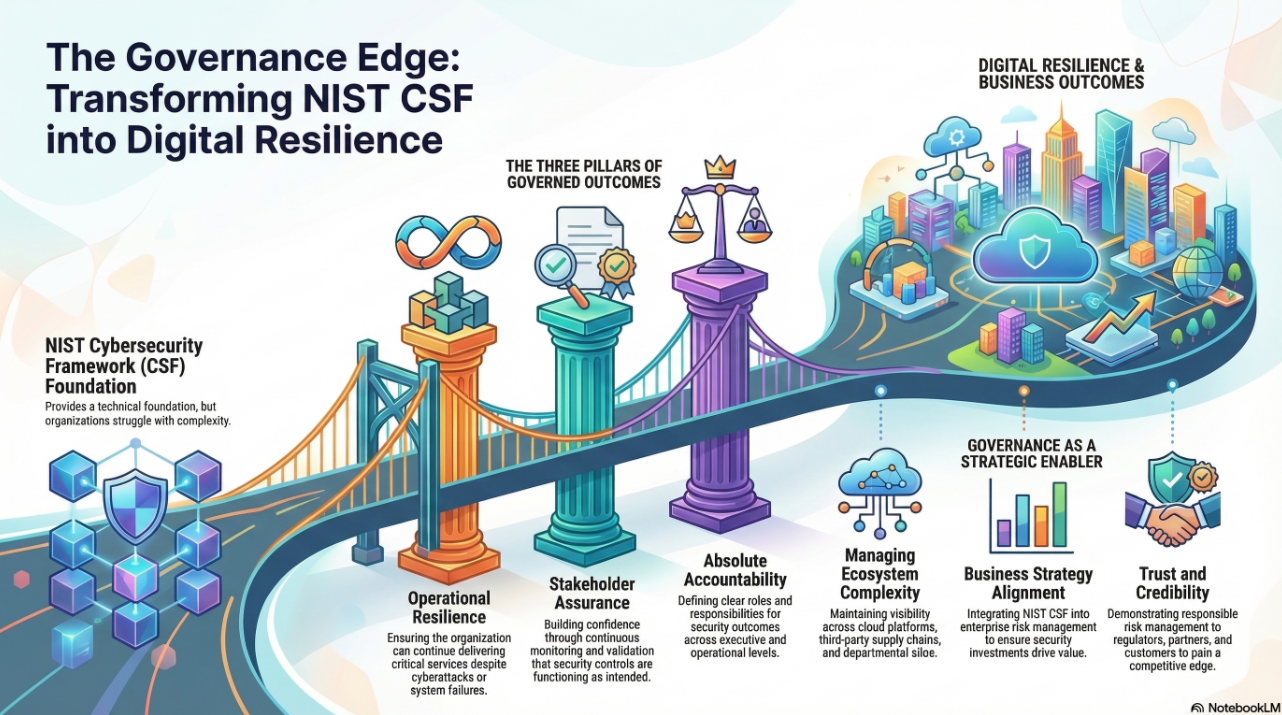
Cyber Resilience as the True Goal
Cybersecurity is not the destination; cyber resilience is. Resilience means the ability to withstand, respond to, and recover from adverse cyber events while continuing to deliver business value. This requires planning, preparation, and governance—all of which come from strategy, not technology alone.
As the DVMS team explains, true resilience is achieved when organizations embed cybersecurity into the design and delivery of value—making protection and creation concurrent rather than sequential. Resilience is not about avoiding all breaches; it’s about minimizing impact, restoring services quickly, and adapting faster than adversaries can evolve.
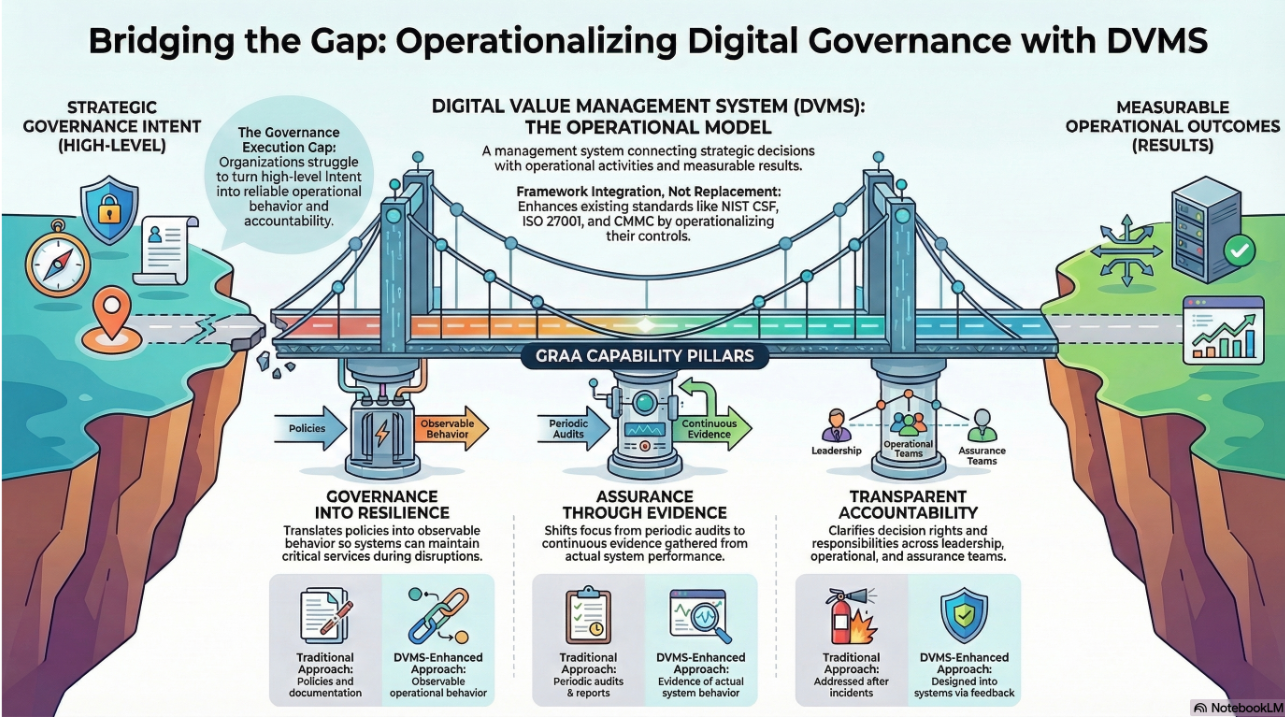
The Strategic Overlay: DVMS and NIST CSF in Practice
The DVMS model does not replace the NIST CSF—it overlays it. This distinction is critical. NIST CSF provides the taxonomy of outcomes (what to achieve), while the DVMS provides a systems-based method (how to build the organizational capabilities needed to achieve those outcomes). Technology selection and deployment must flow from strategic alignment and gap analysis, not vendor hype or panic responses.
Organizations that use the CSF Profiles and Tiers to identify gaps between their current and desired states can then apply the DVMS’s phased FastTrack™ approach to guide iterative improvements—starting with governance and foundational capabilities before investing in advanced technologies.
Conclusion
Technology is essential in the fight against cyber threats—but it is not a silver bullet. Technology becomes expensive clutter without a strategy that aligns with enterprise goals, manages risk intelligently, embeds security into culture, and embraces systems thinking. Together, the NIST CSF and DVMS frameworks clarify that proper cybersecurity and cyber resilience are strategic capabilities, not technical ones. Organizations that understand this will not just survive—they will thrive on the edge of chaos.
About the Author

Rick Lemieux
Co-Founder and Chief Product Officer of the DVMS Institute
DVMS Institute is a renowned provider of accredited (APMG International), Assured (NCSC-GCHQ-UK), and Recognized (DHS-CISA-NICCS-USA) NIST Cybersecurity Framework, Digital Value Management System® body of knowledge publications, certification trainings, assessment platforms and real-life desktop simulation trainings.
The Institute’s NIST Cybersecurity Framework Digital Value Management System® certified training programs teach businesses of any size, scale, or complexity the skills to build a Performance Driven Overlay System for Cyber Resilience capable of anticipating and mitigating the systemic risk digital businesses face today.
By embedding systemic risk management into strategic decision-making and aligning it with employee cultural values, organizations can build resilience—a dynamic capability to withstand digital business disruption and comply with any cybersecurity regulation (SEC, UK, DORA, NIS2, SAMA, SOCI, IMO, etc.) or maturity model mandates (HITRUST, CMMC, C2M2 etc.).
® DVMS Institute 2024 All Rights Reserved